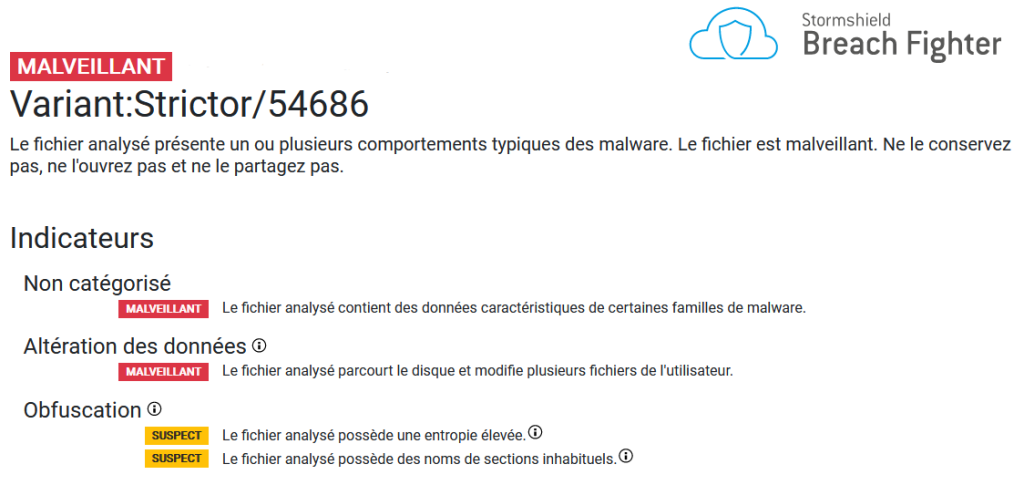
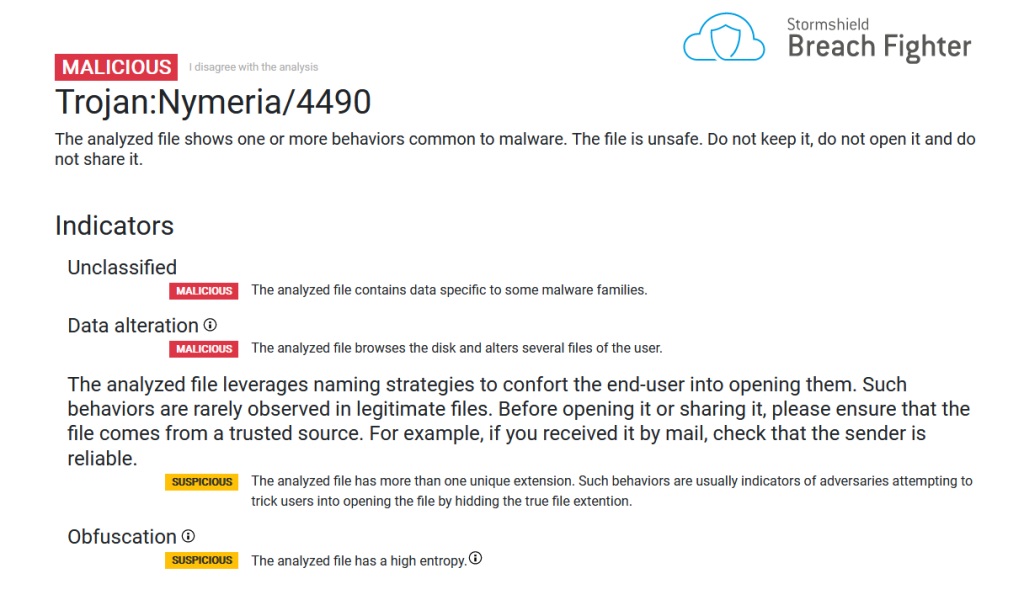
Following the detection by our partners of recent ransomware activity in Asia, Stormshield's Cyber Threat Intelligence team conducted an in-depth analysis of this sample. This malware is part of a family already identified by other cybersecurity players as "Crypt888", "Strictor", "Nymeria" and others. The return of this malware is an opportunity for Stormshield Customer Security Lab to provide the technical background to this ransomware attack.
