Ukraine is currently in the middle of a real cyber war. After several rounds of DDoS attacks on government websites and banks, Ukrainian government bodies (as a whole) are now in the line of fire of malicious attacks. And after DDoS, these cyberattacks include a devastating malware: HermeticWiper. The Stormshield Customer Security Lab team provides an update on a critical vulnerability in a complicated geopolitical situation.
UPDATE: this security alert has been update with CaddyWiper new malware analyse at the bottom of this paper.
Context of the attack
On February 23, Eset's research teams announced that they had discovered a new data erasure malware in a Twitter post. Dubbed HermeticWiper (a variant of KillDisk.NCV, now renamed Win32/HermeticWiper.a), it is reportedly currently used against various Ukrainian government bodies, such as the Ministry of Foreign Affairs, ministers' offices, and the Parliament (the Rada). The question of the official attribution of the attack is still under debate, although the current geopolitical situation and the presence of an APT group linked to the country seem to point to Russia.
This malware, visibly distributed by GPO and thus aiming at compromising the victim's computer system, hijacks a legitimate disk partitioning driver to corrupt system partitions, resulting in the loss of data on a machine (server or workstation). The objective of the attack is clear and unique: the destruction of data.
Technical details of the attack
To date two variants of this malware are known:
- 1bc44eef75779e3ca1eefb8ff5a64807dbc942b1e4a2672d77b9f6928d292591
- 0385eeab00e946a302b24a91dea4187c1210597b8e17cd9e2230450f5ece21da
An in-depth analysis of the malware shows us that this wiper is signed by the company "Hermetica Digital Ltd" through the root authority Digicert. The certificate was revoked in the afternoon of 24 February 2022.
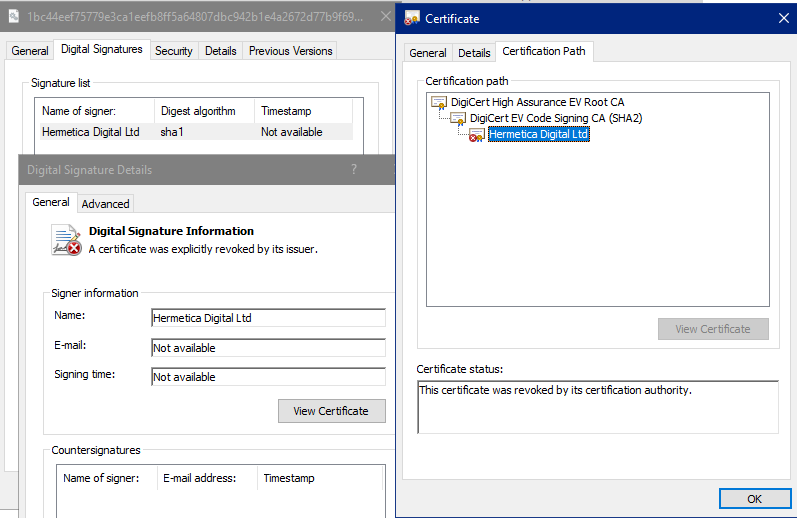
Figure 1: the certificate signing the malware is valid although revoked
The malware has not been reworked post-compilation to make it difficult to analyze. In this sense, it is not compacted (packaged) and the strings appear in clear text.
Another interesting element in this analysis is that an old version was compiled (according to the program's metadata) on December 28, 2021. A sign that the action is premeditated for a long time:
Figure 2: dates of creation of the binary according to the metadata it contains
In terms of operation, when the malware starts its execution, it draws from its embedded resources section to extract one of the following four drivers:
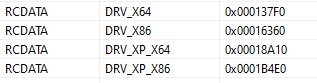
Figure 3: the four drivers embedded in the malware
These drivers correspond to Windows 7/8/10/11 and XP systems and are available in both 32-bit and 64-bit. It can be seen from the SZDD signature that they are compressed using the LZSS algorithm (an old compression format historically used by Microsoft since Windows 3.x, by utilities such as COMPRESS.EXE). This explains the dependency of the malware on LZ32.DLL.
