If you think Locky, the cryptoware that became famous in 2016, is ancient history now you would be wrong. Although its new version is little more than a cosmetic change, the virus is still present in cyberattacks.
Back in 2016: Locky reached the symbolic level of 7.8 million dollars’ worth of ransoms, according to a study by Google, and became the year’s most “profitable” ransomware. It spread like wildfire throughout Europe, mainly using a Trojan horse attack technique in which you receive, generally by e-mail, an invoice containing a macro in the form of a Word document. Without thinking, you open the document and the attack starts. Locky encrypts the files on your computer, and sometimes on your entire network, and then demands a ransom in exchange for the decryption key.
A massive attack at the end of the summer
Between late August and early September, a new campaign of this ill-reputed ransomware swept across the networks. According to David Bisson, 23 million emails were sent out in less than 24 hours. Our Breach Fighter tool successfully detected the waves of Locky (along with its variant Lukitus) and GlobeImposter.
Locky: what’s new?
The changes are minor in comparison with the previous version, and mainly cosmetic: an extra series of characters at the beginning and end of the message and a new extension.
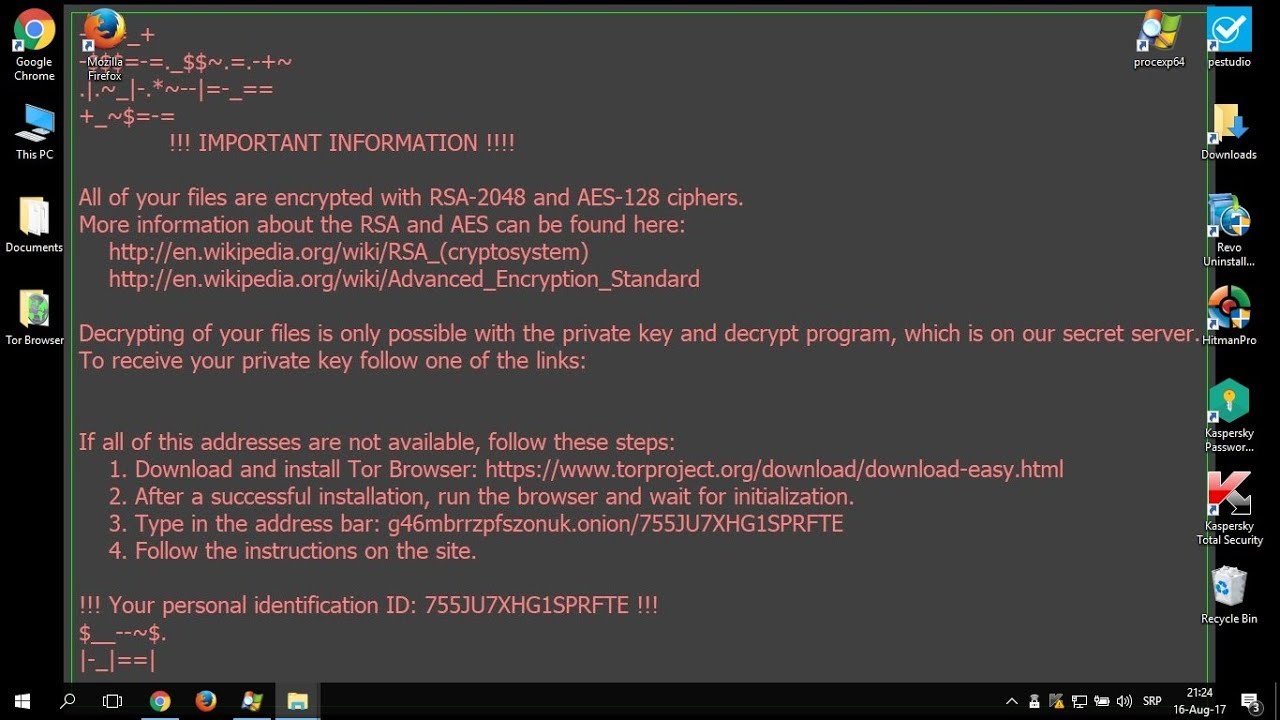
They are also minor in terms of their impact, as the additional characters don’t have any effect and the new extension has already been detected and dealt with in Stormshield’s Network Security solutions, taking the malware's behavioral change into account.
This is not the case with traditional antivirus software, which has to quickly change its signature analysis solutions. This is why a proactive approach is preferable to a reactive approach.