We'll see in this article that "888" echoes a technical feature of the malware.
Initial vector of the ransomware attack Crypt888
We obtained two samples and analyzed them:
- 2e0f1385a0eb72f189c3d3cffa38020d71370ab621139c5688647c5bab6bc7f2
- ba2598fdd2e5c12e072fbe4c10fcdc6742bace92c0edba42ca4ca7bc195cb813
We have observed two forms of the initial phase of the attack: in the first, the file poses as an installer for the Google Chrome web browser, in the other it poses as a PDF document.
In the case of the Google Chrome browser installer, the malware takes the form of an executable with the Google Chrome icon.
In the case of the PDF document, the file is also an executable, but with a double extension. It is entitled "Academics.pdf.exe", but if the default settings are set to Windows session, the file explorer hides known file extensions (in this case, .exe). Visually, without notion of extension and a very suggestive icon, the user doesn't realize that he's dealing with an executable and not a PDF document.
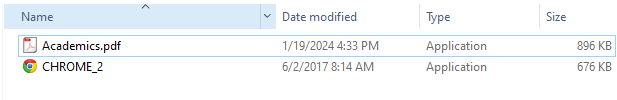
Figure 1 - Displaying samples in Windows Explorer
Apart from changing the name and icon, the attackers have made no particular effort to customize the samples used. Declarative file details (description, company or product name, etc.) are absent.
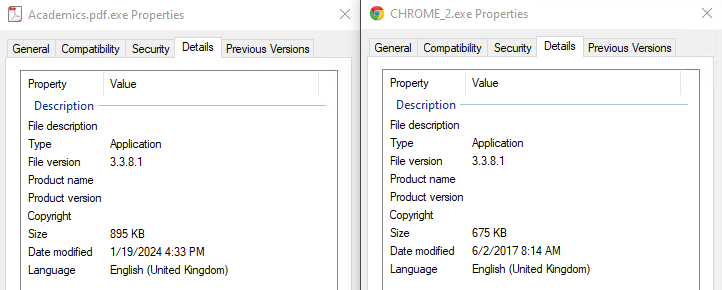
Figure 2 - File details for both samples
We do not have enough evidence to confirm how this malware is distributed on victims' computers. However, the intention to pass off the samples as legitimate executables makes distribution via phishing (PDF Document) and download sites (Software Installer) likely.
Languages and obfuscation of ransomware Crypt888
Apart from the icon and wallpaper, the two samples are identical, as their source codes are similar. For the sake of simplicity and readability in the rest of the analysis, we'll consider these two samples to be variants of the same malware, presented under the name of "Crypt888" ransomware.
The malware uses several layers of obfuscation. Basically, the logic is developed in the form of an AutoIT script, which has then been packaged to remove all constant values from the code (strings and numeric values).
The removed data is serialized and placed in a file distributed with the script. This script and all associated files are then compiled into an executable, which is packed by UPX.