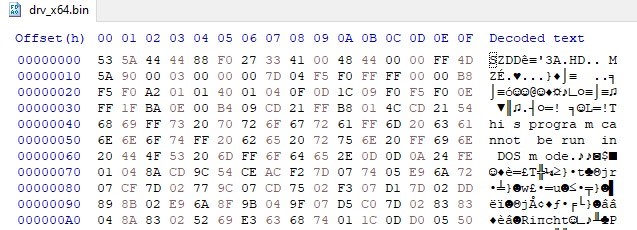
Figure 4: decoding a driver
File extraction is then simple:
| Driver | SHA-256 |
| XP 32 bits | 2C7732DA3DCFC82F60F063F2EC9FA09F9D38D5CFBE80C850DED44DE43BDB666D |
| XP 64 bits | 23EF301DDBA39BB00F0819D2061C9C14D17DC30F780A945920A51BC3BA0198A4 |
| Vista+ 32 bits | 8C614CF476F871274AA06153224E8F7354BF5E23E6853358591BF35A381FB75B |
| Vista+ 64 bits | 96B77284744F8761C4F2558388E0AEE2140618B484FF53FA8B222B340D2A9C84 |
Figure 5: SHA-256 fingerprint of extracted drivers
These drivers are those found in the partition management software "EaseUS Partitionning" at least in version 9.2.1. They are signed and legitimate but the certificate is expired and the timestamp is not conform:
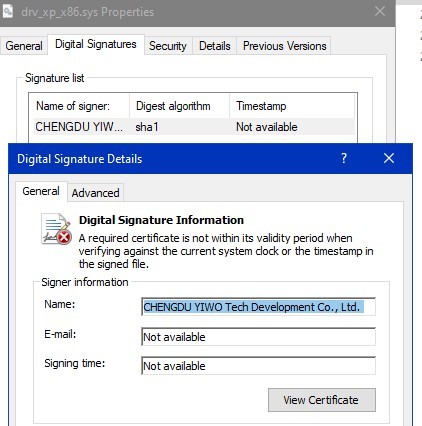
Figure 6: drivers signatures
The right driver to load is selected in order to correspond to the operating system of the host machine. Then, the malware opens a communication channel to the driver \\.\EPMNTDRV\ and the disk writing is done through this way. This driver is ideal, both for bypassing user-land security solutions and also for overwriting disk areas corresponding to volumes mounted and used by Windows.
During the analysis of the malware, it was found that the malware does not alter the MBR (thus retains the partition table). On the other hand, it alters the first sectors of FAT/FAT32/NTFS partitions of each disk. The consequence is that the system does not boot anymore due to partition corruption.
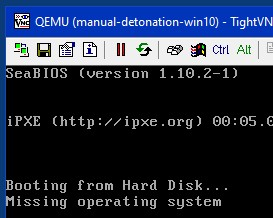
Figure 7: corrupted system not restarting
Here, the message displayed comes from the error handling of the MBR which remained intact:
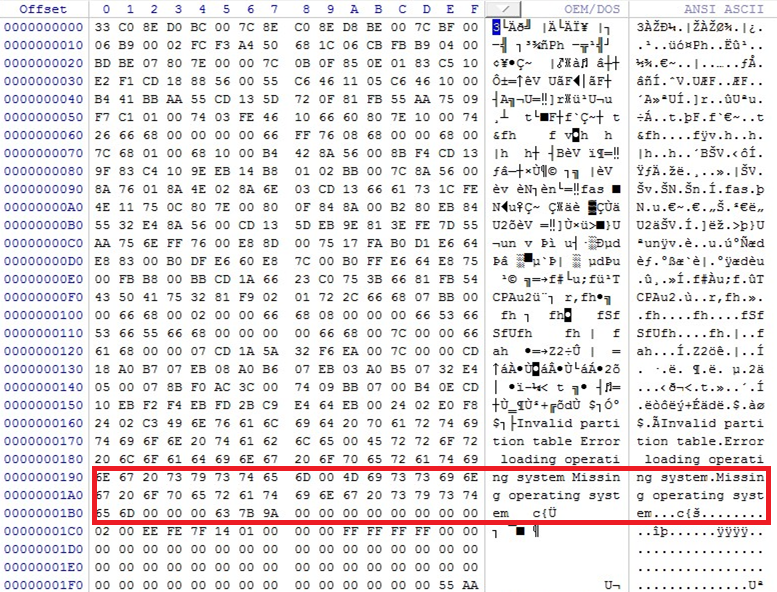
Figure 8: MBR still intact and able to display a message in case of a boot partition location error
An examination of the first sectors of the partitions reveals the corruption:
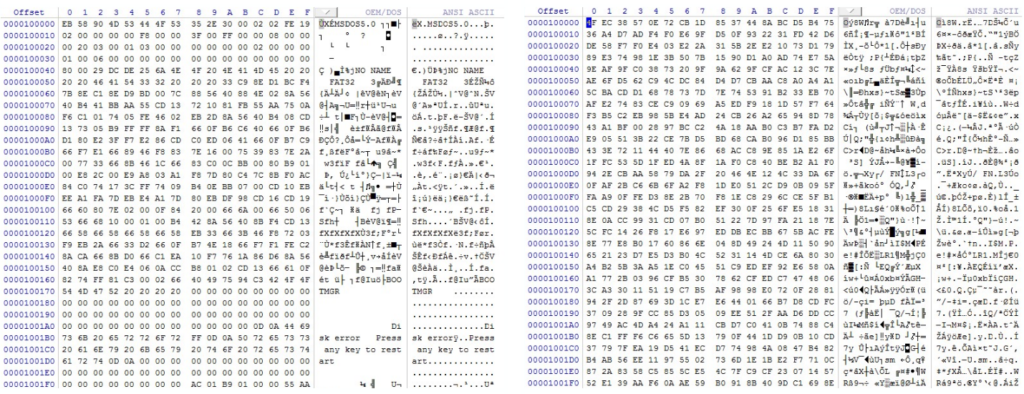
Figure 9: on the left, the healthy FAT32 partition, and on the right, the corrupted FAT32 partition

