Password stealers are well-known malware used in daily basis by cyber-criminals. Most of the time those stealers are delivered in ready to used package (builder + panel) with a readme or/and video tutorials. Those malware aim to steal credentials in all kinds of software, record keystrokes, grab sensitive files such as wallets, etc. During the end of 2017 we published a post talking about the unpacking and reverse engineering of Agent Tesla. However in this blog-post we will focus on the analysis of the infrastructure used by average crooks to spread Agent Tesla. We will also explain the hunting methodology to retrieve information on those cyber-criminals.
Agent Tesla
Agent Tesla is a well-known password stealer offering a lot of features. This malware is heavily used in the wild and mostly by script kiddies surely due to its low price ($49 for 6 months) and its user-friendly UI. The builder of Agent Tesla offers 3 types of communication to exfiltrate stolen credentials. Those methods are HTTP, SMTP, and FTP (see picture below).
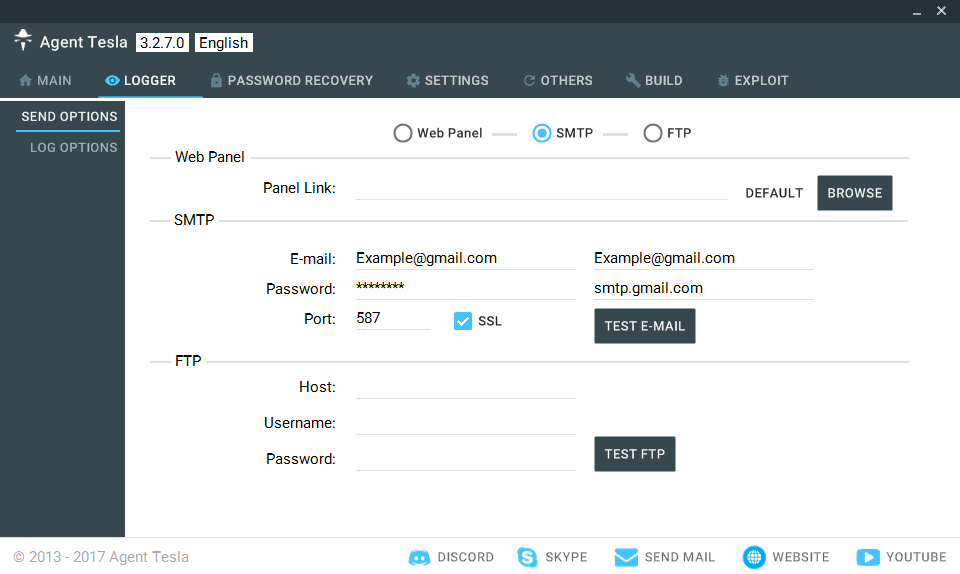
Analyzing the incoming samples in Breach Fighter (our sandboxing service), we saw that the most used protocols are HTTP followed by SMTP. The SMTP option is loved by skids because all you need is a working email address - no server, no configuration, etc. The downside of this feature is that if you have the sample you can get access to the mail account. For this reason in this blog post we will focus on the SMTP version.
During the research of new Agent Tesla samples we found 8674a053118790bc1bb11d188f517c95c2a5471ce2eca36129296f4783015bb8 which was at the moment active. We analyzed this sample because it uses SMTP and because the crooks behind this sample have pwned themselves. This infection can give us a better understanding of the infrastructure used by those criminals.
Information gathering
In this section we will discuss how we retrieved information on the crook to help us understand the infrastructure used to propagate malware.
