Hacking point of sales (PoS) systems is a very trendy topic. A lot of PoS malware can be found in the wild (jackPOS, gamaPOS, Backoff, FighterPOS…). At every big breach of PoS systems, media talk about sophisticated attacks involving high skills and great tools. But sometimes, it can be very easy to compromise a PoS and no particular skills are required to steal sensitive information, such as credit card numbers.
During our investigation, we caught a very interesting case of “low-cost” PoS hacking. This article tries to unveil the inner process of infection.
Everything started with a Win32.Ardamax sample found in the wild. Ardamax is a classical sample which is a commercial keylogger available on the Internet. After reversing this sample, it appears that the malware uploads data on a FTP server hosted in Germany, on server4you. This FTP can easily be accessed (login and password are embedded in the sample) and contains victims’ uploaded data. This FTP seems to be used since the 9th of October 2014. The server is full of samples, tools and exfiltrated data. We cannot publish the original sample, because Server4you has not shutdown the server yet.
This repository contains the original Win32.Ardamax sample, malwares (Darkomet, Andromeda, Gorynych…), some memory scrappers to retrieve credit card numbers and websites crawlers scan results. On the same repository, we can find screenshots, microphone recordings, webcam pictures as well as keystroke recordings for each single infected computer.
Crooks have access to about fifteen point of sales computers as well as to some SCADA systems.
We spent a lot of time contacting CERTs and companies for cleaning computers but day after day new infected point of sales data were uploaded to the FTP repository. How were crooks able to continuously find new targets to infect? Amongst uploaded data, some screenshots caught our attention: somebody was using a VNC brute force tool against a large range of IP addresses.
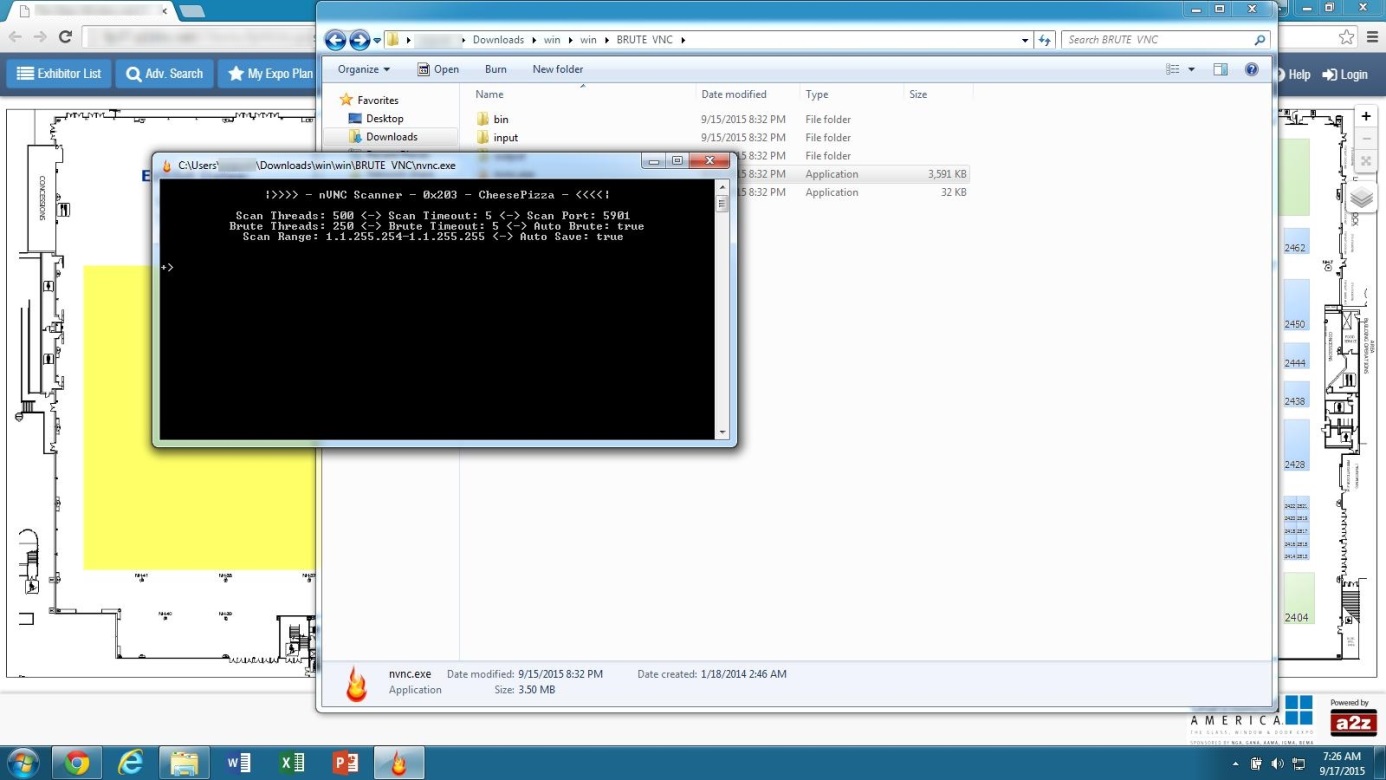
The tool used by crooks can be retrieved from an archive uploaded to the VirusTotal website: virustotal.com/fr/file/b6c3445386f053c1cca711c8389ac8b12d05aad46bbfec02d721428442cd2ed5/analysis/1442602500/