Figure 10: on the left, the healthy NTFS partition, and on the right, the corrupted NTFS partition
During the analysis, we found that the first two sectors were overwritten for FAT32 partitions, while many more sectors are overwritten for NTFS partitions. NTFS specificity: the malware targets particular files so that data recovery becomes very difficult.

Figure 11: special NTFS files searched by the malware
Targeted systems
This malware attacks Windows XP, Vista, Seven, 10 and 11 systems, both 32-bit and 64-bit, regardless of the system language.
Other information
Numeric signatures
Both for the malware and for the drivers, the fingerprinting algorithm used is SHA-1. As a reminder, this 160-bit algorithm has been deprecated for several years now. However, due to compatibility with older software, it is still tolerated in some cases.
Administrator rights
This malware absolutely requires administrator rights in order to drop the driver and load it. This is not a problem since in the observed attack vector, the deployment of the malware was done through GPOs (thus with sufficiently high rights).
Execution timing
The malware performs its malicious actions very soon after starting up. Thus, as soon as its CPU activity drops to 0%, the system is already corrupted. Normal Windows life will inevitably lead to a problem in the next few seconds or minutes. Note that the malware does not terminate after corrupting a system, its process remains active but does nothing. Maybe it is waiting for connected removable disks to corrupt them in turn.
Reboot
The malware does not require an immediate reboot of the machine after partition corruption. On the other hand, the operating system may panic after the live corruption of the file system that makes it live. There are many immediate reasons for the panic, but what is certain is that when the Windows kernel panics, the result is a BSOD with a potential forced reboot depending on the settings.
