Droppers are in the front line of every cyberattack. They are special files that install malware on your system. And they often take the form of well-known files. Let’s look back at this summer’s statistics.
Dropper, summer statistics
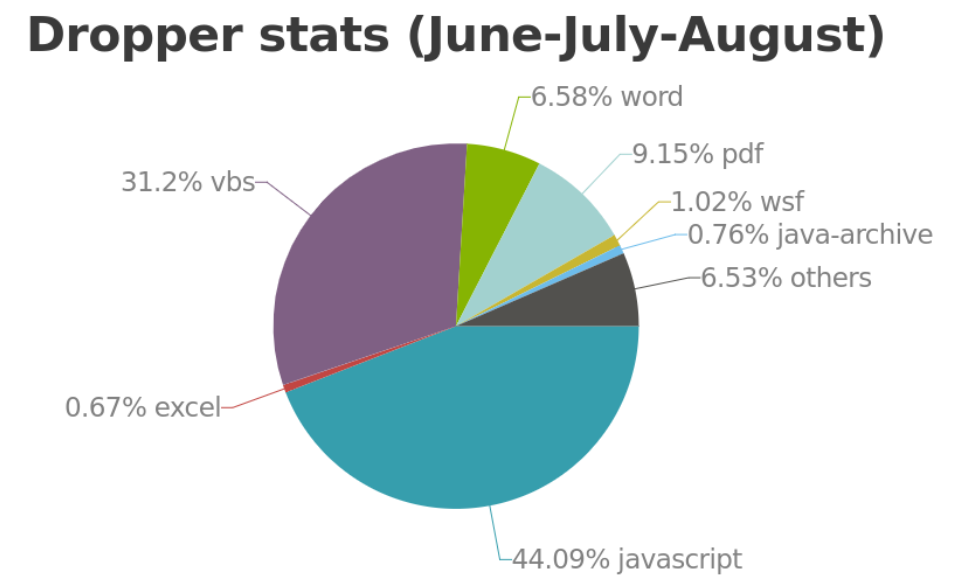
The advantage of knowing what form droppers can take is that your staff can be made more aware of the formats to look out for. Stormshield’s Threat Intelligence team analyzed several thousand droppers during June, July and August 2017. Here is what they found:
The traditional Word and PDF formats are very much present, although not in large numbers, while other formats such as JavaScript and Visual Basic Script (VBS) are much more widely used. It should also be noted that there were very few Excel format files over the months that were analyzed.
But you don't always have to play “Where’s Waldo?” to find and identify these droppers. Implementing certain good practices can be enough to protect you from this type of malware:
- Keep your computer up-to-date (your operating system, software and plug-ins)
- Make regular backups of your most important files
- And above all, don't click on links from unknown sources
Breach Fighter: Big and Smart Data
With the Breach Fighter tool, Stormshield’s Security Intelligence team detects and analyzes malware by examining millions of spams and targeted attacks, and also their droppers. Breach Fighter is built into hundreds of thousands of Stormshield Network Security firewalls deployed worldwide so as to aggregate the largest number of samples. In this way, the Security Intelligence team can establish in real time from which dropper the attacks come.