Hybrid-Analysis
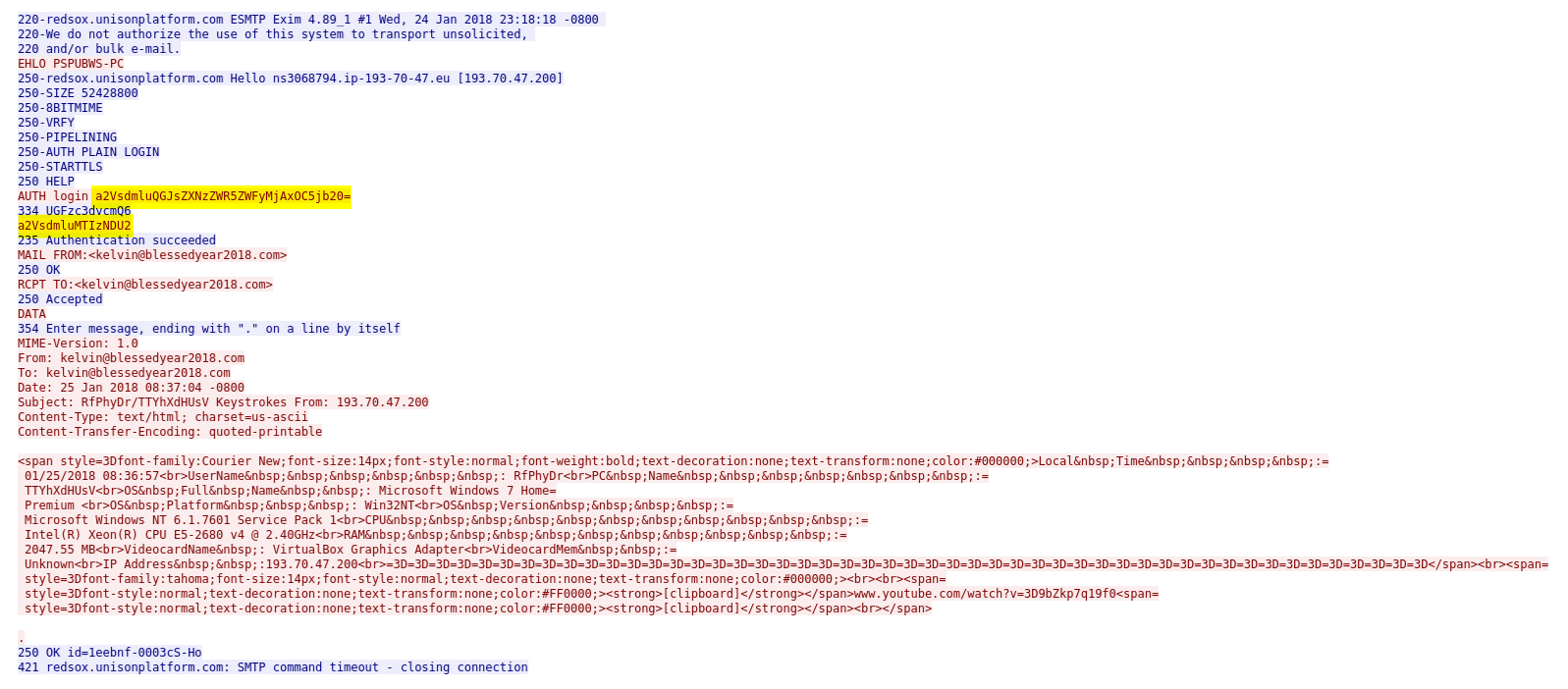
Analyzing the SMTP traffic from the PCAP of the sample on Hybrid-Analysis we can find the credential encoded in base64 (see highlights parts in the picture below) and the SMTP server. After decoding those strings we get the following credential login: kelvin@blessedyear2018.com, password: kelvin123456 .
Digging into mail
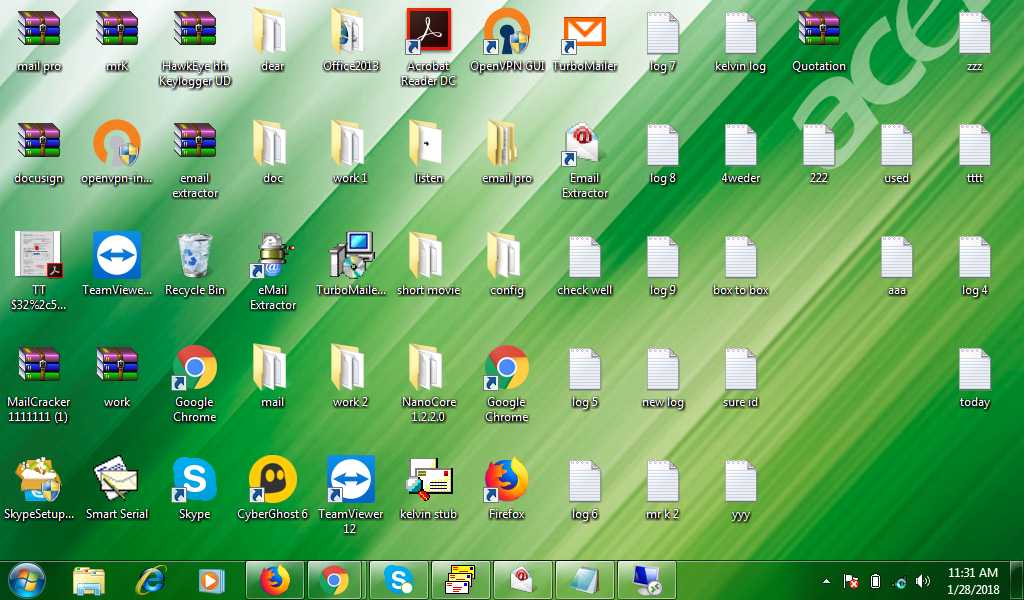
Once the credential retrieved, we found some screenshots of the crook took by Agent Tesla. As we can see below, there is some malware on the desktop (HawkEye, and NanoCore), but also some tools used by spammers such as Turbo Mailer.