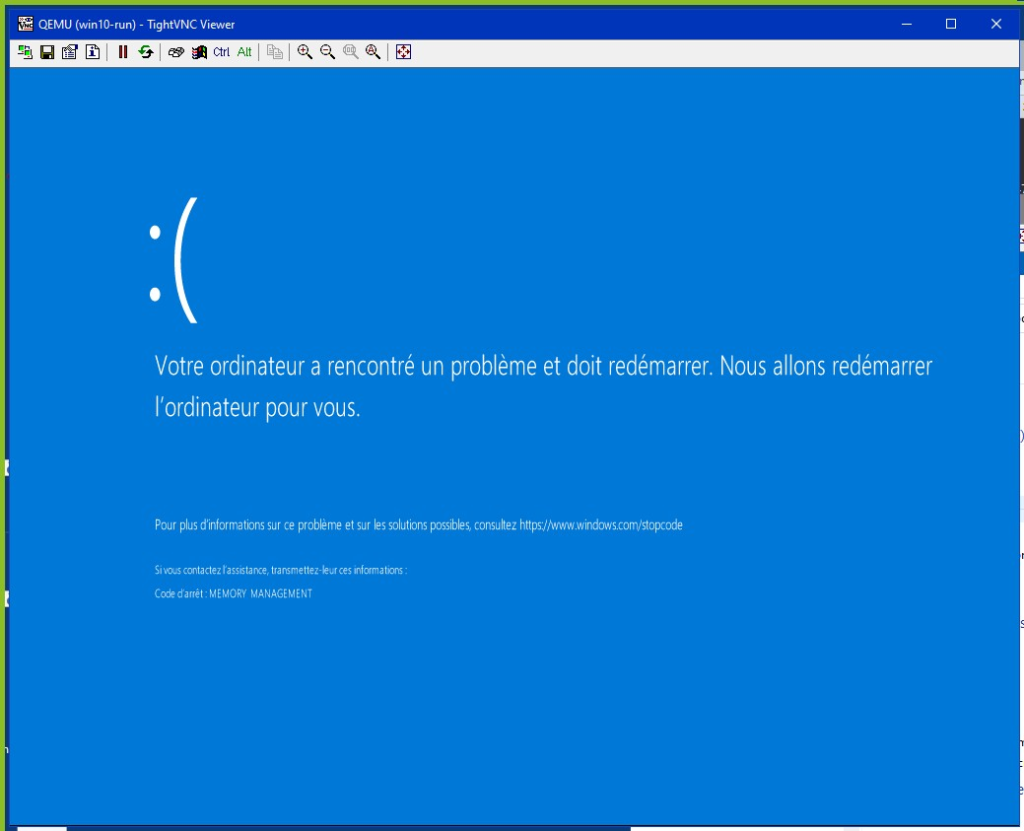
Figure 12: a (French) Windows kernel corrupted by disk wiping
Disabling crash dumps
The malware reconfigures the system to not generate a crashdump after BSOD. It does this by writing the value 0 to this registry location:
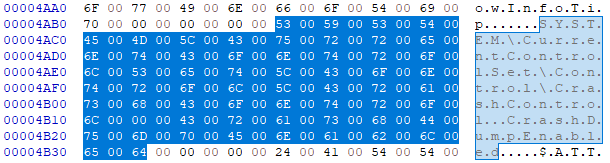
Figure 13: reference to the kernel crash-dump disable register parameter
Divers
- The VSS service is searched and stopped by the malware.
- Some file display settings in the file explorer are altered: ShowCompColor (used to identify compressed files via blue color) and ShowInfoTip (used to display info bubbles)
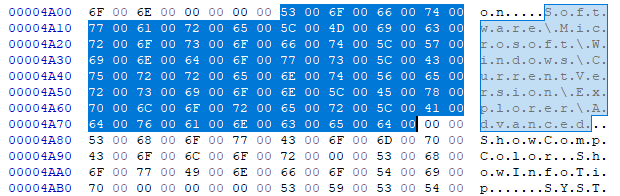
Figure 14: reference to File Explorer Registry Settings
Means of protection provided by Stormshield
Stormshield Network Security
Breach Fighter, a SaaS sandboxing solution that complements SNS, detects all Hermetic Wiper malware.
When a file passes through the stream, SNS will perform a hash of the file and check its safety with Breach Fighter (in case of an unknown file, it will be sent to our cloud detonation environment). As a result, it will be blocked immediately.