Here's an extract from the AutoIT code. The comments are the values reconstructed from the appendix files:
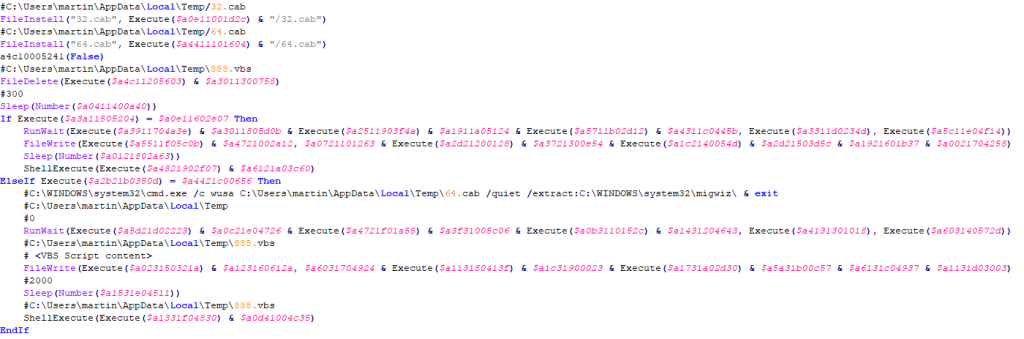
Figure 3 - Extract from the AutoIT code of one of the samples
Chronology of the ransomware attack Crypt888
The timeline in the quick version is as follows: the ransomware starts by disabling the UAC mechanism; it then encrypts files located in user and public folders with a fixed key; and finally, it initiates the display of the ransom demand via a wallpaper change.
The detailed chronology is much more complex, and is summarized in the image below.
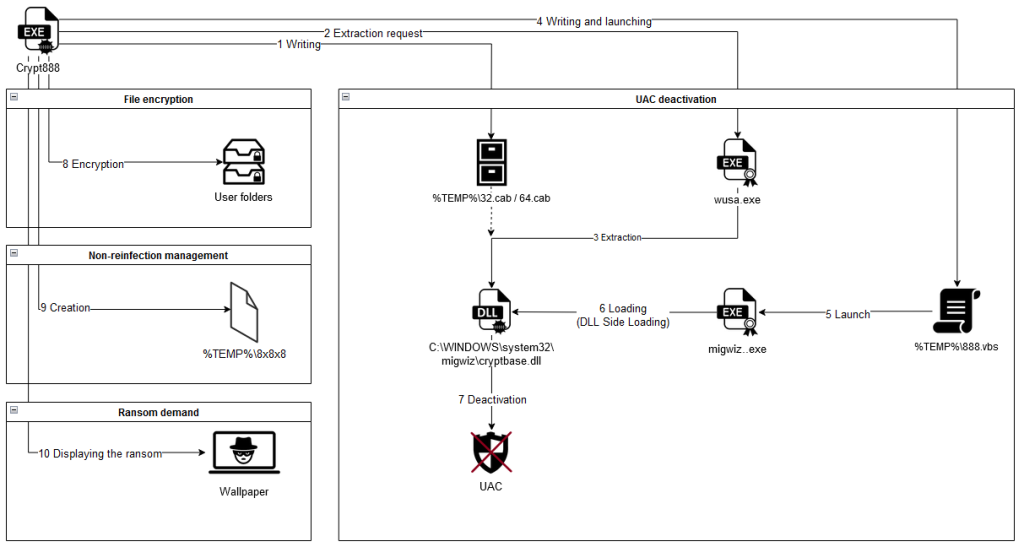
Figure 4 - Summary diagram of how the Crypt888’s attack works
The ransomware infection itself consists of four stages, which will be described in detail in the following dedicated paragraphs:
- UAC bypass via sideloading
- UAC deactivation
- File browsing and encryption
- Displaying the ransom note
UAC bypass via sideloading
Preparing sideloading
The ransomware begins by placing two CAB format archives (32.cab and 64.cab) in the current user's temporary folder: "C:\Users\<userName>\AppData\Local\Temp\".
These archives contain the 32-bit and 64-bit versions respectively of a DLL library named "cryptbase.dll". We'll see later that this DLL file contains malicious code. The malware then attempts to deploy the version corresponding to the processor architecture in the "C:\WINDOWS\system32\migwiz\" system folder.
At this point, the malware runs out of rights, but uses the "Microsoft Windows Update Standalone Installer" (wusa.exe) with the "/extract" parameter to avoid getting stuck. This command enables the contents of an archive to be placed in an arbitrary location without displaying the UAC warning window on a Windows system with the default configuration.