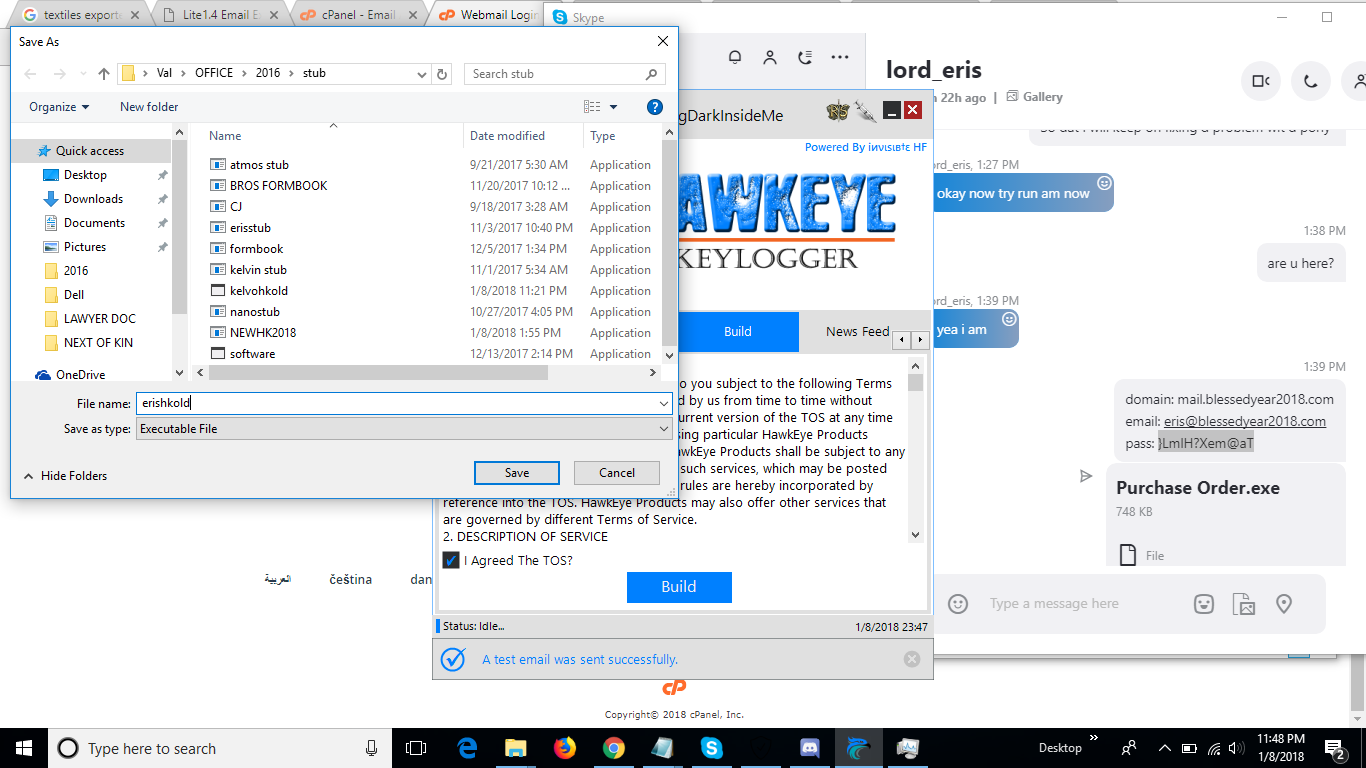
Another screenshot shows us the HawkEye builder with another mail account related to the blessedyear2018.com. The password given in the Skype conversation was wrong at the moment of the analysis. But, with some extremely sophisticated guessing (xD) we found the password which was eris123456 .
We can also see that all mail sent to kelvin@blessedyear2018.com are forwarded to mrkjonal@hotmail.com .
