Vulnerabilities are continuing to appear at the end of September: CVE-2021-22005, a flaw in Microsoft Exchange and a new version of the StealBit malware. Here is an update on Stormshield protection.
CVE-2021-22005: a vulnerability in VMware telemetry
The telemetry of VMWare VCenter VSphere systems (v7.0 & v6.7) is vulnerable to an arbitrary file upload, on the server filesystem. This vulnerability can be used to execute malicious code on the Linux system.
Stormshield protects your virtual infrastructure from CVE-2021-22005 (CVSS 9.8) exploits on VMware and VCenter systems with the new SNS signature http:client:header.216. Please note that SSL proxy must be activated.
Protection confidence indicator
No false positive confidence indicator
StealBit malware: a variant to watch out for
StealBit 2.0 is a “stealers” family tool, used by Lockbit group to exfiltrate victim’s data to a Command & Control server. It starts after the exploit phase of the attack. To hide its activity from signature-based security solutions, the studied tool variant charge specific function through a non-official DLL call to network library.
Stormshield Endpoint Security Evolution solution is able, by default, to detect and block this kind of non-standard behavior before any damaged occurred. A protection built in the default policy since SES Evolution 2.1.0.
Protection confidence indicator
No false positive confidence indicator
Microsoft Exchange flaw: a critical misimplementation
The Autodiscover service of Microsoft Exchange is used to automatically connect a new client to the mail by sending credentials through a specific URL like autodiscover.example[.]com. If it fails, the back-off procedure suppresses the middle domain, the URL becomes autodiscover[.]com. But this domain is public and it can be bought by a malicious person who might then be able to receive credential of domain mail users.
Stormshield protects from this Microsoft Exchange Autodiscover vulnerability leak with the SNS signatures http:client:header.215 (please note that this one requires that SSL proxy must be activated) and ssl:client:sni.27 (that does not required SSL proxy).
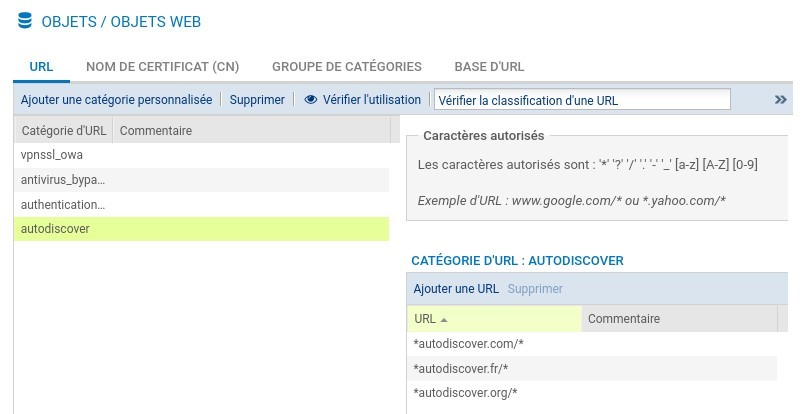
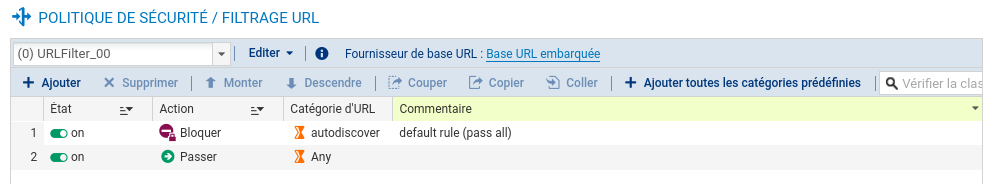
It is also possible to configure the SNS URL filtering to block autodiscover domains*:
- Create an autodiscover object with the extension of your domain (fr, eu...)
- Add this object to the URL filtering policy
- Enable the policy in http filtering (and https via proxy)
Protection confidence indicator
No false positive confidence indicator