Note: The "wusa.exe" tool was introduced with Windows Vista and is used in the Windows update process. In response to various abuses, Microsoft has decided to remove the "/extract" parameter from versions supplied with Windows 10. This means that this malware only targets "older" Windows.
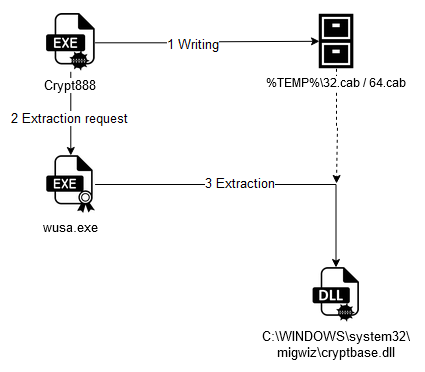
Figure 5 - Summary diagram of Side-Loading implementation
Triggering Side-Loading
The malware then deposits a VBS script named "888.vbs" in the user's temporary folder and executes it. The contents of the VBS script show a launch of the "migwiz.exe" utility with the following parameters:
Figure 6 - 888.vbs script content
The "migwiz.exe" program is a legitimate Microsoft tool for migrating data from one Windows workstation to another. It also features automatic UAC elevation, making it a potential candidate for UAC bypass attempts.
Malicious actions are not carried out directly by this program. For its operation, it needs to load the "cryptbase.dll" module, which, in the technical context of the attack, has been deposited by the malware in the "migwiz.exe" directory.
This malicious version of the module therefore takes priority and will be loaded instead of the official one supplied by Microsoft. The malicious code will therefore run in the context of this legitimate executable, which starts automatically with administrator rights.
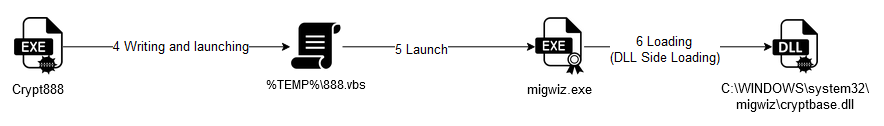
Figure 7 - Summary diagram of Side-Loading triggering
UAC deactivation
Once sideloading has been triggered, the malicious "cryptbase.dll" module deposited by the malware ensures that it is loaded by the "migwiz.exe" process. If it is, it executes the command given as a command-line parameter, thus enabling commands to be executed in the context of the "migwiz.exe" process, which benefits from UAC auto-elevation.
In the case of the attack chain, the command passed to "migwiz.exe" allows a particular value to be written to the registry, disabling the UAC mechanism on the system. In this way, if Crypt888 performs actions requiring privileges, they can be carried out directly without the user having to accept a validation message.
Note: On versions from Windows 8 onwards, this step no longer works, as "migwiz.exe" is no longer present by default. This again implies that this malware only targets "older" Windows.
File browsing and encryption
Targeted files
The initial Crypt888 executable seeks to encrypt all files located in the "Documents", "Pictures", "Videos", "Desktop" and "Music" sub-directories of the current user's folder and the folder shared between users: "Public".
Note: The samples studied are surprising in that they seek to acquire a higher level of privilege through UAC bypass, while the targeted files can be modified with the user's default rights.
File encryption
The files found are encrypted using a fixed key applied to the DES algorithm. Below is the content of a file before and after encryption:
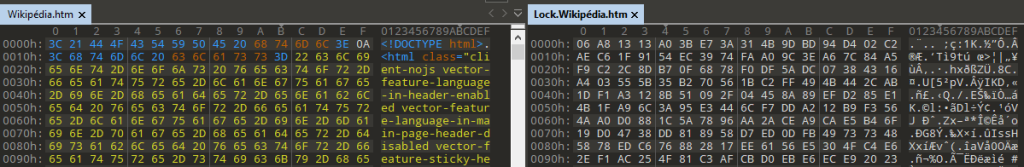
Figure 8 - File contents before and after encryption
Note: The DES encryption algorithm has been depreciated since the early 2000s, as it has become weak in comparison with computing power. We would have expected the ransomware to use a "stronger" encryption algorithm; this leads us to believe once again that it's not a very advanced one.