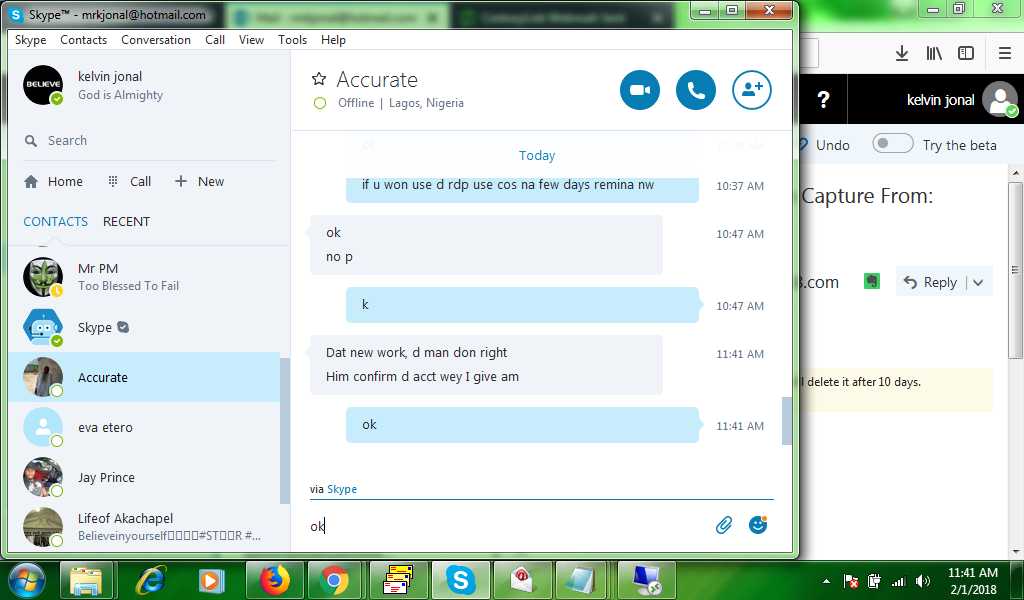
Like most of the crooks we've seen, they communicate with Skype or Jabber. Below is a discussion with another crook in "English".
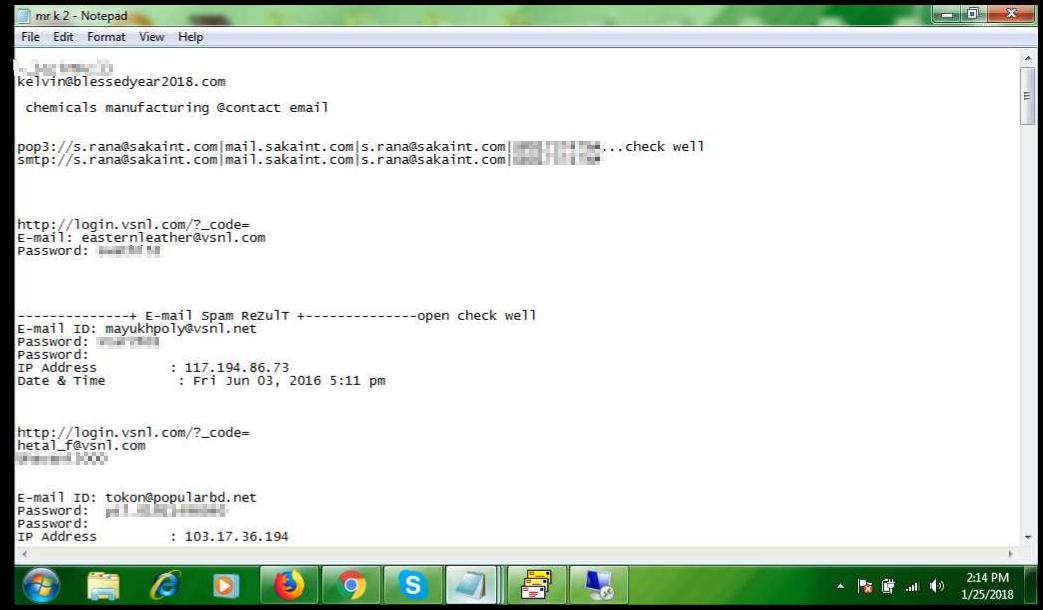
To send spam they use stolen credentials retrieved with Agent Tesla. In some cases (not this one) we also saw crooks buying their credentials, Cpanel, RDP, and emails on websites such as olux.to (tweet about this website), toolsbase.ws, and spammer.ro. Below is a notepad with stolen credentials used to send malware.
