An “attack surface” refers to the set of cybersecurity risks to which a company or organisation may be exposed. It is (often) very broad, and results from the fact that a cyberattack can occur from almost anywhere. This is why, in order to be able to anticipate the threat and implement countermeasures, a method of modelling cyberattacks – the Kill Chain – was launched in 2011.
Derived from a military concept to identify the structure of an attack, the Kill Chain offers a framework for better understanding cyberattacks, and the operating methods of cybercriminals in particular. How does the Kill Chain work? What steps does it follow? How has the model evolved? And why is the Kill Chain still an indispensable part of cyber protection? Read on for more information.
What is the Kill Chain?
Developed in 2011 in a white paper by Lockheed Martin, a US aerospace and defence company, the Kill Chain was developed as an analytical framework for breaking down and understanding the various stages of a cyberattack. This prevention framework was initially developed to try to stem intrusion attempts by advanced persistent threats (APTs) against computer networks, hence the first known name of “Intrusion Kill Chain”. Its title would later be changed to the “Cyber Kill Chain” model.
The Kill Chain model is based on the idea that a cyberattack must pass through seven consecutive phases to succeed, from the recognition phase to the data exfiltration step. The underlying idea behind this model is that by breaking a link in this chain, it becomes possible to counteract the cyberattack.
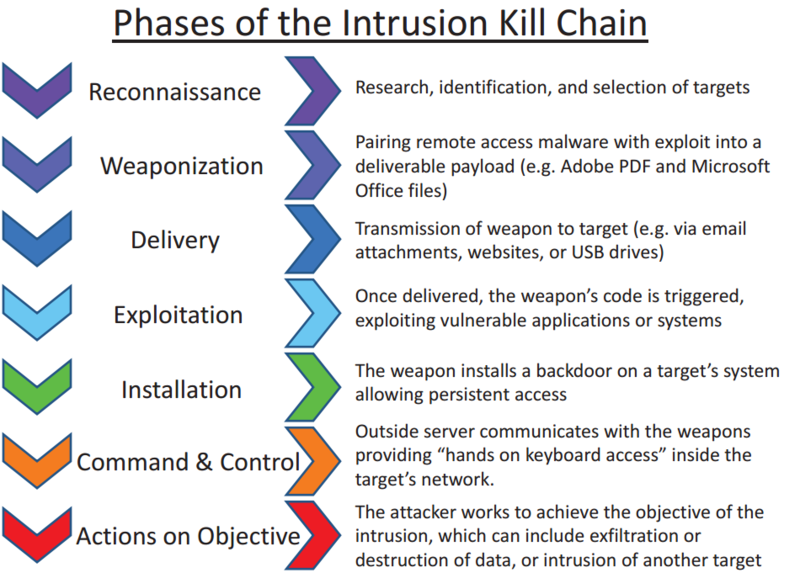
The seven stages of the Kill Chain are as follows:
- Reconnaissance: this is the step prior to any operating procedure. This involves choosing the target (company, person, and even component), and collecting information about it. In the case of a human target, the attack can have a social facet and reconnaissance is performed on social networks. In the case of an attack on a company, reconnaissance can involve identifying domains, sub-domains and other IP addresses. Finally, reconnaissance also (and most importantly) means identifying vulnerabilities which the cyber-criminal may be able to exploit.
- Weaponisation: following the reconnaissance phase, the cybercriminal prepares the tools (and in particular the malware) that will be used during their future attack.
- Delivery: the goal here is simple: the cybercriminal must ensure the tool that has been developed reaches the location where it can do the most harm. This is the point at which the phishing email is sent, the infected USB stick is posted or the malware is deployed in the network.
- Exploitation: as its name suggests, this means activating the malicious code on the infected machine to exploit the technical vulnerability and take control of the target system.
- Installation: the installation stage involves consolidating access to the IT asset. The aim is to install itself (discreetly) over time. This is the point at which the cybercriminal tries to install a back door on the infected machine.
- Command and Control: having opened a persistent line of access to the machine, the cybercriminal establishes a communication channel between the compromised system and an external control server, known as C2 (Command and Control) using the malware that was previously installed.