It seems they are using infected computers to brute force VNC servers with weak passwords . When a new VNC connection is established, a new payload is downloaded through a regular browser and installed on the newly infected machine. No exploit or sophisticated techniques are employed.
Once the payload is downloaded, any installed antivirus is configured to ignore it or is even completely uninstalled. This requires administration rights on the computer, but obviously this is quite a common situation on point of sales systems.
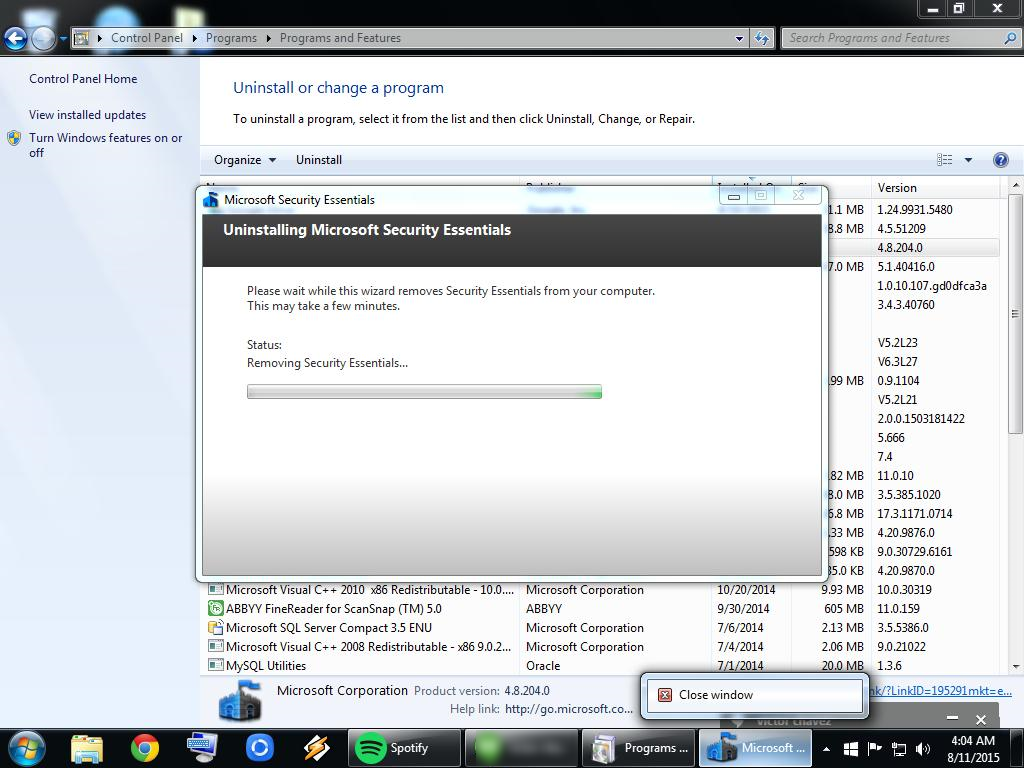
This day, it is Gorynych which was spreading: virustotal.com/fr/file/406c30d40f3837615e3b393edc1d6667213c3d287ec006be6198d68124041d43/analysis/
Last but not least, crooks used compromised computers to administrate the Gorynych panel:
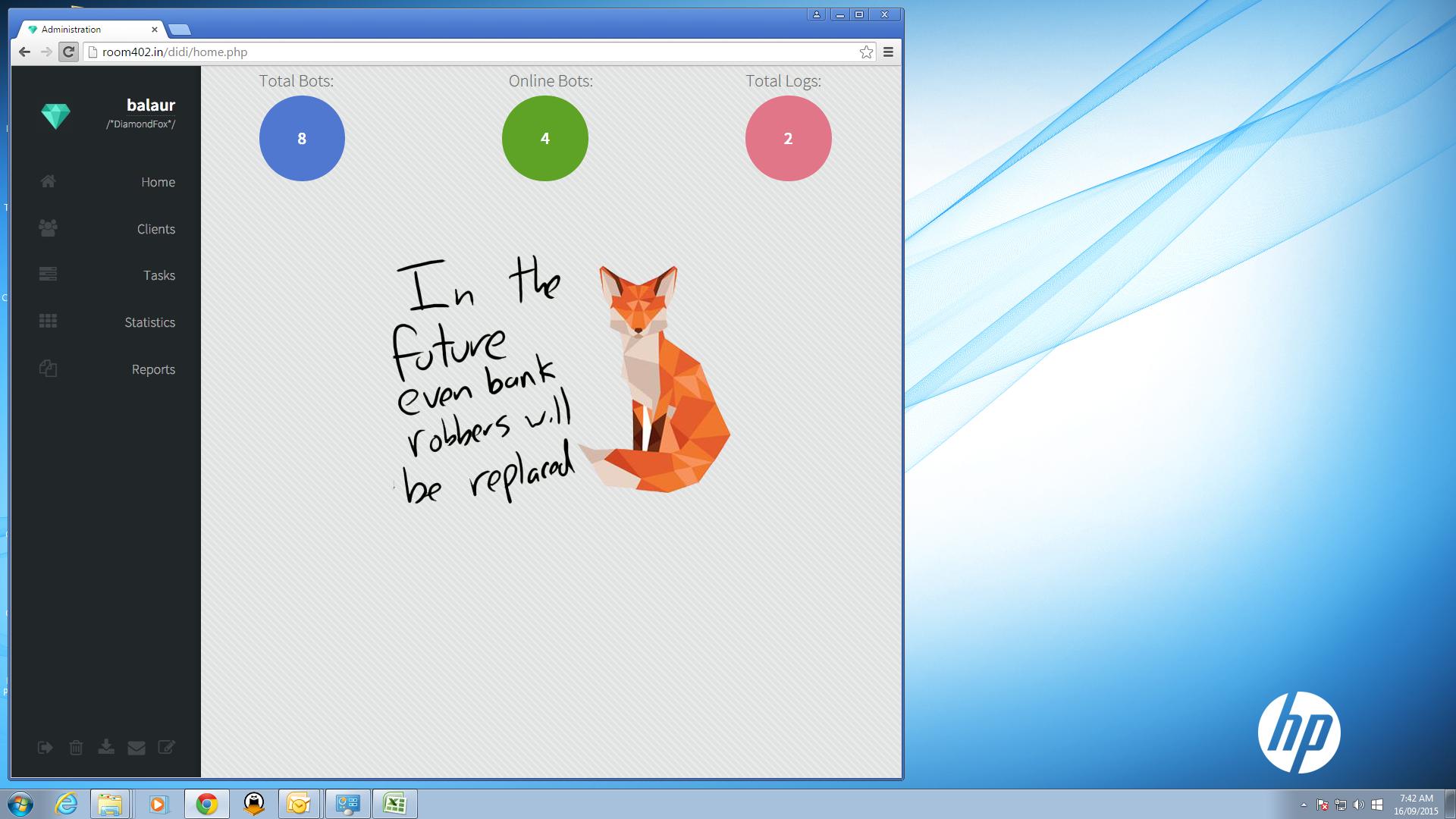
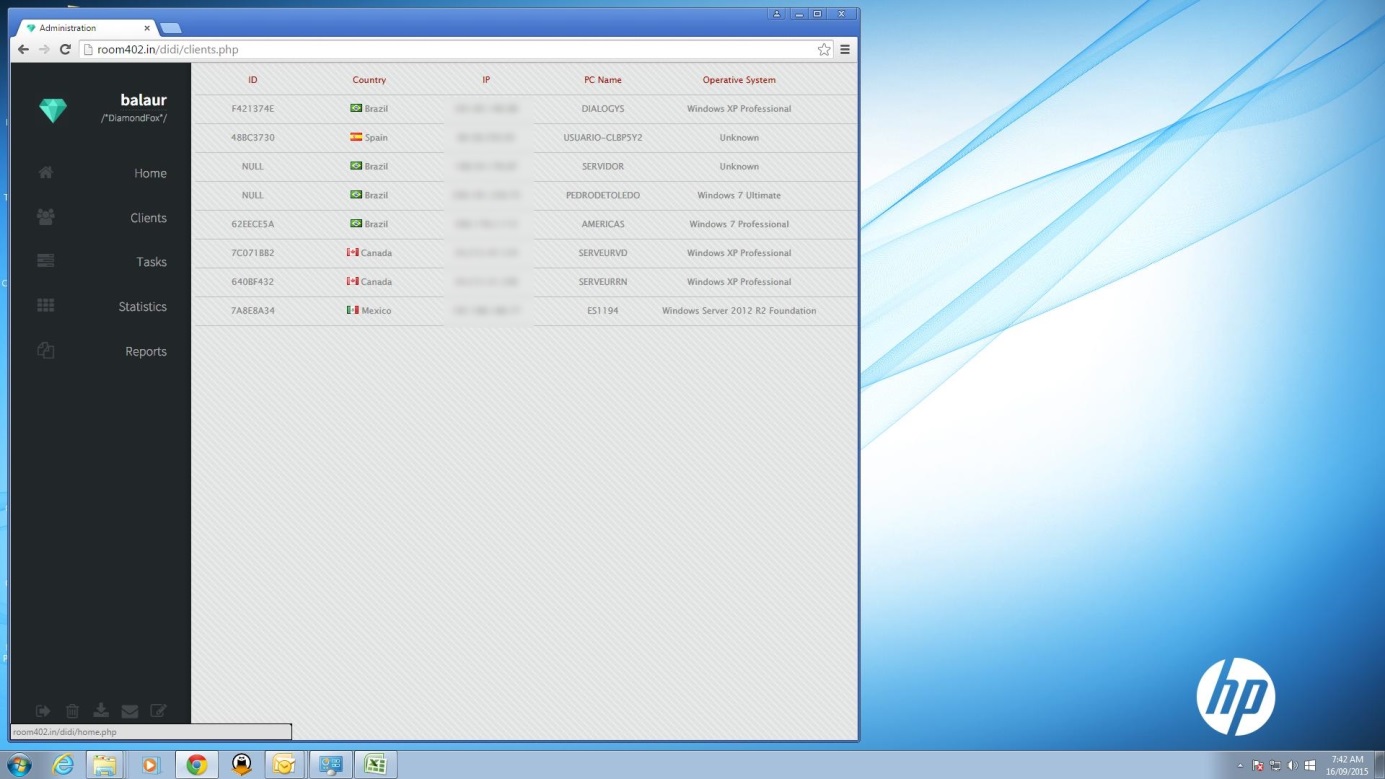
During several days we followed the whole stealing process. Crooks infected point of sales and used mainstream memory scrappers like SearchforCC for credit card numbers exfiltration.
As we can see, there is no need of sophisticated attacks or processes to infect systems. With a little more time, crooks would be able to infect a much larger range of systems. With a short list of 152 weak passwords, an attacker is able to control a lot of point of sales systems. In this case, crooks access from small and medium-sized enterprises to companies with 500 million dollars in annual sales.
This kind of campaign would not be so easy to carry out if:
- Point of sales computers were not directly connected to the Internet;
- Strong VNC passwords were used;
- Administrator accounts were not used to connect to sensitive systems.
This kind of negligence can result in a huge waste of money and a very bad image for the compromised company.
Appendix
Payload found on the FTP site
Related servers
posserverupdate.ddns.net
teamviewer.ddns.net
anjing.no-ip.biz
chiproses.net
maculastudios.com
room402.in
193.84.64.159
212.105.175.93
173.214.168.141