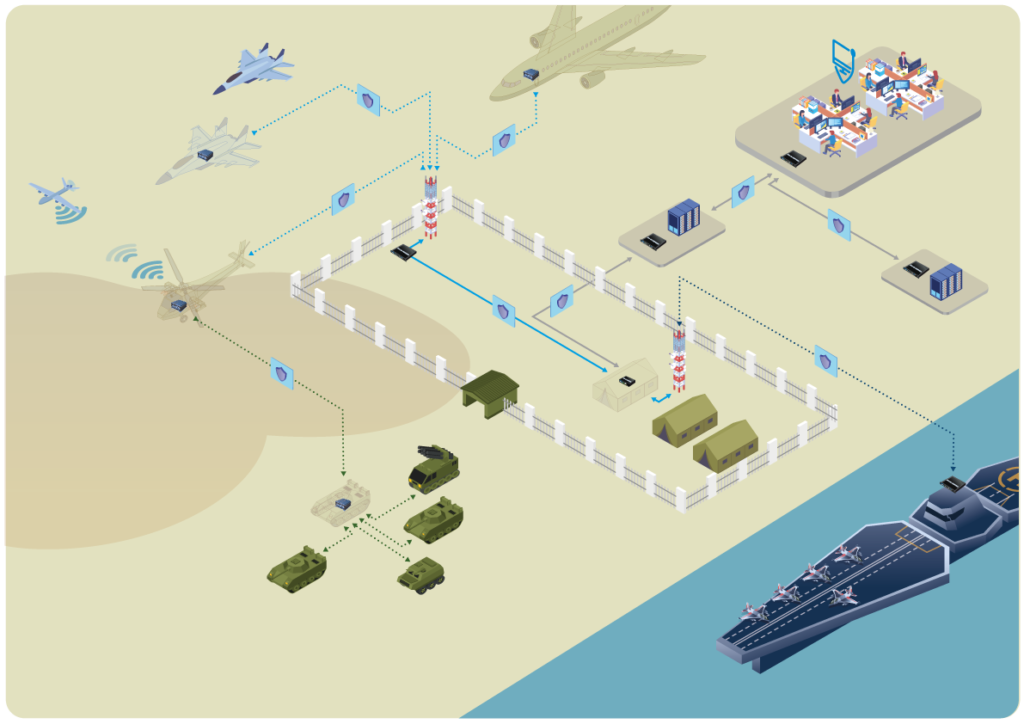
Military organizations, defense ministries, and armed forces need especially powerful protection for their information systems. In the modern era, cyberwarfare plays a crucial role in national security – and the best offense is an unshakeable defense. Security, reliability and availability are therefore of the utmost importance when the stakes are so high.
Cyber-Defence: choosing trusted products
The defence sector must have guarantees regarding the quality of security products. The standards and certifications offered by independent bodies provide assurance that the products chosen are trustworthy and certified by third parties. That is why our cybersecurity products are regularly certified and qualified, in other words recognised as trustworthy products by the French government and by all European countries that have ratified the mutual recognition agreement (SOG-IS).
Our Stormshield products have a bunch of labels for protecting sensitive NATO info: ANSSI Standard qualification in France, ‘Producto Aprobado’ and ‘Producto Cualificado’ qualifications from the CCN in Spain, Common Criteria EAL4+, Restricted Distribution (DR), NATO Restricted, EU Restricted and TEMPEST assessment (recognised as SDIP-27 Level B by NATO and classified as Zone 1 equipment by ANSSI). This level of reliability is unique and guarantees that you are choosing products with the highest level of security while benefiting from the functional developments offered by a key player in the cybersecurity market.
Ensure the highest level protection
Losing confidential data or information is not an option in the Defense sector and military organizations. Applications and communications, especially confidential communications, are protected through strong, vital encryption.
Stormshield Network Security
The intrusion prevention system (IPS) in Stormshield Network Security (SNS) products combine behavioral and protocol analysis to ensure effective, proactive protection against attacks, especially zero-day attacks. Our EAL3+ and EAL4+ certified technology is among the most powerful on the market and was designed to guarantee the highest level of security and performance.
