On January 17th 2020, Microsoft issued a security advisory about the vulnerability CVE-2020-0674 affecting Microsoft Internet Explorer. This vulnerability allows an attacker to execute malicious code remotely on a system running Internet Explorer. The vulnerability is located in jscript.dll component, the old Internet Explorer JavaScript engine. However, attacks could force Internet Explorer to fallback to this vulnerable engine instead of the most recent one, Jscript9.dll.
This vulnerability seems very similar to previous vulnerabilities CVE-2018-8653 and CVE-2019-0609, affecting that same component.
Even though there are currently no public code samples available, different sources indicate that this vulnerability is already being exploited in the wild while Microsoft has not published any security fix yet.
An attack exploiting this vulnerability would take place when a vulnerable system accesses a website. This website can be a legitimate one that the attackers have compromised. Attackers can also convince the user to go to a website crafted specifically for that purpose, for instance by making the user click on a link in an e-mail.
Stormshield Endpoint Security delivers effective proactive protection against this threat if the following recommendations have been applied, by blocking attempts to exploit the vulnerability on the workstation.
Stormshield Endpoint Security – Block this threat
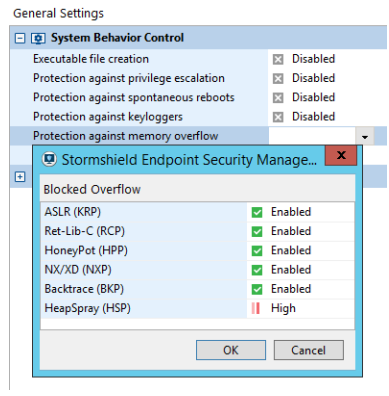
Protections against exploitation of memory corruption vulnerabilities
Based on attack samples that exploited similar vulnerabilities in the past (CVE-2018-8653 and CVE-2019-0609), we advise to enable Stormshield Endpoint Security RCP (Ret-Lib-C Protection) and HPP (HoneyPot Protection).
These protections are enabled by default as soon as protection against memory overflow is enabled (see SES Administration guide, page 141).
Block access to jscript.dll
Besides, as the vulnerability affects jscript.dll, you can create an applicative rule to deny any access to that component.
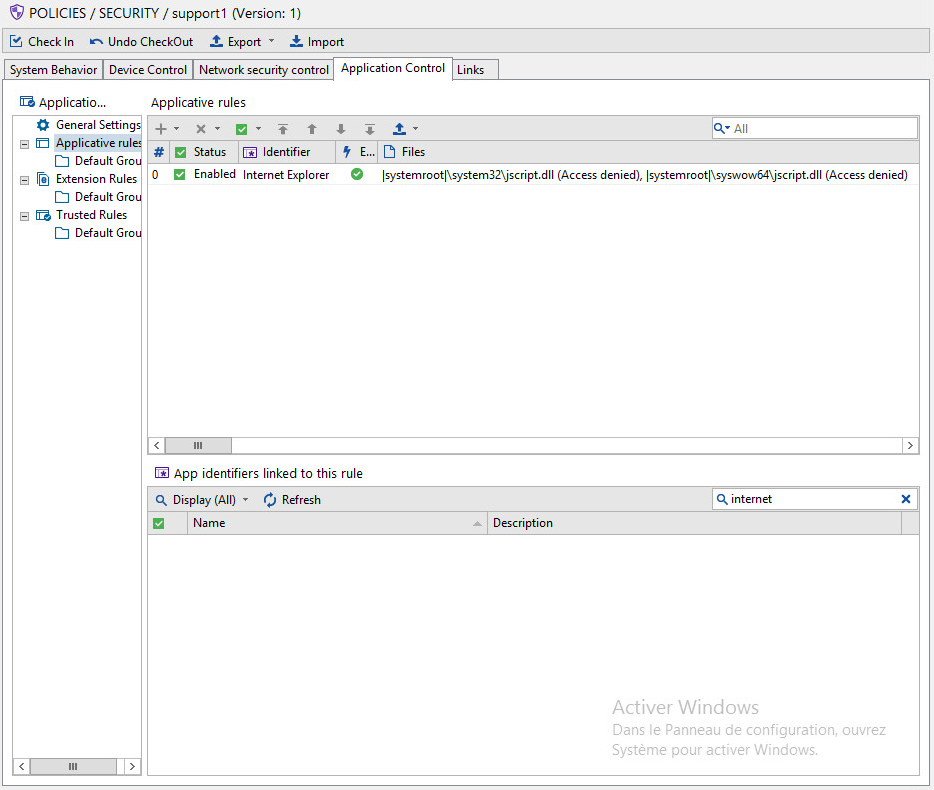 According to Microsoft, Internet Explorer IE11, IE10 and IE9 use by default the new Jscript9.dll engine that is not impacted by this vulnerability, instead of the vulnerable jscript.dll engine.
According to Microsoft, Internet Explorer IE11, IE10 and IE9 use by default the new Jscript9.dll engine that is not impacted by this vulnerability, instead of the vulnerable jscript.dll engine.
The application of this rule will not affect these browsers, except when accessing some websites requiring specifically the usage of the old jscript.dll engine and that will not work anymore in these browsers after applying this recommendation.
In case a user would face troubles browsing a specific website after applying this recommendation, you can look for the following alert in Stormshield Endpoint Security logs in order to understand if this new rule is in cause:
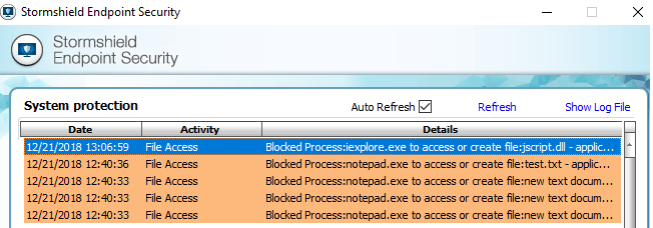
Other recommendations
Workaround solution from Microsoft
Microsoft official recommendation consists in restricting access to the vulnerable jscript.dll component.
This can be done using Windows Command Prompt (open as administrator):
1. For Windows 32 bits operating systems:
cacls %windir%system32jscript.dll /E /P everyone:N
2. For Windows 64 bits operating systems:
cacls %windir%system32jscript.dll /E /P everyone:N
cacls %windir%syswow64jscript.dll /E /P everyone:N
Functional impact of this recommendation:According to Microsoft, Internet Explorer IE11, IE10 and IE9 use by default the new Jscript9.dll engine that is not impacted by this vulnerability, instead of the vulnerable jscript.dll engine.
The application of this rule will not affect these browsers, except when accessing some websites requiring specifically the usage of the old jscript.dll engine and that will not work anymore in these browsers after applying this recommendation.
How to tell if you have been infected
There is currently no known indicator of compromise that would allow detecting if you have been impacted by an attack exploiting this vulnerability.