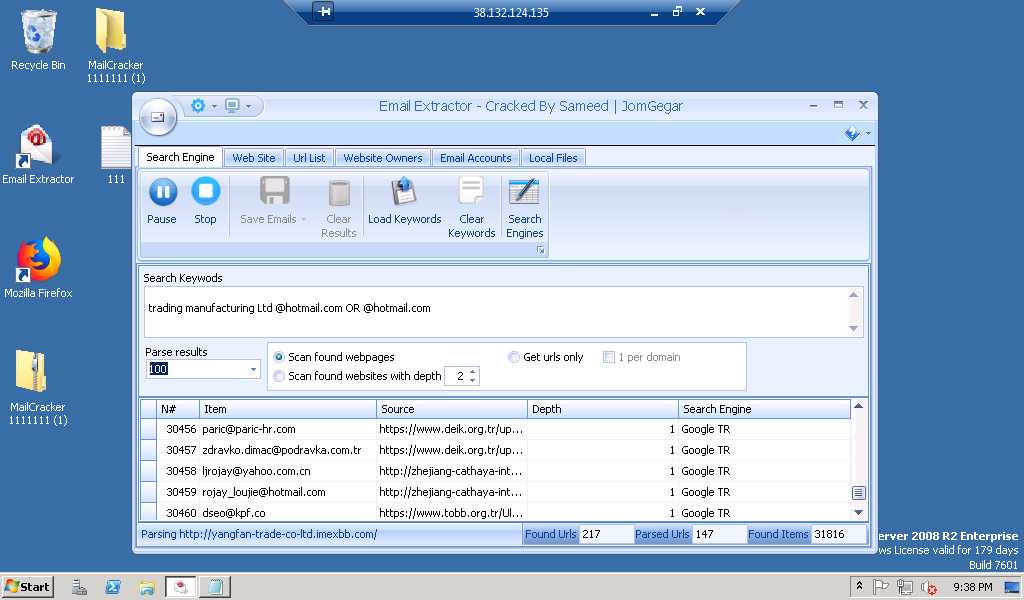
To find targets, they use a tool named Email Extractor Pro. This software allows the extraction of emails from various sources such as: files, websites, search engines, etc. Below we can see Email Extractor in action.
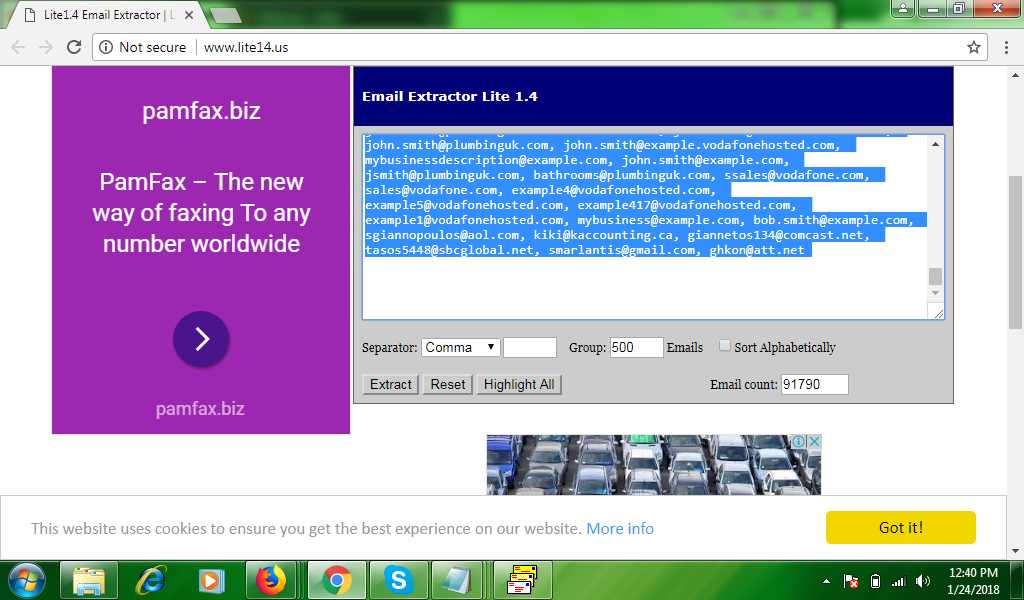
Then to clean their lists of targeted emails, and split them in chunks they use the website Email extractor Lite 1.4. The screenshot below shows that the crook wants to clean 91.790 emails separated by commas, and then split them in chunks of 500.