- Actions on Objectives: The actions on objectives stage is the last phase of the Kill Chain. Several actions can then occur, such as data exfiltration or encryption of the electronic asset. During this step, the infected machine can also be used as a jump-off point enabling lateral movement to another machine.
Some Kill Chain models also include an eighth step, monetisation, in which cybercriminals seek to recover money from previously-deployed ransomware or by selling stolen information. The traditional theoretical model also does not make it clear that different groups can be involved in these seven stages. However, not all groups of cybercriminals use all of these stages. With the professionalisation of cybercriminal groups and the advent of a vulnerability economy, for example, some will buy initial access from another group and then become involved only from the third stage. All these peculiarities then require evolutions in the model, giving rise to alternative versions of the Kill Chain.
An evolving Kill Chain model
While the Kill Chain model has been (and remains) an effective way of breaking cyberattacks down into sequential phases, it has some limitations when faced with modern, dynamic operating methods that can skip or repeat some of these steps. Its usefulness remains theoretical, and it may be less effective against complex attacks that involve disinformation, fraud, or interference – or even internal threats. To address these limitations of linearity and granularity, new repositories have emerged.
One of the most common is the MITRE ATT&CK (Adversarial Tactics, Techniques and Common Knowledge) framework, which breaks down to form an exhaustive data repository of the tactics and techniques used by cybercriminals through the different phases that make up an attack. Unlike the Kill Chain, which focuses primarily on the steps of an attack, the MITRE ATT&CK repository provides a detailed overview of specific attack behaviours, helping to understand and simulate attacks more closely. Reconnaissance is one of the seven stages of the Kill Chain, and one of the fourteen stages of MITRE ATT&CK. This dynamic model is more suitable for organisations seeking to perform more granular security assessments and proactively improve their cybersecurity stance. The SOC and CSIRT teams also use this repository to understand the cyberattacks they face and learn how to respond effectively. That’s why it’s important for SOC operators and solution editors to easily associate the different alert logs issued with an element of the ATT&CK MITRE repository, and thus be able to run the initial response more efficiently.
The result of a merger between the two approaches, the Unified Kill Chain was developed through a hybrid research approach “combining design science and qualitative research methods”. As defined on its own website, this repository comprises 18 phases, divided into three main stages: “In” (initial access step), “Through” (target control step), and “Out” (target achievement step).
Ben Nimmo and Eric Hutchins from Meta have proposed adding a new repository to the original Kill Chain: the Online Operations Kill Chain. This new approach incorporates malicious online behaviour patterns, such as espionage, misinformation, fraud and more. This new repository is structured around ten phases, covering activities such as asset acquisition and disguising, information gathering, coordination and defence testing.
Other frameworks more specific to certain sectors have emerged, such as the Cyber Fraud Kill Chain framework, developed by Optiv in response to cyberattacks against financial institutions.
Kill Chain: a vital tool for cyber protection
With all these alternative frameworks, the Kill Chain remains more than ever an indispensable tool to maintain the cybersecurity of companies and organisations. This is a tool that Cyber Threat Intelligence teams also rely on, both to study and understand cyber threats and for the continuous improvement of cybersecurity product protection.
An endpoint protection strategy allows the compromise attempt to be detected from the first stages, helping to stop the cyberattack before it reaches its final phase. To protect yourself on a daily basis, you can therefore use endpoint protection solutions. Endpoint detection and response (EDR) solutions are a first response for protecting end devices, complemented by extended detection and response solutions (eXtended Detection & Response – XDR). They aggregate and analyse all the data from the assets in your infrastructure (networks, terminals, etc.). By detecting connection attempts (recognition), identifying file downloads on the machine and using a sandbox to analyse files (exploitation) or analysing outgoing network traffic (command and control), these solutions can detect the threat at the various stages of the Kill Chain.
And to improve your security strategy still further, you can implement firewalls and intrusion detection solutions. By detecting and preventing vulnerability exploitation, providing Web security through URL filtering and IP and domain filtering, or segmenting networks, network protection solutions deliver protection, control and performance through the various stages of the Kill Chain model.
Although originally designed for traditional IT environments, it is important to note that the Kill Chain can also be used in industrial environments (OT). In this case, the seven phases remain the same; only the reconnaissance criteria (protocols and ports) and the final target (the industrial control system, ICS) differ.