In May 2016, Softpedia wrote an article about a Drupal web ransomware. This malware exploits an SQL Injection on CMS Drupal, changes admin credentials and asks for bitcoins to unlock content.
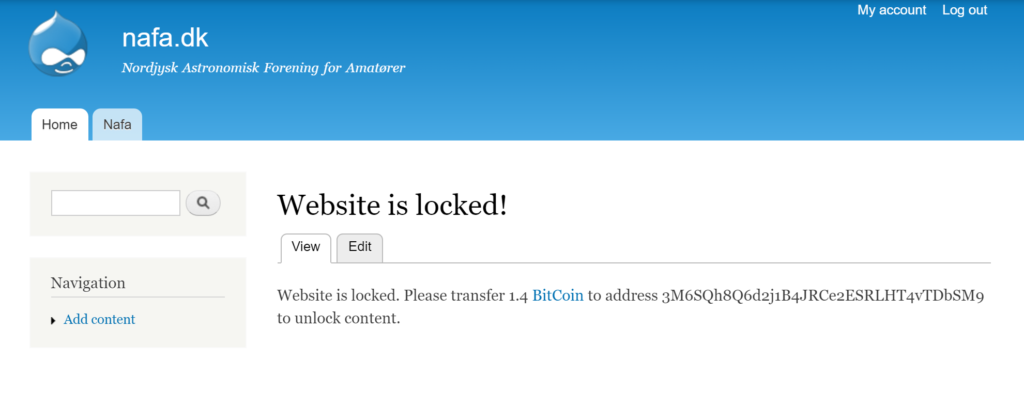 After locking the website, a malware is executed on the server. After this ends, the last uploaded file is a binary file written in the Go programming language, which is the actual ransomware. This Go binary deletes the file upload form and replaces it with the ransom note seen above.
After locking the website, a malware is executed on the server. After this ends, the last uploaded file is a binary file written in the Go programming language, which is the actual ransomware. This Go binary deletes the file upload form and replaces it with the ransom note seen above.
3 months after this article, there was no available sample of this malware on public repositories. So, it’s time to try to find one. We only know that the malware is developed in Go and exploits Drupal vulnerabilities. Thanks to @DlBlind, we also know that it uses P2P to communicate.
Please note that this article is not a reverse of the malware but tries to explain the attack vector and some interesting key features.
Sample Hunting
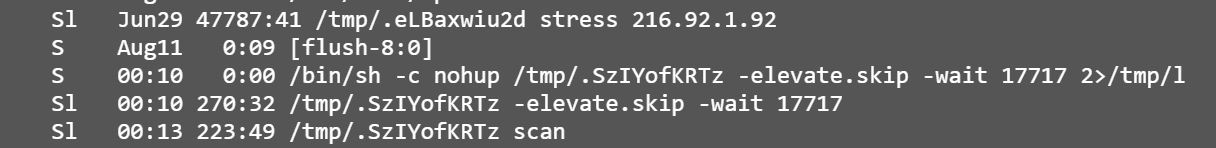
Googling « Website is locked. Please transfer 1.4 BitCoin to address », we can found a lot of hacked Drupal. After a quick look, we retrieved an unknown sample executed as:
where the file “l” is actually a log file looking like:
The above snippet shows that the sample uses P2P communication.