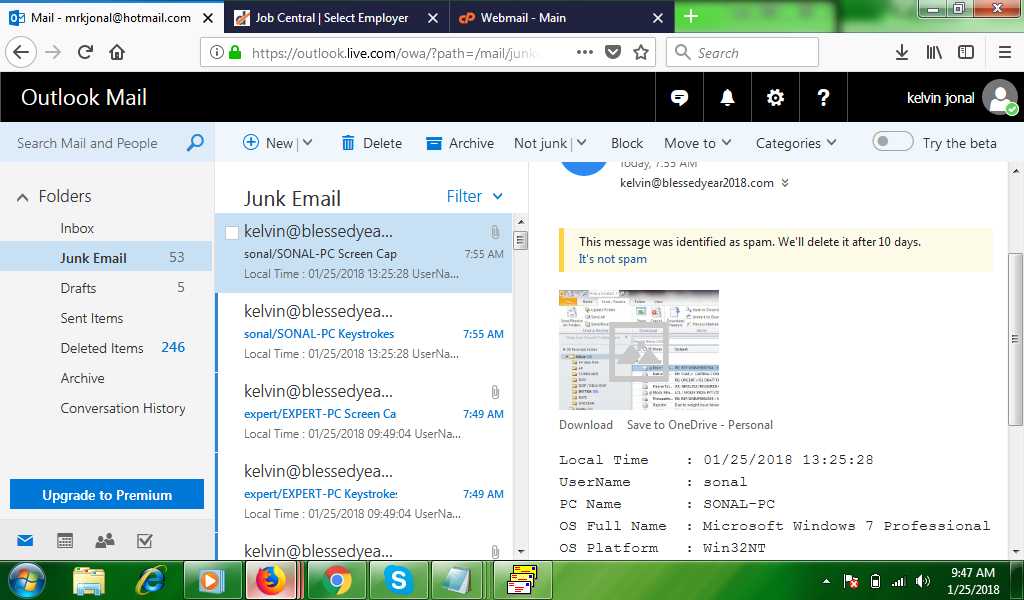
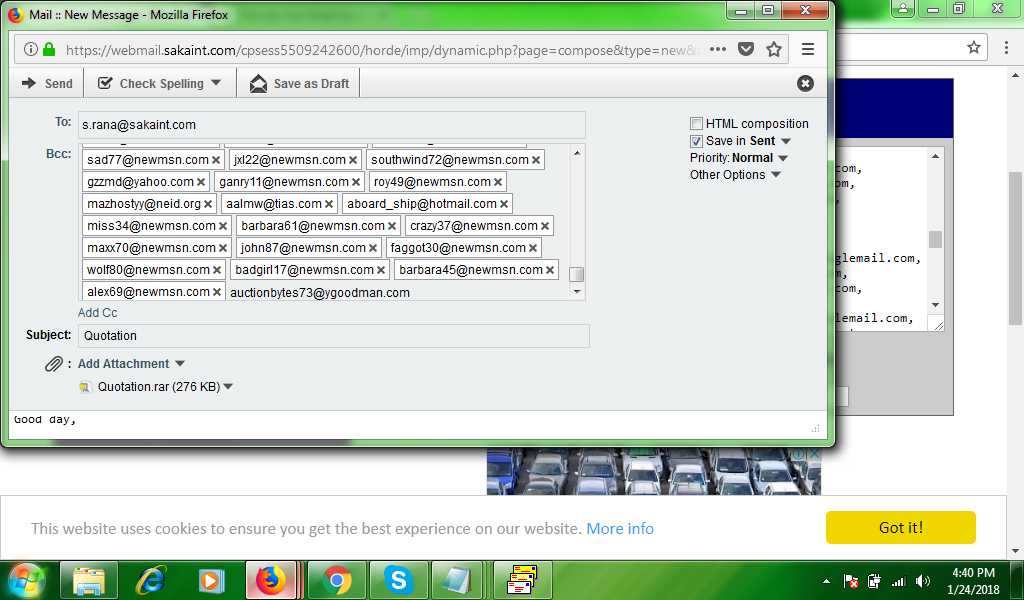
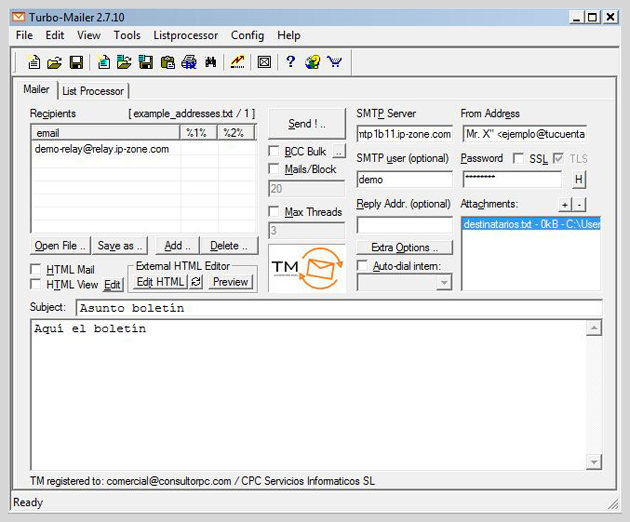
During the investigation we saw that they used two methods to send spam. They either send email "manually" via web-mails (See the first screenshot below). The other technique is using the tool Turbo-Mailer (we forgot to take a screenshot :/) which is a mass mailer.