For this detection to be effective, you need to:
- have the Premium Security Pack license and the Breach Fighter option;
- activate sandboxing on all file transport streams (SMTP, HTTP, FTP).

Confidence index of the protection offered by Stormshield

Confidence index of no false positives
Stormshield Endpoint Security
SES v7.2
The eraser malware requests the "SeLoadDriverPrivilege" to start the maliciously used EaseUS driver. This behavior is detected and blocked by the SES (v7.2) solution with the elevation of privilege protection set to "High" or "Superior". Without this driver, the malware is no longer able to erase data on the computer.

Confidence index of the protection offered by Stormshield

Confidence index of no false positives
SES Evolution
A specific rule set has been made available to users free of charge to counter this malware.
Specifically, the processes whose signature refers to the certificate stolen from "Hermetica Digital LTD" are blocked. And even if a variant uses another certificate (or no certificate at all), the creation of "driver" files is controlled and authorized only to Microsoft programs.
Please note that this configuration strictly restricts the deposit of drivers for non-Microsoft programs, which can lead to many false positives if the administrator is not careful. This rule is disabled in the provided ruleset. Here is the log of the blocking rule:
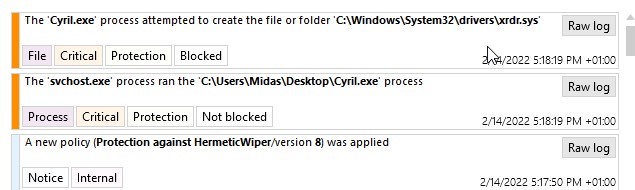
Figure 15: rule block illustration

Confidence index of the protection offered by Stormshield
Confidence index of no false positives
Addendum: new strain CaddyWiper malware analyse
On March 14, Eset's research teams announced in a Twitter post that they had observed a new data erasure malware targeting Ukrainian infrastructures. This new strain, named CaddyWiper, is identified for the moment on 4 files and has the same objective as its predecessor: to make totally inoperable the workstations starting the strain.
Even if the ultimate goal is the same, the technique to achieve it is completely different: the CaddyWiper strain no longer uses the signed driver of the EaseUS tool nor the Hermetika ltd certificate. In order to purge the computer, the malware first overwrites the data in all user directories on all disks. In case these files are owned by another user, it tries to appropriate them via the SeTakeOwnershipPrivilege. Then it accesses the physical disks via "\\.\PHYSICALDRIVEX" and erases the MBR/GPT type information and alters the partition tables of each disk to make them inoperative. The next time the computer is restarted or after a BSOD, the computer will not boot anymore.
Out of these four files, only one is signed by an invalid Chinese certificate because it has expired:
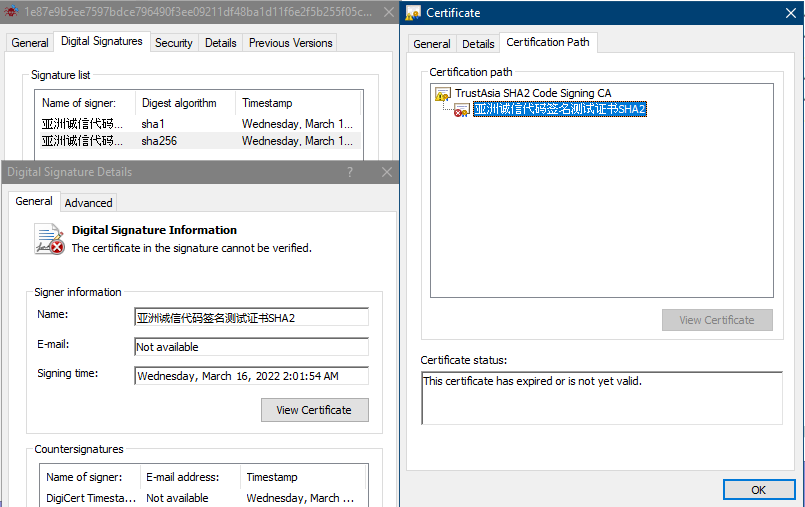
Figure 16: expire certificate signature of the malware
Stormshield product response is efficient immediately.