A quick analysis of the sample shows that it is developed in GO and compressed with UPX. As shown below, it is not known by any anti-virus on VT:
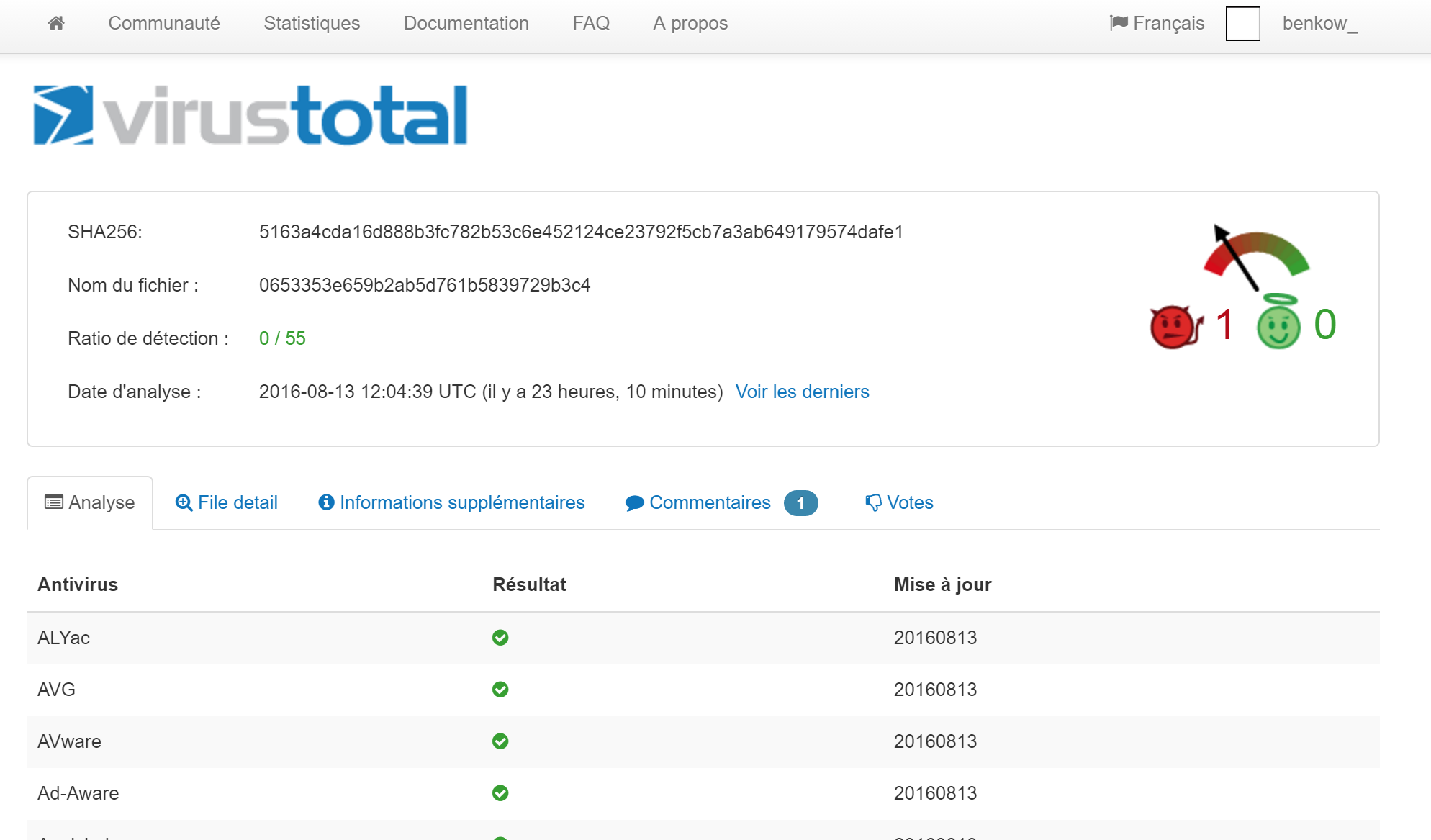
We found our sample and it’s an interesting one. Actually, Drupal-locking is a very small part of the available feature of the self-called "Rex" malware which is still in evolution. We found many different variants from April to August 2016.

Rex malware weapons
Rex is made of 5 different parts. Some of them seem to be still in development:
- Attack vector
- Bitcoin mining
- C&C Communication
- Ransom – Armada Collective
- DDoS
Hereafter, we will look into details for each of this part.
Attack vector
Depending of the variant, Rex malware scan Internet for different vulnerable services. The kill chain is simple:
- Bots are scanning Internet for vulnerable websites
- Websites are infected and defaced (Drupal-locker)
- “Rex” malware is dropped on the server
- The server communicates with other bots via P2P.
Hereafter, a non exhaustive list of exploits used by different variants of Rex malware.
Drupal
It’s not something new, Rex can exploit an SQL injection on Drupal 7 via CVE-2014-3704. The malware adds a new admin account, locks all blogposts with website-locker notes, uploads and executes Rex.