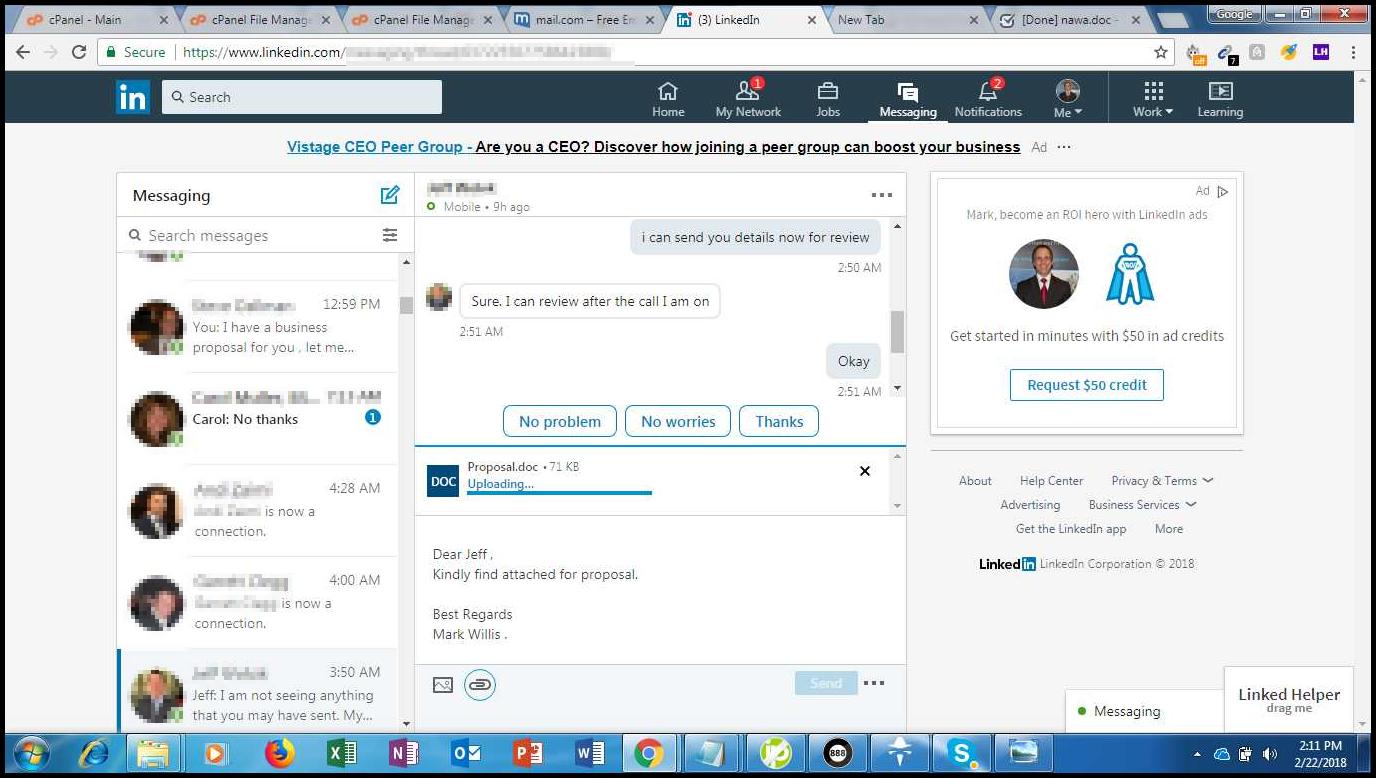
Those actors send simple phishing via mails, but in other cases we also saw some malware spreading via LinkedIn (see an example below).