Stormshield Endpoint Security
Switch to a better workstation protection technology with Stormshield Endpoint Security (SES) behavioral analysis. Working within the operating system, our tool intercepts and analyses all commands in order to detect unusual behavior that might exploit flaws in applications. Since it does not use a signature database, it is particularly effective for non-connected environments. Stormshield Endpoint Security provides smart protection against both known and unknown attacks, regardless of their level of sophistication.
Stormshield Data Security
Encrypting sensitive information at its source helps prevent confidential data from leaking or being stolen. This certified product guarantees a level of encryption that meets the strictest standards. Its end user-centered approach makes it easy to use, thus limiting the potential to bypass the security system. Stormshield Data Security’s (SDS) certified encryption solution is compatible with all third party applications so as to facilitate integrating the encryption of your data into your business applications.
SNxr1200: an encryption firewall adapted to heavy constraints
Discover our network security product extra-ruggedized, designed to be embedded in vehicles operating in critical environments for extreme aeronautical, space and military missions.

Combining compliance and cybersecurity
Because military organisations, ministries of defence and armed forces require particularly strong protection for their information systems, all these organisations must comply with a number of cyber rules and standards. In addition to the national level, these organisations must comply with European cybersecurity regulations such as the NIS and NIS2, the GDPR, the Cybersecurity Act or the NATO Restricted Classification. Other standards (e.g. Common Criteria EAL3+ & EAL4+ or ISO/IEC 27000 series) are not mandatory under current legislation but help to improve the level of cyber security of defence organisations.
Stormshield products help organisations comply with these requirements by improving the cyber resilience of their infrastructure. For example, Stormshield Network Security and Stormshield Data Security have been awarded NATO Restricted Distribution. These solutions can therefore be deployed in sensitive environments to encrypt information classified as NATO Restricted, and to enable secure transmission of classified information. For more information on Stormshield's compliance with Defence cyber regulations, contact our teams!
Easily integrate our products into your existing structure
Implementing a security product in an existing environment can be a tedious process: the product must be flexible and have an adaptable network layer so that it can fit into your architecture without causing downtime.
Our solution Stormshield Network Security (SNS) is adjustable and integrates seamlessly into your existing infrastructure to ensure you spend more time on what matters to your organization. Whether in routed, transparent, or hybrid mode, you choose how you want to use our equipment. The network layer can be adjusted for integration with any complex architecture. Built-in routing features adapt easily to other previously installed equipment as well.
Centralize for simplified management
The growing need for multiple network security solutions and equipment can greatly complicate administrative tasks. Our centralized administration solution Stormshield Management Center (SMC) simplifies the management of your entire IT system and the delegating of rights for borderline cases. Centralized management helps limit the time you spend managing remote equipment by giving you a single console. It also enables you to efficiently manage all of your Stormshield products.
Manage the protection of your communications
Setting up encrypted networks is often required for an optimal exchange of secure information. Do you need mobility or site-to-site connections? Based on technology that is certified at the highest level, the IPSec VPN and SSL VPN modules provide you with complete protection thanks to unbreakable encryption of data flowing through secure tunnels. Aligned with the ANSSI's IPSec Restricted Diffusion (DR) standard, the IPSec module is particularly well suited to protecting sensitive communications.
Whether your certification authority is internal or external, our PKI certificate management module ensures that digital certificate enrollment and tracking is a simple, centralized process. With this module, you get to take advantage of high-performance authentication and comprehensive management of user rights.
Benefit from services dedicated to Cyber Defence
Do you have specific requirements regarding your organization’s security constraints, such as securing configuration exchanges? Stormshield offers sensitive markets specific services to perform secure exchanges (without going back to using hard disks), deploy secure configurations using a USB drive, automatically update equipment that is not directly connected to the Internet via Stormshield’s offline update system.
Any other questions about your military cyber security? About your IT security? For all your other military and cyber defence requirements, our Stormshield expert teams are at your disposal.