WordPress
Rex is able to infect other CMS. WordPress plugins are mainly targeted. At least 8 exploits are available:
- Plugin Revslider RCE - https://www.exploit-db.com/exploits/35385/
- Plugin Woocommerce RCE - https://cxsecurity.com/issue/WLB-2016040066
- Plugin Robo Gallery RCE - http://www.vulnerability-lab.com/get_content.php?id=1822
- Plugin WP-squirrel RCE - https://packetstormsecurity.com/files/134688/wpsquirrel-rfi.txt
- Plugin Gwolle Guestbook RCE - https://www.htbridge.com/advisory/HTB23275
- Plugin Site Import 1.0.1 LFI - https://www.exploit-db.com/exploits/39558/
- Plugin Brandfolder 3.0 LFI/RFI - https://www.exploit-db.com/exploits/39591/
- Plugin Issuu Panel 1.6 RFI & LFI - https://packetstormsecurity.com/files/136398/wpissuupanel-rfilfi.txt
We have found some infected WordPress websites but we didn't see any of them locked.
Magento
The botnet scans for Magento eCommerce too. It looks for ShopLift RCE - https://www.exploit-db.com/exploits/37977/. The attack is similar to the Drupal attack. A new admin account is created and a Webshell is used for executing Rex.
Misc
A few other exploits are shipped with Rex:
- Apache Jetspeed – CVE-2016-0710 http://haxx.ml/post/140552592371/remote-code-execution-in-apache-jetspeed-230-and
- Exagrid – CVE-2016-1560 - https://github.com/rapid7/metasploit-framework/blob/master/modules/exploits/linux/ssh/exagrid_known_privkey.rb
- AirOS RCE - https://github.com/rapid7/metasploit-framework/blob/master/modules/exploits/linux/ssh/ubiquiti_airos_file_upload.rb
The above list confirms that Rex does not focus on website locking but tries to build a P2P botnet.
Bitcoin mining
As lots of malware, Rex has bitcoin mining capabilities. We won't dig into details for this.
C&C communication
We haven’t looked deeper in the network part but thanks to @silascutler @DlBlind, we know that this botnet use Kademlia P2P network (“/home/user/src/rex/dht/” https://github.com/nictuku/dht ) on port 5099 with TLS enabled.
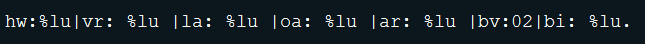
It seems that all aforementioned weapons are available through the P2P network.