Renaming encrypted files
Once the data has been encrypted, the file name is prefixed with the string "Lock". It is therefore possible to decrypt altered files, since the encrypted files are clearly identifiable on the one hand, and the encryption algorithm is reversible and uses a fixed key on the other.
Here are the contents of a file before and after encryption:
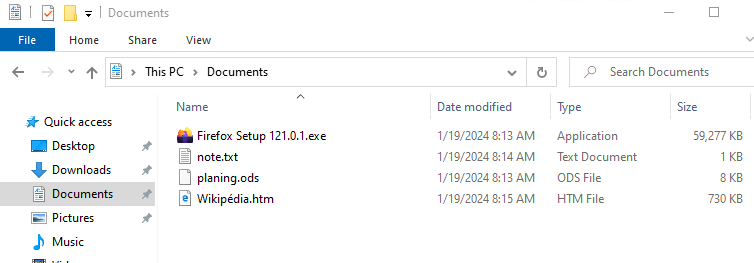
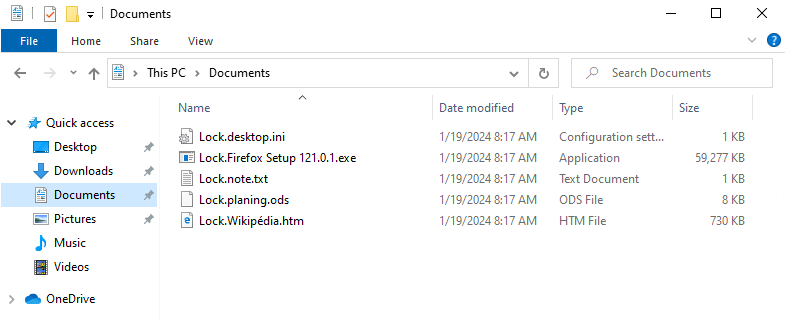
Figures 9 and 10 - Listing files before and after encryption
Displaying the ransom note
Here are the wallpapers configured by the two samples:
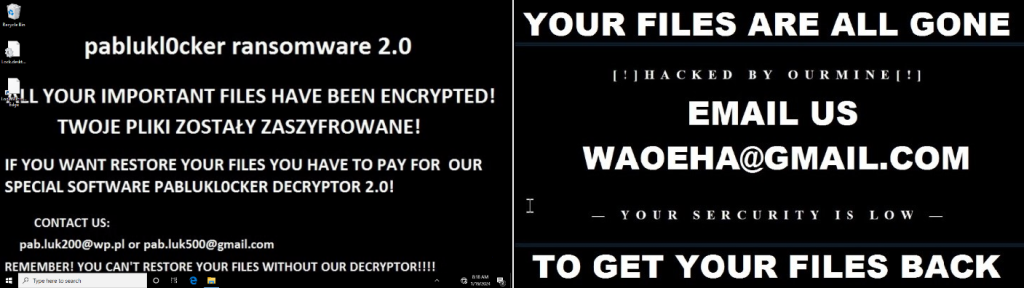
Figure 11 - Potential ransomware wallpapers
Note: One of the samples displays a ransom note, presenting itself as "Pablukl0cker" malware. An analysis of this malware has shown that it is not similar to the samples studied in this report. As we have no concrete evidence to know why these cybercriminals want to pass themselves off as someone else, several hypotheses are plausible like taking advantage of the notoriety of another cyber-criminal group, or giving false indications to mislead victims to avoid an effective reaction.