Stormshield Network Security
Breach Fighter, a SaaS sandboxing solution that complements the SNS firewall, detects all CaddyWiper malware.
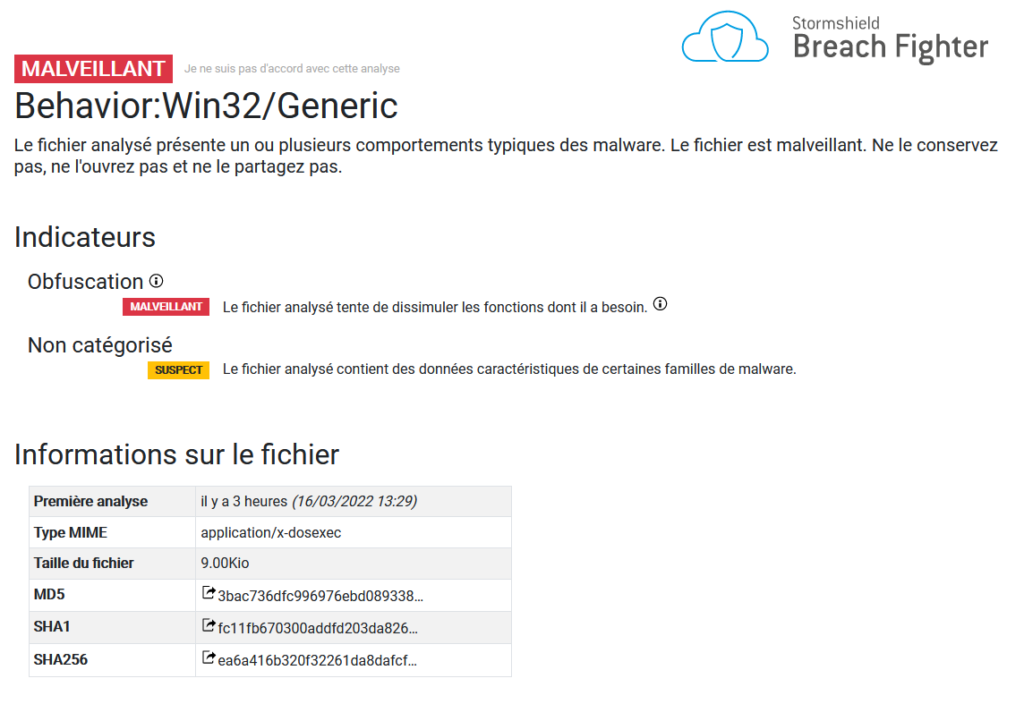
Figure 17: CaddyWiper breachfighter analyse result
Stormshield Endpoint Security
Whether it is the 7.2 version or the Evolution version, both products block the first action of malware, in fact the malware directly triggers the "HPP" or "Execution Flow Hijack" protection of the products.
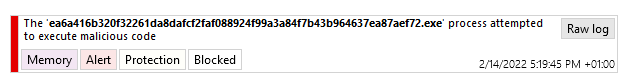
Figure 18: SES Evolution block log of CaddyWiper
IOCs
Sha256:
- a294620543334a721a2ae8eaaf9680a0786f4b9a216d75b55cfd28f39e9430ea
- b66b179eac03afafdc69f62c207819eceecfbf994c9efa464fda0d2ba44fe2d7
- ea6a416b320f32261da8dafcf2faf088924f99a3a84f7b43b964637ea87aef72
- 1e87e9b5ee7597bdce796490f3ee09211df48ba1d11f6e2f5b255f05cc0ba176
Breach Fighter Portal:
- breachfighter/ea6a416b320f32261da8dafcf2faf088924f99a3a84f7b43b964637ea87aef72
- breachfighter/b66b179eac03afafdc69f62c207819eceecfbf994c9efa464fda0d2ba44fe2d7
- breachfighter/1e87e9b5ee7597bdce796490f3ee09211df48ba1d11f6e2f5b255f05cc0ba176
- breachfighter/a294620543334a721a2ae8eaaf9680a0786f4b9a216d75b55cfd28f39e9430ea
