A critical authentication bypass vulnerability impacting the Next.js middleware has been reported. It has been assigned the reference CVE-2025-29927 and a CVSS 3.1 score of 9.1.
It should be noted that proof of concept are publicly available about this CVE-2025-29927 vulnerability.
Initial vector attack of the Next.js vulnerability
The vulnerability allows an unauthenticated attacker to bypass Next.js authorization mechanisms.
Technical details of the Next.js vulnerability
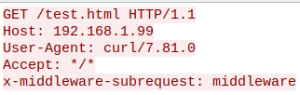
The vulnerability lies within an internal Next.js function which aims to prevent infinite middleware execution loops. If the HTTP header x-middleware-subrequest exists with a special value (depending on the Next.js version) the Next.js authorization functions are bypassed.
Affected versions:
- >= 11.1.4, <= 13.5.6
- >= 14.0, < 14.2.25
- >= 15.0, < 15.2.3
Attack modelling with MITRE ATT&CK
MITRE ATT&CK
- T1190 (Exploit Public-Facing Application)
How to protect against the Next.js vulnerability with Stormshield Network Security
Protection against CVE-2025-29927
Stormshield Network Security (SNS) firewalls detect and block exploitation of CVE-2025-29927 with the following IPS signature:
- http:client:header:259 : Exploitation of a Next.js middleware vulnerability (CVE-2025-29927)
For those protections to be efficient, the traffic must be decrypted.

Confidence index for the protection offered by Stormshield |
Confidence index for the absence of false positives |
Recommandations regarding the Next.js vulnerability
Update Next.js to the following version
- For Next.js 15.x, update to version 15.2.3;
- For Next.js 14.x, update to version 14.2.25;
- For Next.js 13.x, update to version 5.9;
- For Next.js 12.x, update to version 12.3.5;
- For other Next.js versions, we advise to disable the external usage of the
x-middleware-subrequestHTTP header through a reverse proxy.