Synthesis and modeling of the ransomware attack Crypt888
In summary, "Crypt888" is a very simplistic ransomware targeting older versions of Windows (Vista and 7). The malware seems to have required few resources for its development, and motivations for use must surely lie in its simplicity of use, sobriety and effectiveness. For example, there's no need to maintain a C&C infrastructure to generate encryption keys. Although the ransomware is old in conception (the first traces of it can be found as far back as 2016), it still seems to be active in certain geographical regions, such as Southeast Asia.
There are several indications that little effort has been devoted to developing the ransomware:
- the encryption algorithm (DES) has been deprecated since the early 2000s;
- the developers have not maintained the malware to support Windows system evolutions over the years: disabling UAC therefore does not work on versions of Windows 8 and above;
- the design of the cryptographic system makes the data easy to decipher (fixed encryption key);
- no action is taken to disable the Shadow Copies mechanism (native Windows backups that restore files);
- the ransomware doesn't target other users' files or network shares, for example.
This ransomware is yet another example of how criminals are attracted by malware that is easy to use, requires no maintenance and very few technical skills. To develop and exploit the ransomware, cyber-criminals need few programming skills and none in system administration. In fact, no infrastructure costs are required to host the C&C server. What's more, the malware is easily reusable without owning the source code. It is therefore quite possible that cyber-criminal groups other than the developers will use the ransomware.
For further information, here's the MITRE kill chain implemented by the Crypt888 ransomware:
Here are the details of the Crypt888 ransomware's use of MITRE ATT&CK techniques:
IOC of ransomware Crypt888
In the course of our research, we came across other "initial samples" very similar to those analyzed in this article. Although we haven't studied them in detail, we'd like to mention them here.
- 130550cf5ec5ec37a4985b0fd3c66582d941c80e35e804e98a842dc5bef38c27
- 134516fee6594208afbe6c4fe9dec0926130afecd9f46e26989f202176cea01e
- 1480cc9e090d2edaf3de59b1b4e76a43c8f1fe40f66e73c5c6b9c91b69ba7a00
- 1585208cccb80adbaa116c96f0efae1ccfdbc0fe7d9cff97c9c5ba714d18fd92
- 15ba088d5cbc5a367f44e2a36beccee4ba90fec855c20e2b18adc889bd3b1bff
- 1850cae22f29cb94c33b33a2361ed7de3c4a94c42cb3b3bda69b2b26dbec3259
- 1aea04f6ca6974cbed14b9858dd6731b0d38d1313db23a38145dacdace725932
- 219789b31182abc8cbd83b5fee52d72f9a1bf20a38557c2d5b9a2aa96281e5de
- 234f4ac3322a8f958a20d7e68ea60a95732ede2d4b4050bb800d66a6b6c23636
- 2f8d4e1d4a358d31716fcb5f7bc8d00913708ac47e5607265b33d47b201fa58b
- 340aff7b8b16baa0878296d974b3a3114fb84dde6dd891bfe64adc8c12bd2cb5
- 35c278afce8c96e43d556ed58e82108cbef6253e52e6ffcb04edac695d1bafbf