As we have seen on different screenshots, the crooks use a Windows server via RDP. They mostly use it for Email Extractor and Turbo Mailer. Maybe it's used for the bandwidth. Digging into mail, we found a screenshot with the IP and a valid username for that server (see picture below).
Searching in mail of the bot master, we found a strange string which was always at the beginning of a long list of email addresses. This string looks like randomly generated Mono)Uq#4n%o7 . So, we guessed that was the password for the Windows server, and the list of addresses were fed to Turbo-Mailer. As we have expected, it was the right password and we could log in. On the server we searched into the browser history and we found a lot of connections to google domains. We also found new email addresses used by the crooks (see the screenshots below).
Conclusion
During this hunting we saw how shitty crooks organize themselves to find targets, send spams and retrieve stolen data. We can summarize the points seen previously below:
- They forward Agent Tesla mails to other actors
- They use Skype to communicate
- They use stolen credentials to send spam
- They use Email Extractor Pro to grab new email addresses.
- They use Lite 1.4 to split/extract mail
- They send spam manually or via Turbo Mailer
- They send spam with malware attached
This article does not present an extraordinary APTs but a casual malware, and crooks that infect thousand victims per day. If you want to know more about those mediocre scammers, I strongly recommend the @sS55752750 twitter account.
Fun Part
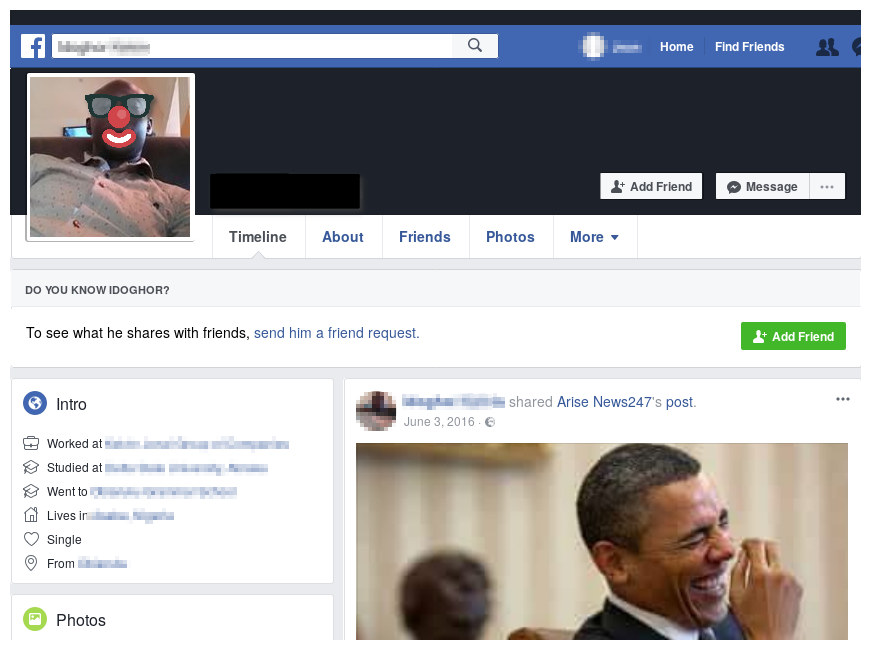
Last but not least, in this section we will see how easy it was to track the crooks behind this campaign. First of all, in the mail account used for the Agent Tesla we found some webcam snap (see picture below) of the crook (trying to understand how to remove AT :D).
We also found some screenshot of him surfing on Badoo and Facebook.
Finally, using this information above we found his Facebook profile. The information on his page seems coherent with the geographic location of his friends.
End of story.
IOCs
| Name | Sha256 | TimeStamp | HA Analysis date |
|---|---|---|---|
| PO-Specifications.exe | 8674a053118790bc1bb11d188f517c95c2a5471ce2eca36129296f4783015bb8 | 04/16/2017 | 01/25/2018 |
| Purchase Order-Drawings SPEC.exe | b11ca5106252eae5b71cc7c1e3abf85d491f1fc41e1112c095c3c18d28d67412 | 04/23/2017 | 01/31/2018 |
| Proforma Invoice.exe | c47cccb5faa1e2ab6c389dca58d8a81e7f971a7e9fdcfcf6a5dc938caa5b1070 | 04/25/2017 | 02/02/2018 |