A new critical unauthorized access vulnerability impacting has been reported. It has been assigned the reference CVE-2024-20439 and a CVSS 3.1 score of 9.8. The Stormshield Customer Security Lab details our protection offerings.
This flaw impacts the following version of the application:
- 0.0
- 1.0
- 2.0
It should be noted that this vulnerability is actively exploited and the technical details allowing an attacker to exploit this vulnerability are public.
Initial vector attack of the Cisco vulnerability
The vulnerability allows an attacker to connect to the Cisco Smart Licensing Utility as an administrator by using an account which username and password are predefined and hardcoded in the code of the API.
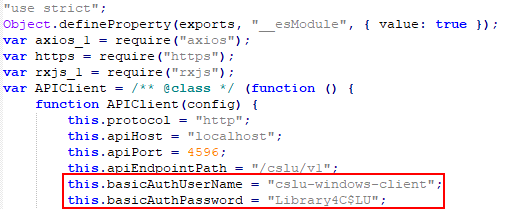
Technical details of the Cisco vulnerability
The Cisco Smart Licensing Utility application exposes a REST API on all the available network interfaces. It makes possible for an attacker that has a network access to the server hosting this API to exploit this vulnerability.
Attack modelling with MITRE ATT&CK
MITRE ATT&CK
- T1190 (Exploit Public-Facing Application)
How to protect against the Cisco vulnerability with Stormshield Network Security
Protection against CVE-2024-20439
Stormshield Network Security (SNS) firewalls detect and block exploitation of CVE-2024-22116 with the protocol inspection:
- http:client.237: Exploitation of a hardcoded password vulnerability in Cisco Smart Licensing Utility (CVE-2024-20439)

Confidence index for the protection offered by Stormshield |
Confidence index for the absence of false positives |
Recommandations regarding the Cisco vulnerability
It is highly recommended to update the Cisco Smart Licensing Utility application to version 2.3 (or above). You can also access the official bulletin.