- 3f0cc63d786e4f582a2bf200ac2fde5f44a3e095b5cf40a1a8dedcbe4fb1aded
- 4cdaecbad21f704af5cdfb089a88c2947ebe3dc4c6965f5d273533c6810162ea
- 53422a8efff6d48f7a985a6cb48b26035ca1cda53c40b1aeea1864270c324831
- 5574d56d513187f1c174c30f07c7d8b61d312cd0c303012e53a7877e0564bee8
- 5e0a2630d8bbc20de8b90ccd89389f8c01298b475fd8330738fe5519a6e01cfb
- 6410f220fdbd34dae565f5fba45e85107741c13d19a91b3126e735fbe0425606
- 642565dfff9850356709a6a094c169e1ee83cba56ac1bd92477e7de01e965ac3
- 6659bf0069dfeabc33ec7ac5ec0c50e5a8cf70aa10f4201a83b870aa6c115627
- 66bf9854472002fdfba5974f8fcba00b08b721c7241a1f0df06d18fd0858a387
- 6bfe111be2d46f80abf6eea2371059d8e5dbaa3cecdf9aaf242f23ef894869f3
- 6d8a15c8fdda25a9c1ac11028a93c0a6d95e1dd8327e7558a67bcf0ac39e2da6
- 70d76ed4d836413447756b708875881f2afcf1bf7a00609e8cd37fa04fff354e
- 72c83f54ef705cfd6ec86ac5e1a28810744670f6064c2b9a9501d5208b1d54b1
- 72dd91677f6f8e8d5587d4a9c684f46eda77ede9dfcf22c699af8651cb407d34
- 85f34cc8fe6247cfc13b3521a4678030a120f623bfc85bca186a8291a926d0b0
- 8b726e8f27d6241d914588a1bd39fb37cf4ba5b181ff013c083e71f0f1ee4ff9
- 82a576880faa9c4c5f017688ea414f54e10d7db78a83def90eb8a98c88c078cb
- 90dab08c9499bf6bbe9795116f9207d047283eccfee792894335b8ea1afbcac7
- 99ff99963727eac3b9766674faf1660348453c4509741be7d975f88a69a83331
- a046b579a3bcd7eb5e044bfa10161ca5ae78dc3ebd395244d3f764b179f4a827
- a1d09a7202623cbdb4278d980a522320be83ceb1f99d5f4ed87b4844fb8064a9
- aa74b00f92a43501e52e20a8c214dd2e9c3d86c14935b3cbb01e2a81fca2c9e3
- acc6114839d91d04b44de3f4483abcbbaeadb16294ce058348046f089bc65283
- acd106cb5ac9eb0ca722b3453c9641e536db573dbf5e6dc03591b5158b751a41
- b10a289269fea8392fae69aef57ed8fd7ed1faaec188bb4526927a37d99b22a8
- b19bf8d7c338fdbbf4c15cf91749796ed7d9bd6ff2bd39c0d8a1b9a439db0bf7
- bb243a3d07a96ff26c89496a9901c14772f235d0a678798f30faa389a25b1bb7
- cf7a2ca1077093ada33b15a0ed40067eee421e084d2fefb544d865352b1138d5
- d25176c86fdaa192fdf02abc04842f05c40bb7c0f6bfce8864f166031bd0ba32
- d7c797ecf5135e96cf7a6936ac5eb53d6cd39e019159789d6ba857f6285eaddb
- daa2b6c8201bd33d3bb871e2b94ec3beb4b4de471104082b0eafece5bd68ccc3
- dd99e24f05e4b1ffcfcc8823826fb098db7a3793b0c798f8fc195351812330f7
- e0c82339cbf535b0b30cef16dcb590cbdfe3898605776c6ca296070c5b11c9d9
- e3d2dd6e47f0b1b1f9b0816b83107c94d5fc46cc299e7dd9470610130bb8ce13
- e65d2f61b97db8f22a370b987ddc50fd26b1c95e1ec545c2777484796fbf942a
- ecf420df36237d9c0b360bbde960ddf398759a128f56f4a0ff8717f107741c8b
- ee372cd7a3457e169a7b8ebaabce843531d67c6f0c72cf17ec2fb7b292f43b4a
- f1648b93c9f1fd740aaf2e367284c6e23ecebe8238b9dfd50c06c2a664184ee7
- f582b4211193f0db6e45196677949425618306d270e47ac720cfe58a537147ff
- f59dc4c4dceb805f083b4aad13705e2a4dde67967e9dd29fa8bb6fce3e00b1f0
- d25176c86fdaa192fdf02abc04842f05c40bb7c0f6bfce8864f166031bd0ba32
- d7c797ecf5135e96cf7a6936ac5eb53d6cd39e019159789d6ba857f6285eaddb
- daa2b6c8201bd33d3bb871e2b94ec3beb4b4de471104082b0eafece5bd68ccc3
- dd99e24f05e4b1ffcfcc8823826fb098db7a3793b0c798f8fc195351812330f7
- e0c82339cbf535b0b30cef16dcb590cbdfe3898605776c6ca296070c5b11c9d9
- e3d2dd6e47f0b1b1f9b0816b83107c94d5fc46cc299e7dd9470610130bb8ce13
- e65d2f61b97db8f22a370b987ddc50fd26b1c95e1ec545c2777484796fbf942a
- ecf420df36237d9c0b360bbde960ddf398759a128f56f4a0ff8717f107741c8b
- ee372cd7a3457e169a7b8ebaabce843531d67c6f0c72cf17ec2fb7b292f43b4a
- f1648b93c9f1fd740aaf2e367284c6e23ecebe8238b9dfd50c06c2a664184ee7
- f582b4211193f0db6e45196677949425618306d270e47ac720cfe58a537147ff
- f59dc4c4dceb805f083b4aad13705e2a4dde67967e9dd29fa8bb6fce3e00b1f0
- dd99e24f05e4b1ffcfcc8823826fb098db7a3793b0c798f8fc195351812330f7
- e0c82339cbf535b0b30cef16dcb590cbdfe3898605776c6ca296070c5b11c9d9
- e3d2dd6e47f0b1b1f9b0816b83107c94d5fc46cc299e7dd9470610130bb8ce13
- e65d2f61b97db8f22a370b987ddc50fd26b1c95e1ec545c2777484796fbf942a
- ecf420df36237d9c0b360bbde960ddf398759a128f56f4a0ff8717f107741c8b
- ee372cd7a3457e169a7b8ebaabce843531d67c6f0c72cf17ec2fb7b292f43b4a
- f1648b93c9f1fd740aaf2e367284c6e23ecebe8238b9dfd50c06c2a664184ee7
- f582b4211193f0db6e45196677949425618306d270e47ac720cfe58a537147ff
- f59dc4c4dceb805f083b4aad13705e2a4dde67967e9dd29fa8bb6fce3e00b1f0
- ee372cd7a3457e169a7b8ebaabce843531d67c6f0c72cf17ec2fb7b292f43b4a
- f1648b93c9f1fd740aaf2e367284c6e23ecebe8238b9dfd50c06c2a664184ee7
- f582b4211193f0db6e45196677949425618306d270e47ac720cfe58a537147ff
- f59dc4c4dceb805f083b4aad13705e2a4dde67967e9dd29fa8bb6fce3e00b1f0
Protective measures Stormshield
Breach Fighter against ransomware Crypt888
The Breach Fighter sandboxing service, available as an option in Stormshield Network Security firewalls (on the SMTP/HTTP/FTP flow) and also as an API, detects and blocks malware.

Confidence index for Stormshield protection |
Confidence index of absence of false positives |
Stormshield Network Security against ransomware Crypt888
Stormshield Network Security firewalls cannot detect malware activity, as it does not carry out any network communication. They can, however, detect malware transport with the Advanced Antivirus option, even without the presence of the Breach Fighter option.
Detection signatures are "AIT:Trojan.Nymeria.4490" and "Gen:Variant.Strictor.54686".

Confidence index for Stormshield protection |
Confidence index of absence of false positives |
Stormshield Endpoint Security Evolution against ransomware Crypt888
The SES Evolution solution, equipped with v2403a security policies, is able to detect and block malware as it runs, even before encryption begins.

Confidence index for Stormshield protection |
Confidence index of absence of false positives |
Recommendations for dealing with ransomware Crypt888
Other applicable recommendations:
- keep your operating systems up-to-date;
- if you have not already done so, please apply the most recent version of SES Evolution policies (currently v2403a);
- in the event of infection, seek professional assistance if your teams are unable to deal with the incident.