Ransom – Armada Collective
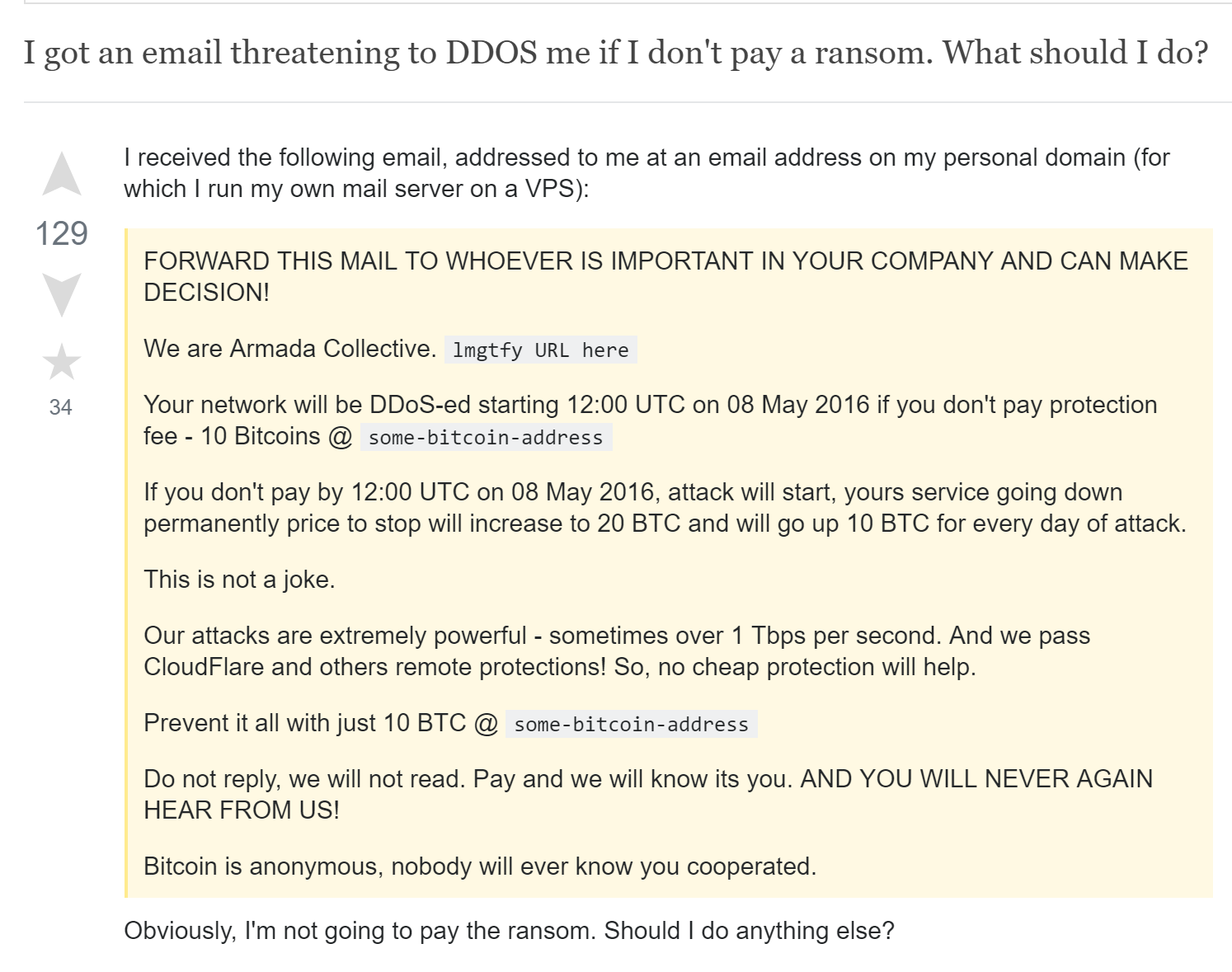
The most curious feature of the malware is called RansomScanner. It is used to retrieve admin contacts of the infected website, and send a DDoS threat email. Below, the email template:
It’s a well-known template used by the crooks of Armada Collective. Lot of people have received this kind of email. Cloudflare wrote a blogpost about this ransom note. There is a supposed gang that sends extortion email to online businesses but nobody has seen any real DDoS. Unfortunately, this kind of scam seems works.
In spite of the lack of actual DDoS follow through, it appears that many victims are paying the extortion fee. A security analyst from the Bitcoin analysis firm Chainalysis studied payments sent to the Armada Collective's Bitcoin addresses and concluded that more than USD$100,000 has been sent to the attackers by victims.
An example of StackExchange post:
But things starts to be different...
DDoS
Armada Collective emails look like hoax, BUT, we have seen infected servers that actually run real DDoS attacks!
Armada collective seems to start a new strategy and try to launch real attacks. The “1Tbps” threat seems ridiculous but If the botnet grows leveraging on fresh vulnerabilities, it may become more harmful.
In the recent versions of Rex, the ransom note has been updated:
Now, crooks talk about a 15 minutes testing DDoS. They ask checking logs as a proof. They want to be taken seriously. Rex looks like a kind of strange webserver-ransomware that didn’t encrypt files but lock access to administration page and threat to DDoS.
Conclusion
Linux botnets continue to evolve and become very interesting. In this case, what looks like at first sight a Drupal locker is in fact a complete botnet, still in development, with many features.
In the nexts write-ups we will try to explain each module of this botnet. As usual the attack vector is not 0day but well known vulnerabilities, so I’ll conclude this article like other:
If you are a website administrator, DO NOT LEAVE OUT OF DATE SERVICE ON THE INTERNET.
Samples:
